156-315.81 Checkpoint Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Checkpoint 156-315.81 Check Point Certified Security Expert R81.20 ( 156-315.81.20 ) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Automation and Orchestration differ in that:
What are the blades of Threat Prevention?
When simulating a problem on ClusterXL cluster with cphaprob –d STOP -s problem -t 0 register, to initiate a failover on an active cluster member, what command allows you remove the problematic state?
NO: 180
What command can you use to have cpinfo display all installed hotfixes?
John detected high load on sync interface. Which is most recommended solution?
You find one of your cluster gateways showing “Down” when you run the “cphaprob stat” command. You then run the “clusterXL_admin up” on the down member but unfortunately the member continues to show down. What command do you run to determine the cause?
You have existing dbedit scripts from R77. Can you use them with R81.20?
Which command shows detailed information about VPN tunnels?
Using Threat Emulation technologies, what is the best way to block .exe and .bat file types?
Where do you create and modify the Mobile Access policy in R81?
Which one of the following is true about Threat Extraction?
Can multiple administrators connect to a Security Management Server at the same time?
John is using Management HA. Which Smartcenter should be connected to for making changes?
SandBlast has several functional components that work together to ensure that attacks are prevented in real-time. Which the following is NOT part of the SandBlast component?
In SmartEvent, what are the different types of automatic reactions that the administrator can configure?
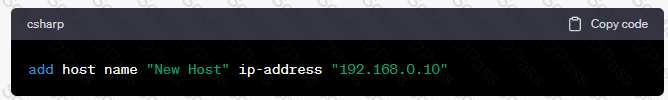
What API command below creates a new host with the name “New Host” and IP address of “192.168.0.10”?
Which of the following links will take you to the SmartView web application?
Which web services protocol is used to communicate to the Check Point R81 Identity Awareness Web API?
Which Check Point software blades could be enforced under Threat Prevention profile using Check Point R81.20 SmartConsole application?
: 131
Which command is used to display status information for various components?
What command lists all interfaces using Multi-Queue?
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
Fill in the blank: The R81 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows then as prioritized security events.
In ClusterXL Load Sharing Multicast Mode:
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
What is the order of NAT priorities?
After the initial installation on Check Point appliance, you notice that the Management-interface and default gateway are incorrect.
Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
You notice that your firewall is under a DDoS attack and would like to enable the Penalty Box feature, which command you use?
What key is used to save the current CPView page in a filename format cpview_”cpview process ID”.cap”number of captures”?
Which SmartConsole tab is used to monitor network and security performance?