1D0-571 CIW v5 Security Essentials Free Practice Exam Questions (2025 Updated)
Prepare effectively for your CIW 1D0-571 CIW v5 Security Essentials certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You have been assigned to provide security measures for your office's reception area. Although the company needs to provide security measures, costs must be kept to a minimum. Which of the following tools is the most appropriate choice?
What is the primary use of hash (one-way) encryption in networking?
Which of the following can help you authoritatively trace a network flooding attack?
Which of the following is the primary weakness of symmetric-key encryption?
You have determined that the company Web server has several vulnerabilities, including a buffer overflow that has resulted in an attack. The Web server uses PHP and has direct connections to an Oracle database server. It also uses many CGI scripts. Which of the following is the most effective way to respond to this attack?
A security breach has occurred involving the company e-commerce server. Customer credit card data has been released to unauthorized third parties. Which of the following lists the appropriate parties to inform?
Which of the following errors most commonly occurs when responding to a security breach?
You have just deployed an application that uses hash-based checksums to monitor changes in the configuration scripts of a database server that is accessible via the Internet. Which of the following is a primary concern for this solution?
Which of the following is a primary auditing activity?
Consider the following diagram:
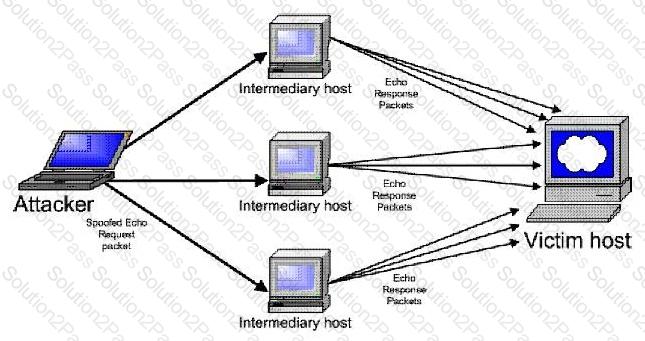
Which type of attack is occurring?
What is the primary strength of symmetric-key encryption?
You have implemented a version of the Kerberos protocol for your network. What service does Kerberos primarily offer?
At what layer of the OSI/RM does a packet filter operate?
A distributed denial-of-service (DDOS) attack has occurred where both ICMP and TCP packets have crashed the company's Web server. Which of the following techniques will best help reduce the severity of this attack?
Which of the following is most likely to pose a security threat to a Web server?
You are creating an information security policy for your company. Which of the following activities will help you focus on creating policies for the most important resources?
Consider the following image of a packet capture:
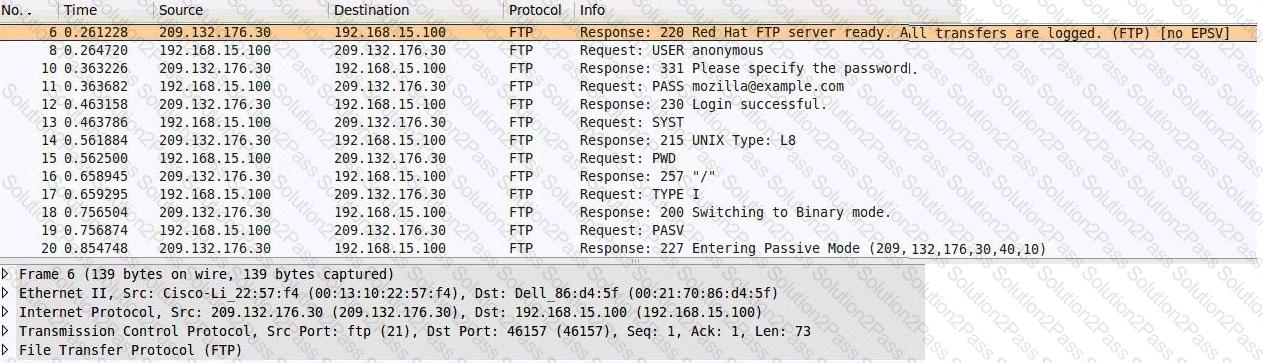
Which of the following best describes the protocol used, along with its primary benefit?
You want to create a certificate for use in a Secure Sockets Layer (SSL) session. Which of the following is responsible for verifying the identity of an individual and also issuing the certificate?
