156-215.81 Checkpoint Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Checkpoint 156-215.81 Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the main difference between Threat Extraction and Threat Emulation?
Which Check Point software blade monitors Check Point devices and provides a picture of network and security performance?
What is the default shell for the Gaia command line interface?
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
An administrator can use section titles to more easily navigate between large rule bases. Which of these statements is FALSE?
Which icon in the WebUI indicates that read/write access is enabled?
You want to store the GAiA configuration in a file for later reference. What command should you use?
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.
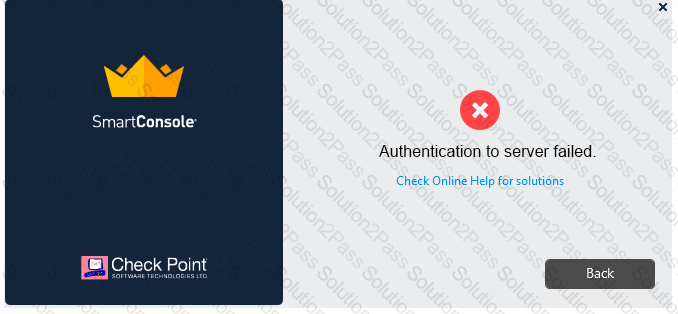
What is the most likely reason?
Where is the “Hit Count” feature enabled or disabled in SmartConsole?
To view statistics on detected threats, which Threat Tool would an administrator use?
By default, which port does the WebUI listen on?
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
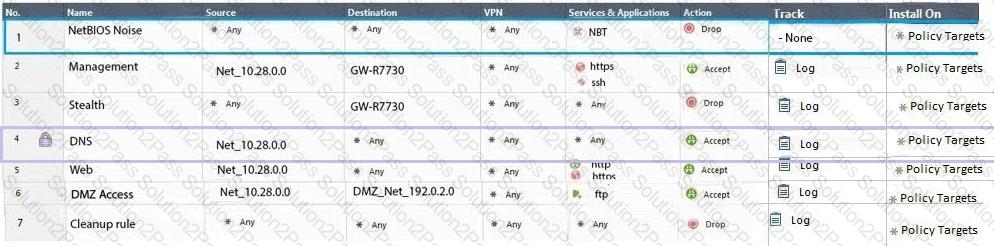
What is the possible explanation for this?
Which of the following describes how Threat Extraction functions?
Which is NOT an encryption algorithm that can be used in an IPSEC Security Association (Phase 2)?
Which command shows the installed licenses?
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
Which of the following is NOT a tracking log option in R80.x?
Identity Awareness allows the Security Administrator to configure network access based on which of the following?
When an Admin logs into SmartConsole and sees a lock icon on a gateway object and cannot edit that object, what does that indicate?
What is the purpose of a Clean-up Rule?
