CPIM-8.0 APICS Certified in Planning and Inventory Management (CPIM 8.0) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your APICS CPIM-8.0 Certified in Planning and Inventory Management (CPIM 8.0) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following threats MUST be included while conducting threat modeling for a Cloud Service Provider (CSP)?
An organization has network services in a data center that are provisioned only for internal use, and staff at offices and staff working from home both use the services to store sensitive customer data. The organization does not want the Internet Protocol (IP) address of the service to receive traffic from users not related to the organization. Which technology is MOST useful to the organization in protecting this network?
Which of the following should Business Impact Analysis (BIA) reports always include?
Which of the following statements characterizes a pull system In distribution management?
Which of the following is the BEST type of fire extinguisher for a data center environment?
A newly hired Chief Information Security Officer (CISO) is now responsible to build a third-party assurance for their organization. When assessing a third-party, which of the following questions needs to be answered?
A security specialist is responsible to improve the security awareness program of a medium-sized organization and tasked to track blocked targeted attacks. Which of the following BEST describes the outcome of the security specialist’s use of metrics for this task?
In an organization that develops aircrafts for military usage, where will the security team focus its efforts to ensure the organization’s data remains confidential?
When an organization is recruiting for roles within the organization, at which stage of the employee life cycle are termination procedures incorporated?
One of the most useful tools for analyzing the sustainable footprint is:
Which of the following MUST exist for an activity to be considered an audit?
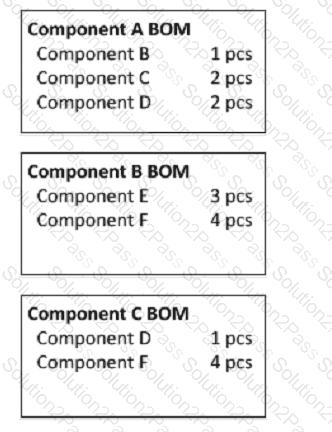
Given the bill of material (BOM) information below and independent requirements of 10 pieces (pcs) per week of Component A and 20 pieces (pcs) per week of Component B, what is the weekly gross requirement of component F?
The costs provided in the table below are associated with buying a quantity larger than immediately needed. What Is the total landed cost based on this table?
Cost CategoryCost
Custom fees$125
Freight$700
Warehouse rent$200
Matenal cost$500
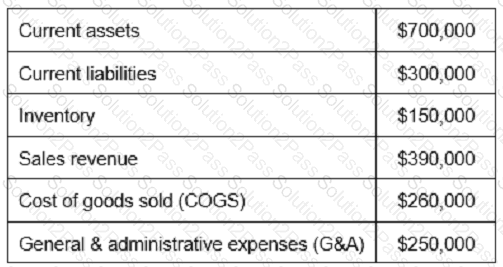
Based on the values reported in the table below, what is the inventory turnover?
What is the MAIN purpose of risk and impact analysis?
A part is sold as a service part, and It is also used as a component In another part. Which of the following statements about the planning for this part is true?
When a third-party needs to receive privileged information, which of the following would be the BEST to
transport the data?
An example of a cradle-to-cradle sustainability model would be:
The master schedule is an Important tool in the sales and operations planning (S&OP) process because it:
When resolving conflicts, which canon within the ISC2 Code of Ethics requires members to consider duties to principals and Individuals?
An organization experienced multiple compromises of endpoints, leading to breaches of systems and data. In updating its strategy to defend against these threats, which of the following BEST considers the organization’s needs?
A systems engineer has been tasked by management to provide a recommendation with a prioritized, focused set of actions to help the organization stop high-risk cyber attacks and ensure data security. What should the systems engineer recommend the organization use to accomplish this?
Which of the following product design approaches are likely to reduce time to market for a global supply chain?
An information security auditor is creating an audit program to assess endpoint security controls for portable storage media movement. Which type of control will MOST likely be part of the program?
A new organization building is being designed and the security manager has been asked for input on needed security requirements. Which of the following controls are MOST applicable to this scenario?
An organization is looking to integrate security concepts into the code development process early in development to detect issues before the software is launched. Which advantage does the organization gain from using Static Application Security Testing (SAST) techniques versus dynamic application security testing techniques?
A life cycle assessment (LCA) would be used to determine:
In a rapidly changing business environment, a primary advantage of an effective customer relationship management (CRM) program is:
In which of the following circumstances is an organization MOST likely to report the accidental release of personal data to the European Union (EU) General Data Protection Regulation (GDPR) supervisory authority and affected users?
The primary purpose for engaging in cycle count activities is to:
