300-220 Cisco Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-220 Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A SOC analyst is usingCisco Secure Network Analytics (Stealthwatch)to hunt for command-and-control (C2) activity across the enterprise. The analyst wants to identify stealthy C2 channels that intentionally avoid known malicious IP addresses and domains. Which Stealthwatch hunting approach BEST supports this objective?
A threat hunter is asked to model how an attacker could abuse cloud identity misconfigurations to escalate privileges without exploiting software vulnerabilities. Which modeling approach BEST supports this analysis?
Which hunting technique is MOST effective for detecting stealthy data exfiltration over standard web protocols?
A security team wants to create a plan to protect companies from lateral movement attacks. The team already implemented detection alerts for pass-the-hash and pass-the-ticket techniques. Which two components must be monitored to hunt for lateral movement attacks on endpoints? (Choose two.)
A Cisco-focused SOC wants to move detection coverage higher on thePyramid of Pain. Which hunting outcome BEST supports this objective?
During multiple investigations using Cisco telemetry, analysts observe attackers consistently perform internal discovery before privilege escalation and avoid high-risk actions. Why is this observation useful for attribution?
Refer to the exhibit.
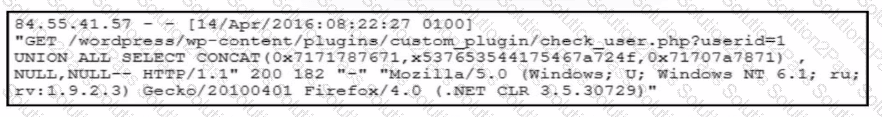
A forensic team must investigate how the company website was defaced. The team isolates the web server, clones the disk, and analyzes the logs. Which technique was used by the attacker initially to access the website?
A threat hunter completes a structured hunt and confirms malicious lateral movement within the environment. Which action BEST ensures the hunt contributes to long-term defensive improvement?
The security team detects an alert regarding a potentially malicious file namedFinancial_Data_526280622.pdfdownloaded by a user. Upon reviewing SIEM logs and Cisco Secure Endpoint, the team confirms that the file was obtained from an untrusted website. The hash analysis of the file returns an unknown status. Which action must be done next?
A SOC team must prepare for a new phishing campaign that tricks users into clicking a malicious URL to download a file. When the file executes, it creates a Windows process that harvests user credentials. The team must configure the SIEM tool to receive an alert if a suspicious process is detected. Which two rules must the team create in the SIEM tool? (Choose two.)
A threat hunter wants to detect credential dumping attempts that bypass traditional malware detection. Which telemetry source is MOST effective for this purpose?
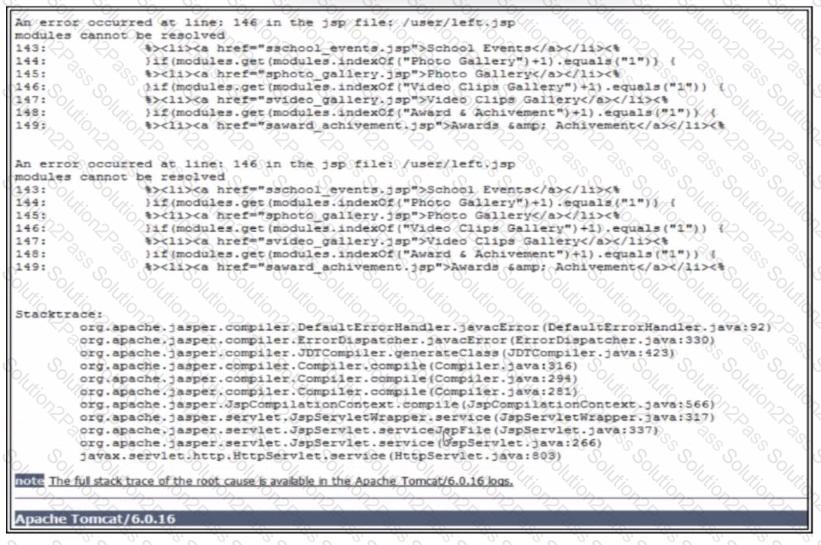
Refer to the exhibit. A penetration test performed against a web application generates the error message. Which two pieces of information are exposed? (Choose two.) Q Internal paths of the web server
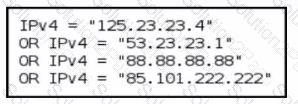
Refer to the exhibit.
A threat-hunting team makes an EDR query to detect possible C2 outbound communication across all endpoints. Which level of the Pyramid of Pain is being used?

Refer to the exhibit. Which technique is used by the attacker?
A mature SOC notices that several incidents over the past year involved attackers abusing legitimate administrative tools rather than deploying custom malware. Leadership asks the threat hunting team to improve detection coverage in a way that increases attacker cost rather than relying on easily replaceable indicators. Which detection strategy best aligns with this objective?
A SOC manager wants to evaluate whether the organization’s Cisco-based threat hunting program is improving over time. Which metric BEST reflects increased threat hunting effectiveness?
A structured threat hunt using Cisco Secure Network Analytics confirms abnormal internal SMB traffic consistent with lateral movement. Which action should occur NEXT to improve organizational security posture?
A SOC team using Cisco security technologies wants to distinguishIndicators of Attack (IOAs)fromIndicators of Compromise (IOCs)during threat hunting. Which scenario BEST represents an IOA rather than an IOC?
