A30-327 AccessData Certified Examiner Free Practice Exam Questions (2025 Updated)
Prepare effectively for your AccessData A30-327 AccessData Certified Examiner certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which Registry Viewer function would allow you to automatically document multiple
unknown user names?
Which type of evidence can be added to FTK Imager?
When previewing a physical drive on a local machine with FTK Imager, which statement is true?
Click the Exhibit button.
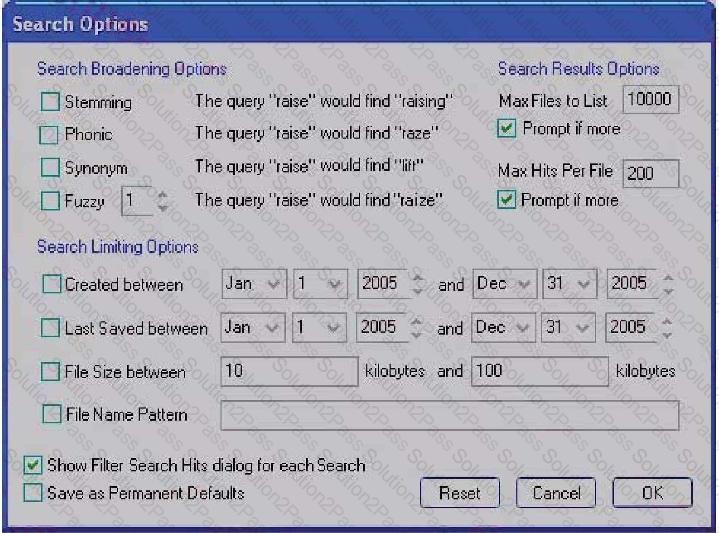
You need to search for specific data that are located in a Microsoft Word document. You do not know the exact spelling of this datA. Using the Index Search Options as displayed in the exhibit, which changes do you make in the Broadening Options and Search Limiting Options containers?
In FTK, when you view the Total File Items container (rather than the Actual Files container), why are there more items than files?
In FTK, which search broadening option allows you to find grammatical variations of the word "kill" such as "killer," "killed," and "killing"?
You view a registry file in Registry Viewer. You want to create a report, which includes items that you have marked "Add to Report." Which Registry Viewer option accomplishes this task?
How can you use FTK Imager to obtain registry files from a live system?
Which three items are displayed in FTK Imager for an individual file in the Properties
window? (Choose three.)
When using Registry Viewer to view a key with 20 values, what option can be used to display only 5 of the 20 values in a report?
FTK Imager allows a user to convert a Raw (dd) image into which two formats? (Choose two.)
Which data in the Registry can the Registry Viewer translate for the user? (Choose three.)
While analyzing unallocated space, you locate what appears to be a 64-bit Windows date and
time. Which FTK Imager feature allows you display the information as a date and time?
During the execution of a search warrant, you image a suspect drive using FTK Imager and store the Raw(dd) image files on a portable drive. Later, these files are transferred to a server for storage. How do you verify that the information stored on the server is unaltered?
What is the purpose of the Golden Dictionary?
Click the Exhibit button.
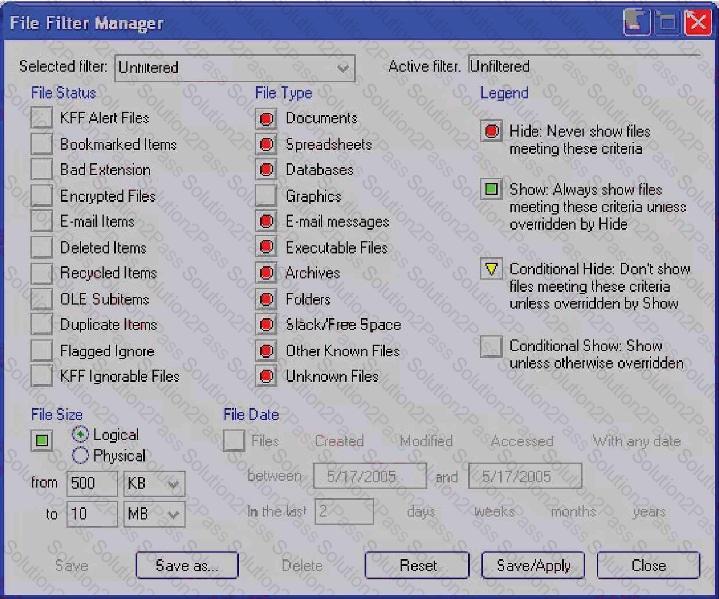
What change do you make to the file filter shown in the exhibit in order to show only graphics with a logical size between 500 kilobytes and 10 megabytes?
In FTK, which two formats can be used to export an E-mail message? (Choose two.)
Click the Exhibit button.
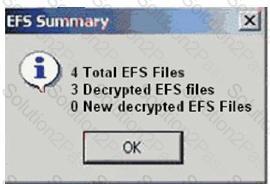
When decrypting EFS files in a case, you receive the result shown in the exhibit. What is the most plausible explanation for this result?
