300-410 Cisco Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-410 Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
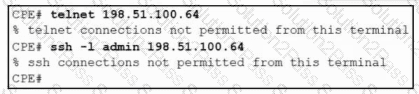
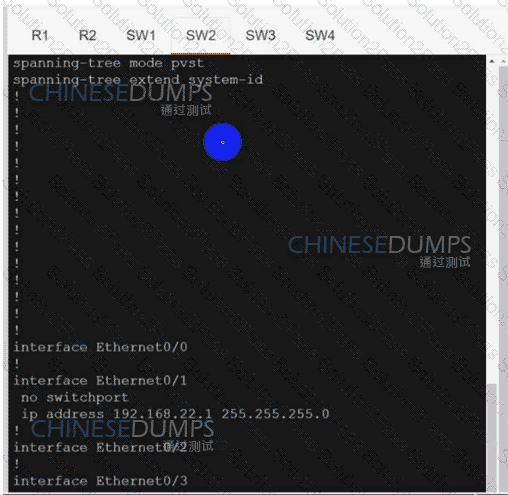
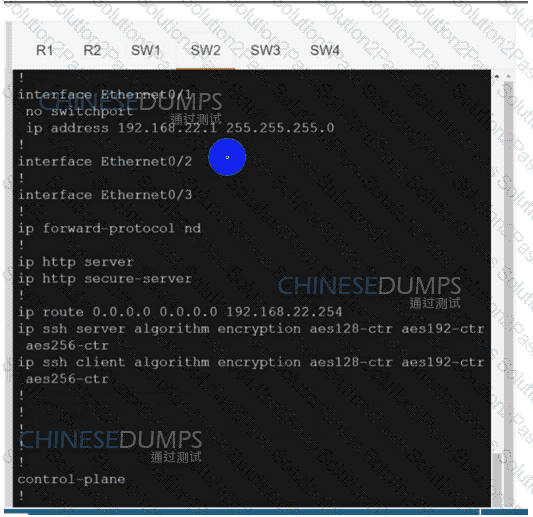
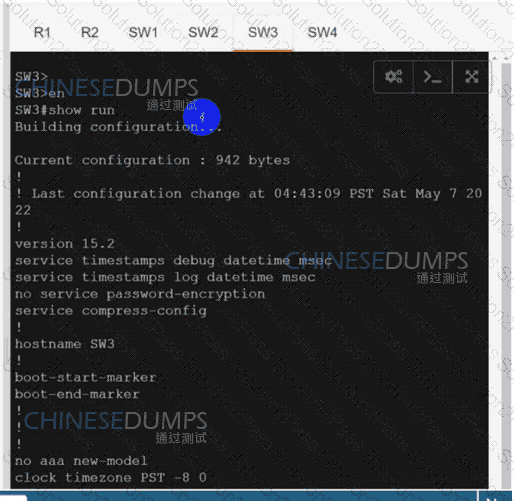
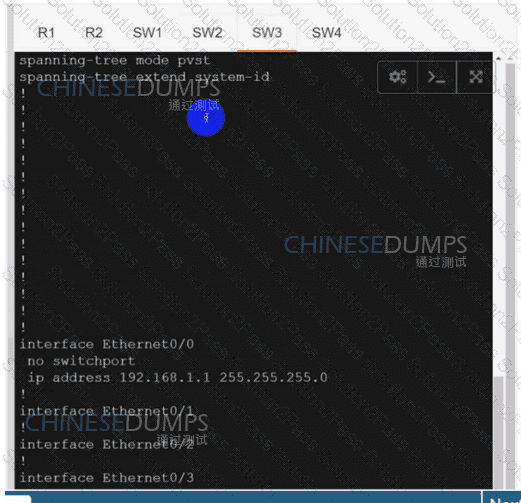
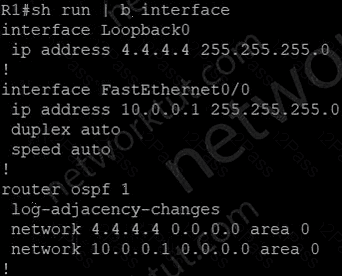
Refer to the exhibit. After a security hardening was performed on a router, the administrator cannot access the command line of any remote device. Which action resolves the issue?
Refer to the exhibit.
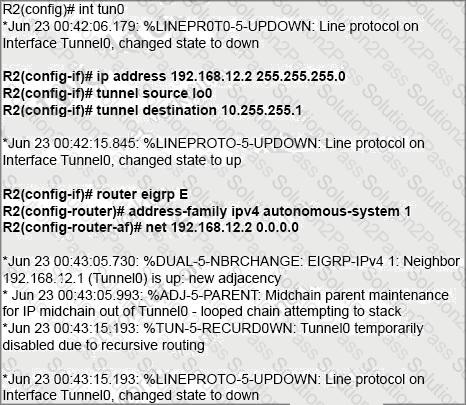
An administrator is configuring a GRE tunnel to establish an EIGRP neighbor to a remote router. The
other tunnel endpoint is already configured. After applying the configuration as shown, the tunnel
started flapping. Which action resolves the issue?
Refer to the exhibit. An engineer is trying to log in to R1 via R3 loopback address. Which action resolves the issue?
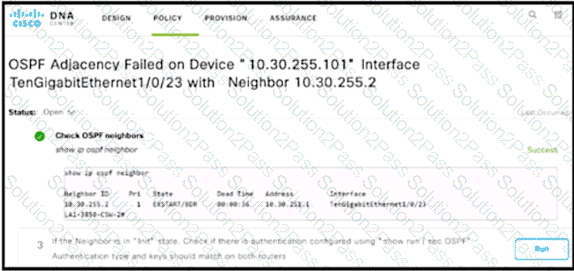
Refer to the exhibit. An engineer is investigating an OSPF issue reported by the Cisco DNA Assurance Center. Which action resolves the issue?
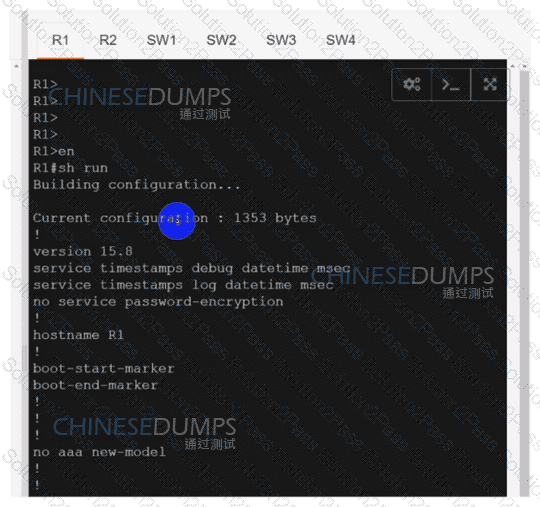
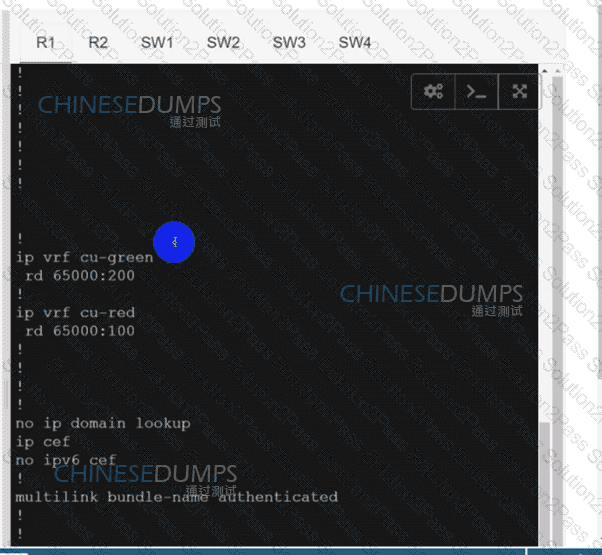
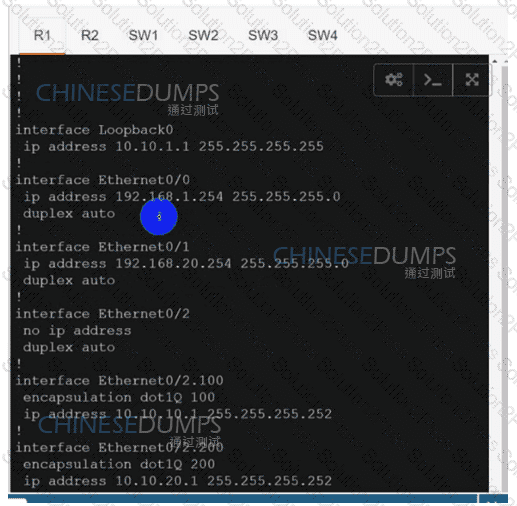
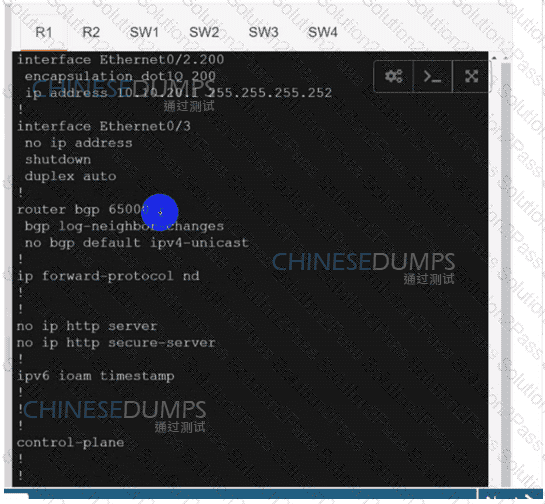
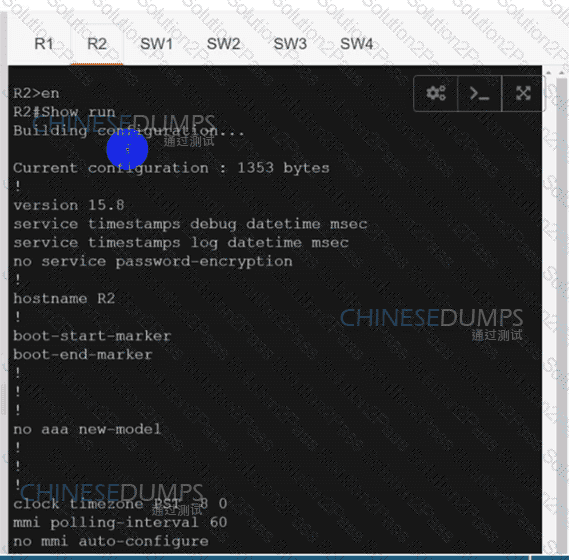
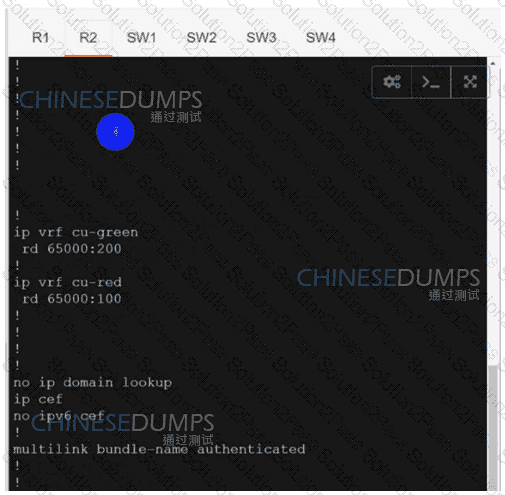
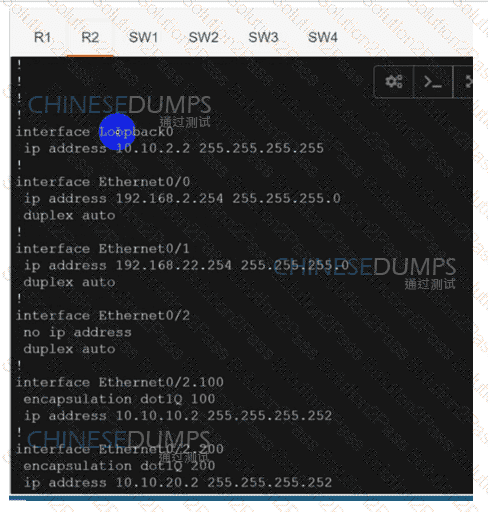
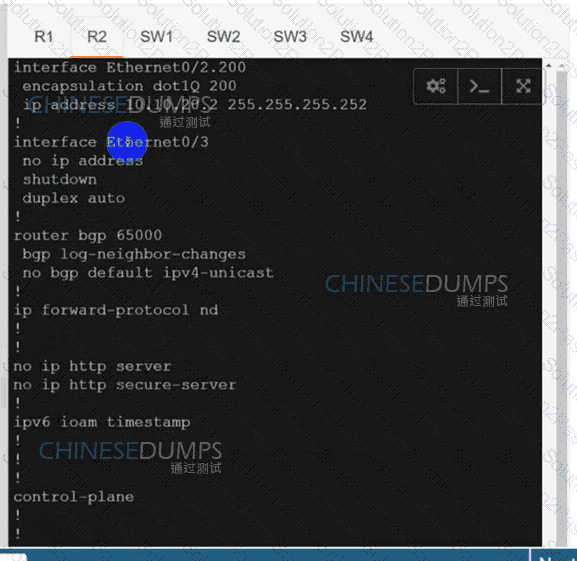
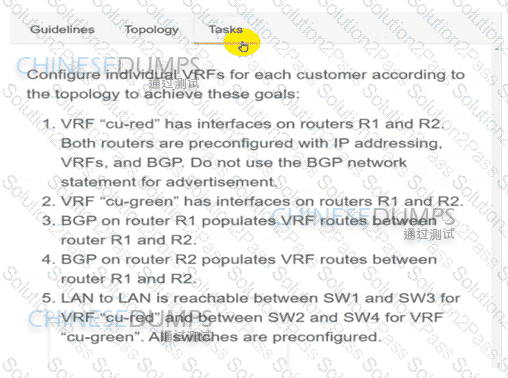
Configure individual VRFs for each customer according to the topology to achieve these goals :
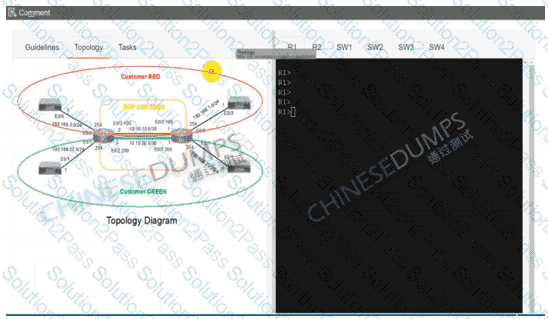

R1
R2
SW1
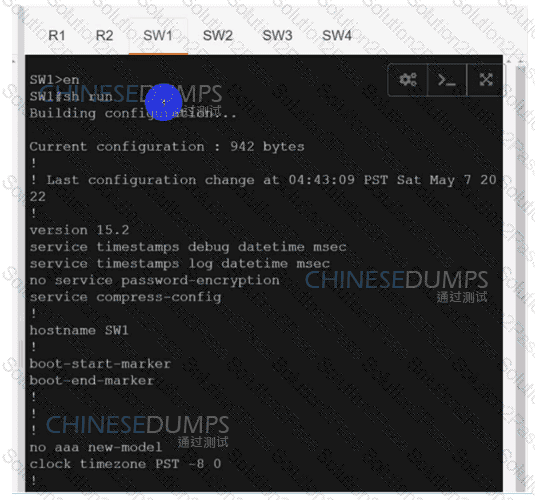
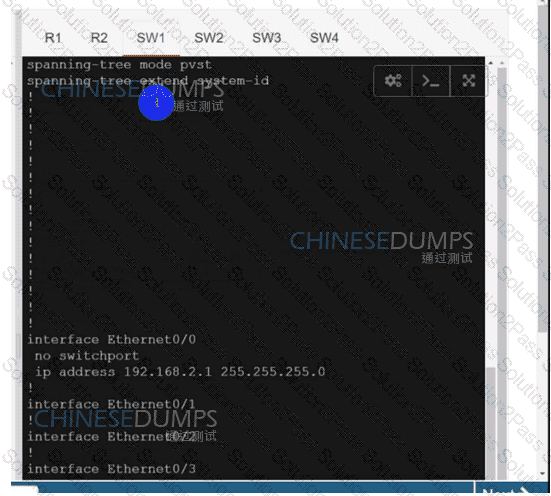
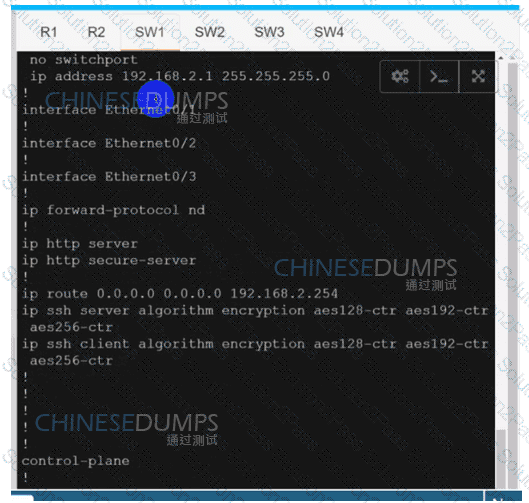
SW2
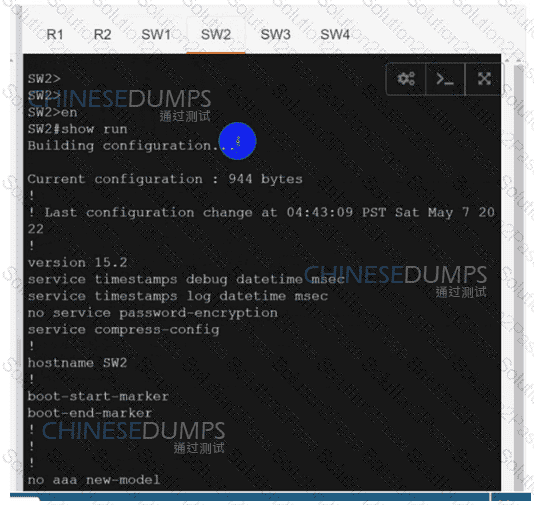
SW3
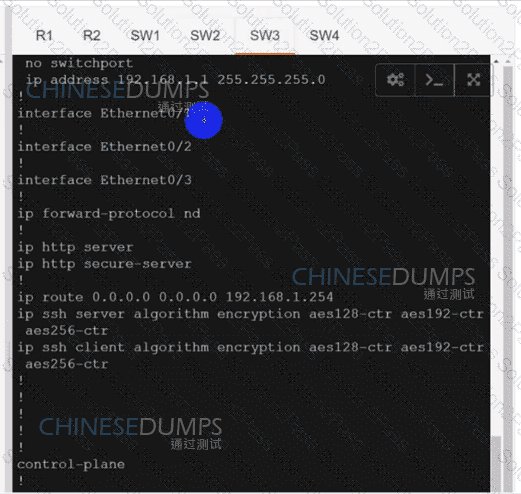
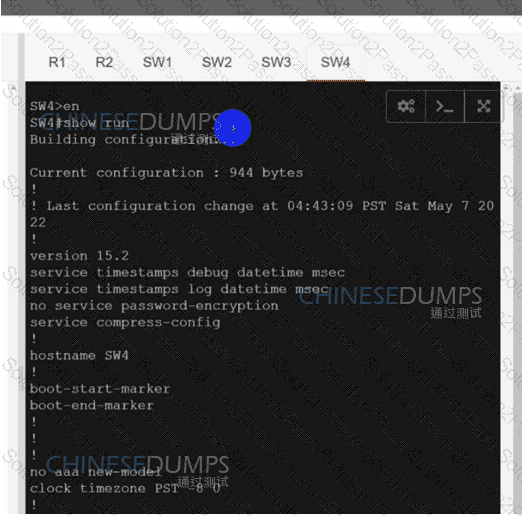
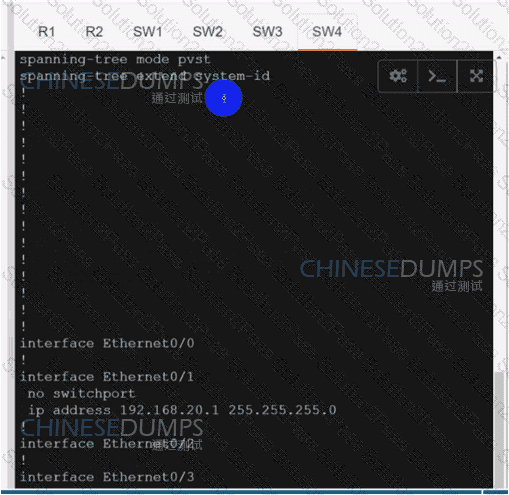
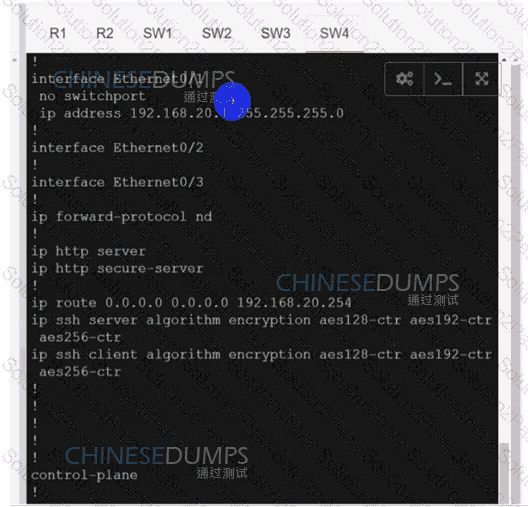
:584
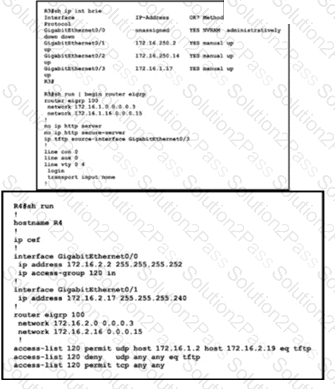
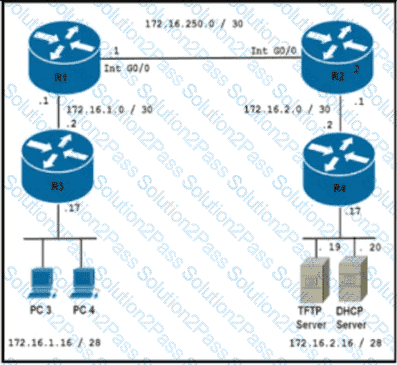
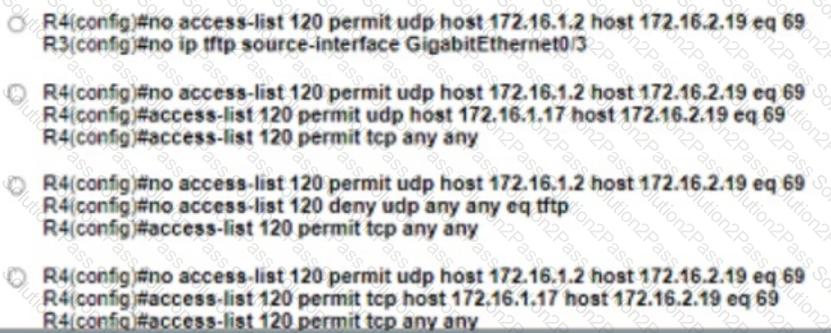
Reler Iothe exhibit The engineer is trying to transfer the newIOSfile to the router R3 but is getting an error Which configuration achieves the file transfer?
Refer to the exhibit.
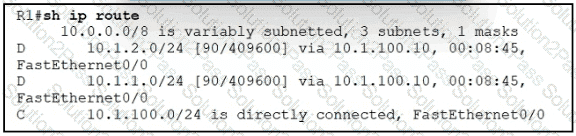
Although summarization is configured for R1 to receive 10.0.0.0/8. more specific routes are received by R1. How should the 10.0.0.0/8 summary route be received from the neighbor, attached to R1 via Fast Ethernet0/0 interface?
Refer to the exhibit.
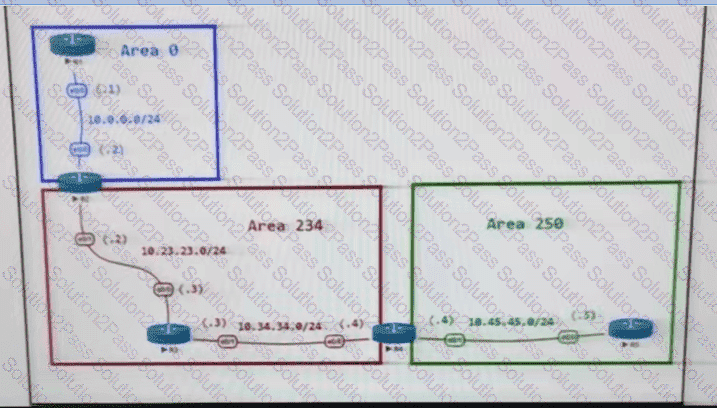
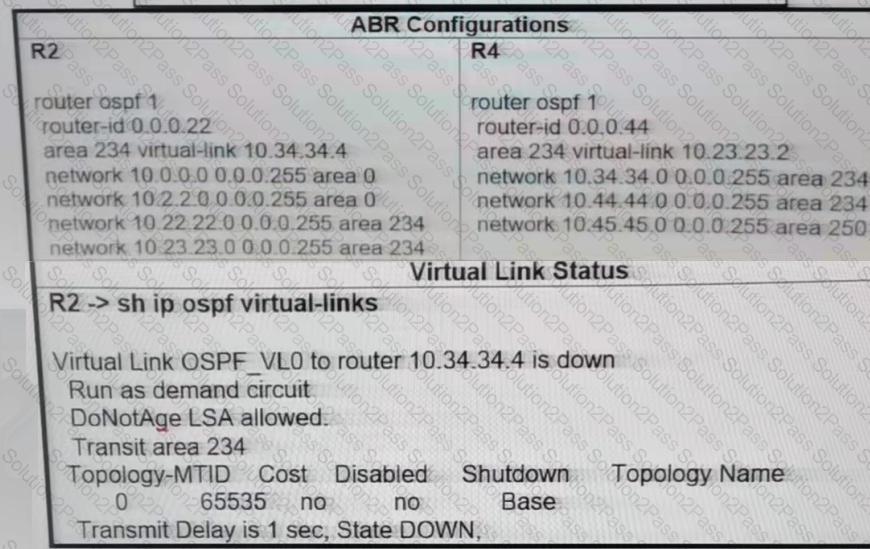
The network administrator configured the network to connect two disjointed networks and ail the connectivity is up except the virtual link which causes area 250 to be unreachable. Which two configurations resolve this issue? (Choose two.)
Refer to the exhibit.
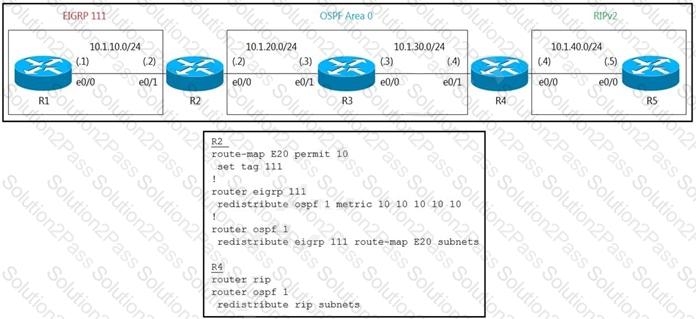
R5 should not receive any routes originated in the EIGRP domain. Which set of configuration changes removes the EIGRP routes from the R5 routing table to fix the issue?
An engineer must establish a connection between two CE routers for two customers with overlapping IP addresses Customer_a is connected to interfaces Gig0/0, and Customer_b is connected to interfaces Gig0/1. Routers CE1 and CE2 are configured as follows:

Drag and drop the code snippets from the right onto the boxes in the configuration to establish the needed connection. Snippets may be used more than once.

Refer to the exhibit.
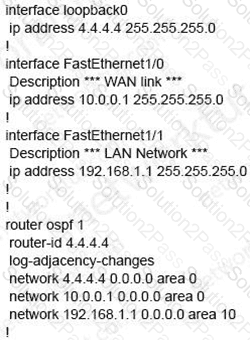
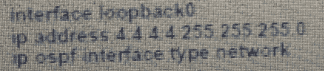
Which set of commands restore reachability to loopback0?
A)
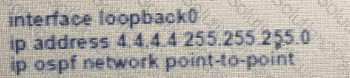
B)

C)
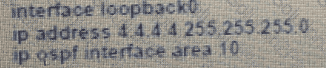
D)
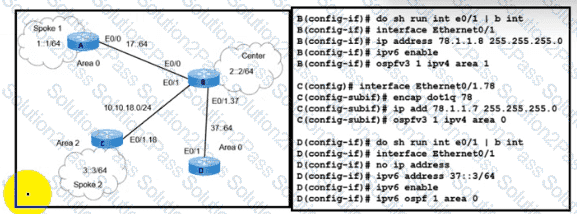
Refer to the exhibit. A network engineer receives a report that Spoke 1 users can perform bank transactions with the server located at the Center site, but Spoke 2 users cannot. Which action resolves the issue?
A company is expanding business by opening 35 branches over the Internet. A network engineer must configure DMVPN at the branch routers to connect with the hub router and allow NHRP to add spoke routers securely to the multicast NHRP mappings automatically Which configuration meets this requirement at the hub router?
A)
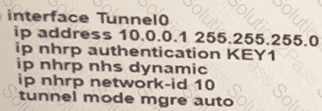
B)

C)

D)

Refer to the exhibit.
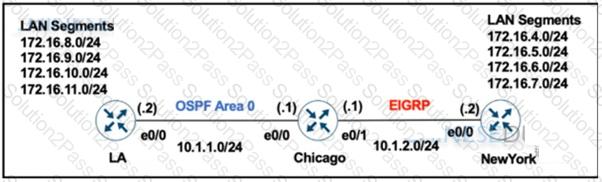
The network administrator configured the Chicago router to mutually redistribute the LA and NewYork routes with OSPF routes to be summarized as a single route in EIGRP using the longest summary mask:

After the configuration, the New York router receives all the specific LA routes but the summary route. Which set of configurations resolves the issue on the Chicago router?

:579
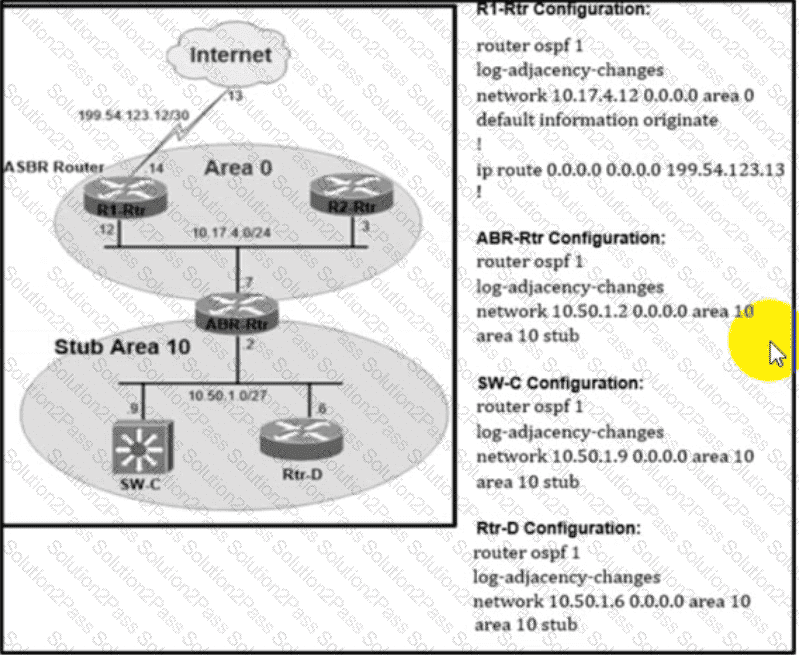
Refer to the exhibit. Router ABR-Rtr is not propagating the internet routes in OSPF area 10. which causes internet reachability problems in the area. Which action resolves the issue?
Which two protocols can cause TCP starvation? (Choose two)
Refer to the exhibit.
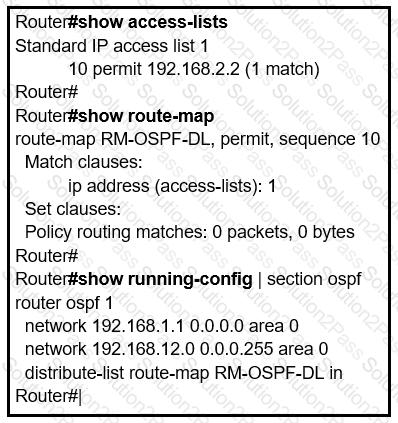
An engineer is trying to block the route to 192.168.2.2 from the routing table by using the
configuration that is shown. The route is still present in the routing table as an OSPF route. Which action blocks the route?
Which statement about IPv6 ND inspection is true?
Refer to the exhibits.
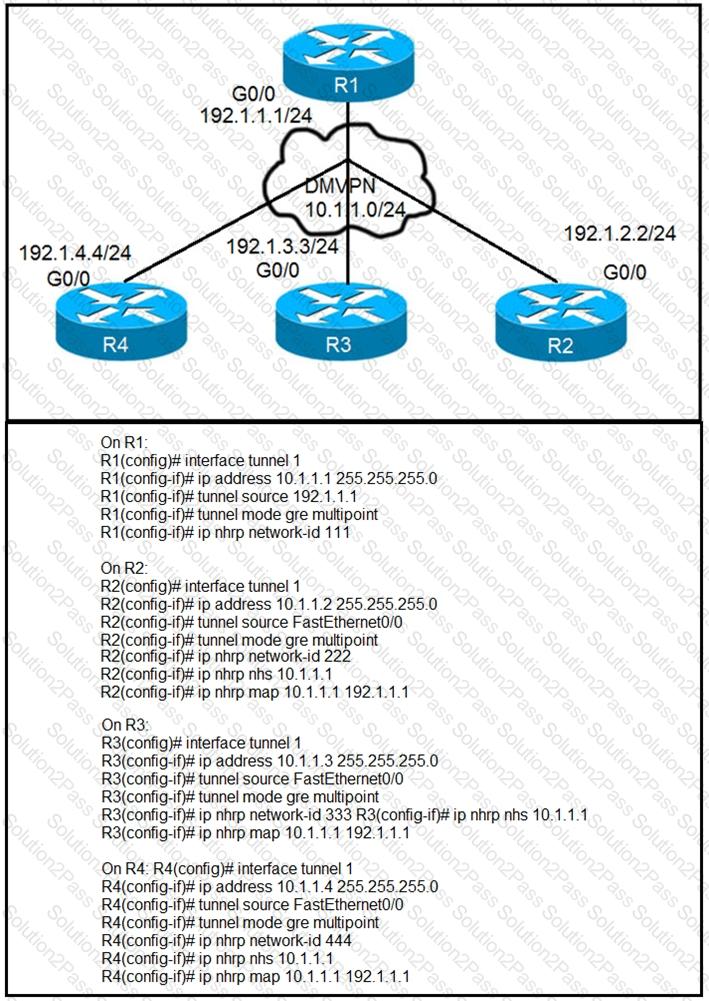
Phase-3 tunnels cannot be established between spoke-to-spoke in DMVPN. Which two
commands are missing? (Choose two.)
Which protocol is used in a DMVPN network to map physical IP addresses to logical IP addresses?
Which statement about route distinguishers in an MPLS network is true?
An engineer configured the wrong default gateway for the Cisco DNA Center enterprise interface during the install. Which command must the engineer run to correct the configuration?
Refer to the exhibit.
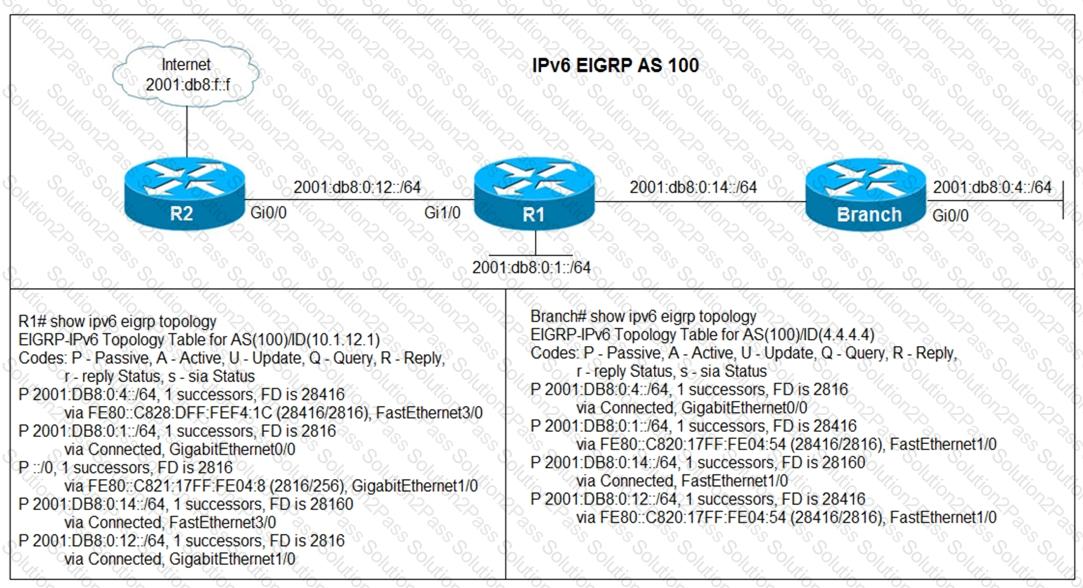
Users in the branch network of 2001:db8:0:4::/64 report that they cannot access the Internet. Which command is issued in IPv6 router EIGRP 100 configuration mode to solve this issue?
Which statement about IPv6 ND inspection is true?
While working with software images, an engineer observes that Cisco DNA Center cannot upload its software image directly from the device. Why is the image not uploading?
An engineer is trying to copy an IOS file from one router to another router by using TFTP. Which two actions are needed to allow the file to copy? (Choose two.)
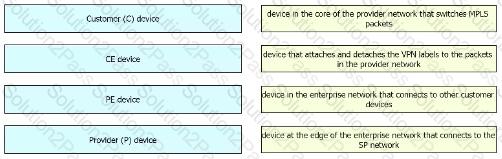
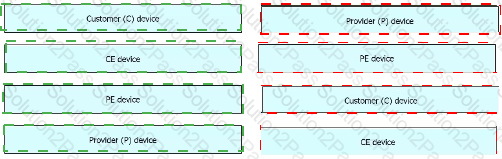
Drag and drop the MPLS VPN device types from me left onto the definitions on the right.
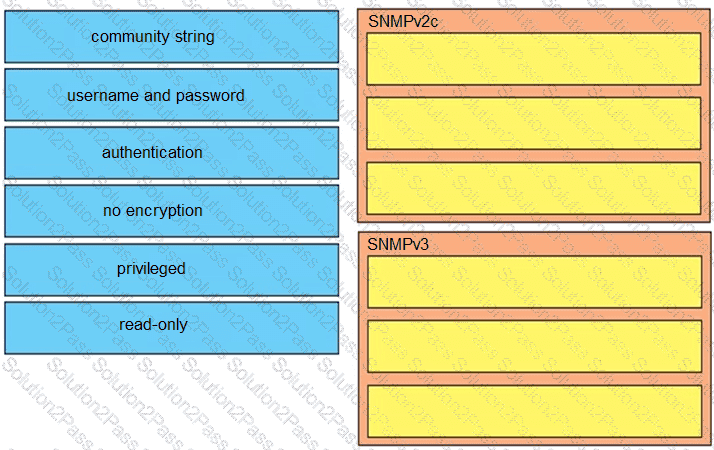
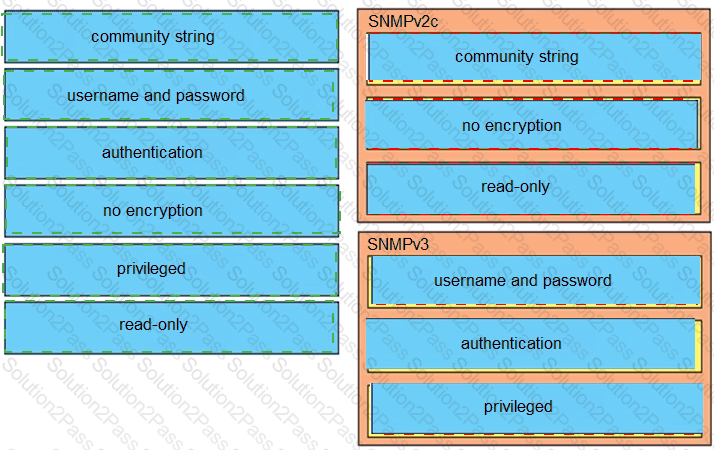
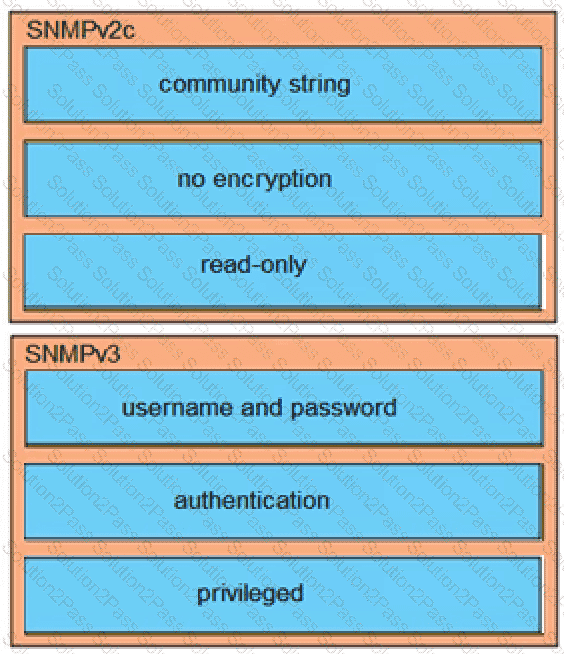
Drag and drop the SNMP attributes in Cisco IOS devices from the left onto the correct SNMPv2c or SNMPV3 categories on the right.
A network engineer is investigating a flapping (up/down) interface issue on a core switch that is synchronized to an NTP server. Log output currently does not show the time of the flap. Which command allows the logging on the switch to show the time of the flap according to the clock on the device?
Refer to the exhibit.

Which configuration denies Telnet traffic to router 2 from 198A:0:200C::1/64?
A)

B)

C)

D)



 Graphical user interface, application Description automatically generated
Graphical user interface, application Description automatically generated