100-160 Cisco Certified Support Technician (CCST) Cybersecurity Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 100-160 Cisco Certified Support Technician (CCST) Cybersecurity certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
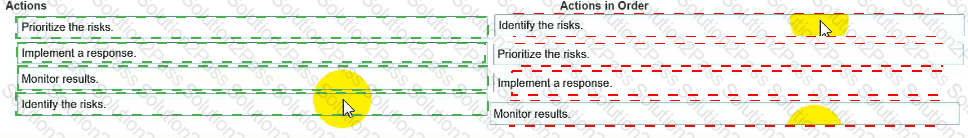
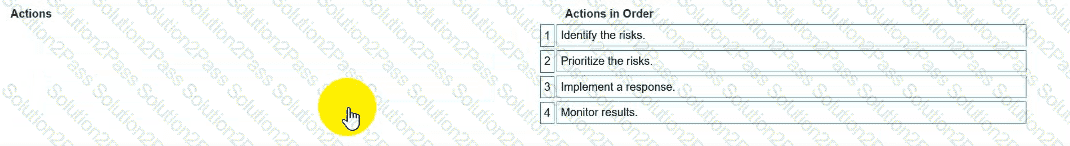
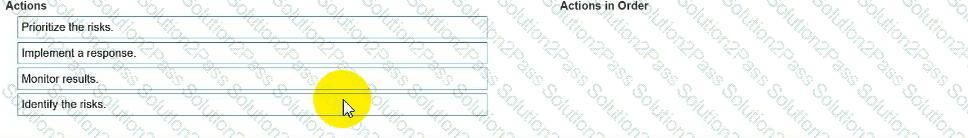
You need to manage security risks at your company. In which order should you complete the actions?
Move all the actions to the answer area and place them in the correct order.
Which data type is protected through hard disk encryption?
Which two passwords follow strong password policy guidelines?(Choose 2.)
An administrator wants to ensure that any files downloaded from the internet are automatically scanned for malicious code before execution. Which security control should be implemented?
Which Windows app is a command-line interface that includes a sophisticated scripting language used to automate Windows tasks?
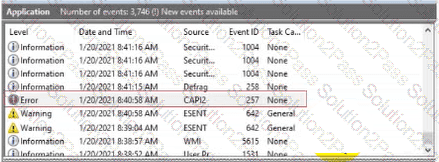
You are reviewing the Application log on a Windows computer. You see an event with an error-level message as shown.
What can you determine about the application that generated the event message?
You are reviewing your company’s disaster recovery plan.
Which two daily data backup actions should the plan include?(Choose 2.)
During an incident response, the security team needs to isolate a compromised server from the rest of the network but still allow forensic analysis. Which action should they take?
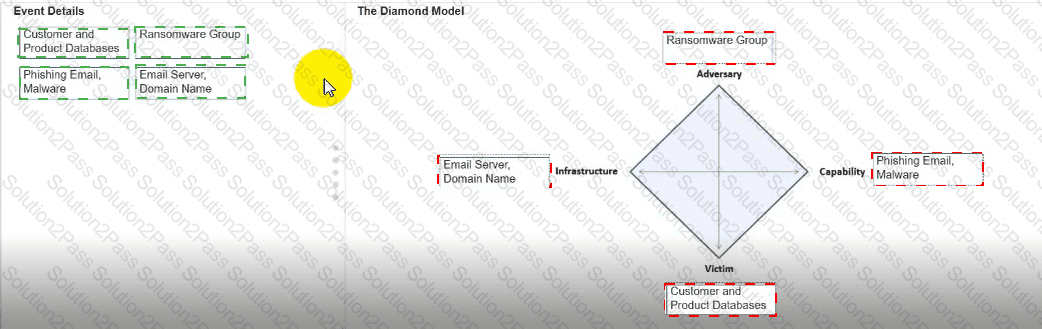
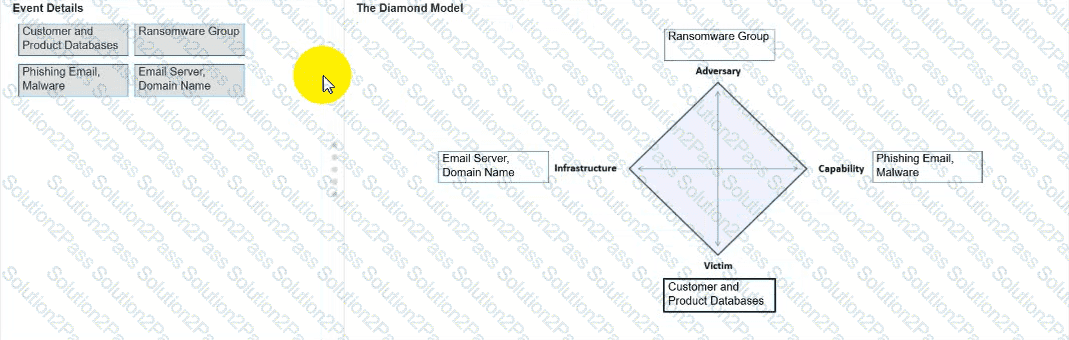
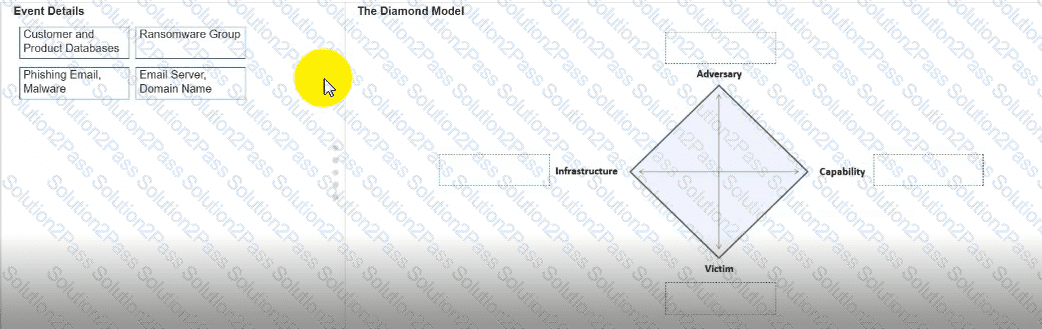
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
Move each worm mitigation step from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.

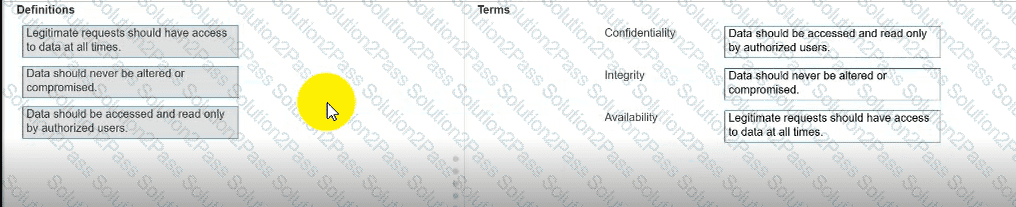
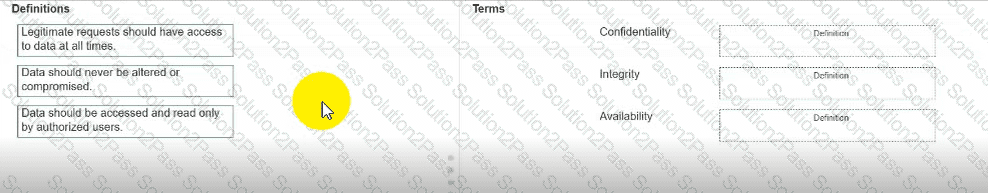
Move each definition from the list on the left to the correct CIA Triad term on the right.
Note: You will receive partial credit for each correct answer.
What is the main purpose of a disaster recovery plan as compared to a business continuity plan?
You notice that a new CVE has been shared to an email group that you belong to.
What should you do first with the CVE?
Which security assessment of IT systems verifies that PII data is available, accurate, confidential, and accessible only by authorized users?
Which step should be performed immediately after identifying a critical vulnerability affecting internet-facing systems?