300-710 Cisco Securing Networks with Cisco Firepower (300-710 SNCF) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-710 Securing Networks with Cisco Firepower (300-710 SNCF) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is noticed that excessive and misleading events filing the database and overloading the Cisco FMC. A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configurationchange must be made to alleviate this issue?
Which group within Cisco does the Threat Response team use for threat analysis and research?
A network engineer is configuring URL Filtering on Firepower Threat Defense. Which two port requirements on the Firepower Management Center must be validated to allow communication with the cloud service? (Choose two.)
Which two statements about bridge-group interfaces in Cisco FTD are true? (Choose two.)
A security engineer manages a firewall console and an endpoint console and finds it challenging and the consuming to review events and modify blocking of specific files in both consoles. Which action must the engineer take to streamline this process?
An engineer is configuring a cisco FTD appliance in IPS-only mode and needs to utilize fail-to-wire interfaces. Which interface mode should be used to meet these requirements?
Which firewall design will allow It to forward traffic at layers 2 and 3 for the same subnet?
An administrator is working on a migration from Cisco ASA to the Cisco FTD appliance and needs to test the rules without disrupting the traffic. Which policy type should be used to configure the ASA rules during this phase of the migration?
Within Cisco Firepower Management Center, where does a user add or modify widgets?
An administrator receives reports that users cannot access a cloud-hosted web server. The access control policy was recently updated with several new policy additions and URL filtering. What must be done to troubleshoot the issue and restore access without sacrificing the organization's security posture?
An engineer must permit SSH on the inside interface of a Cisco Secure Firewall Threat Defense device. SSH is currently permitted only on the management interface. Which type of policy
must the engineer configure?
A network administrator is trying to configure an access rule to allow access to a specific banking site over HTTPS. Which method must the administrator use to meet the requirement?
A network administrator is trying to configure a previously created file policy on a new access policy. Which action must the administrator take before applying the file policy?
An engineermustconfigure a Cisco FMC dashboard in a multidomain deployment Which action must the engineer take to edit a report template from an ancestor domain?
How should a high-availability pair of Cisco Secure Firewall Threat Defense Virtual appliances be deployed to Cisco Secure Firewall Management Center?
An organization has a Cisco FTD that uses bridge groups to pass traffic from the inside interfaces to the outside interfaces. They are unable to gather information about neighbouring Cisco devices or use multicast in their environment. What must be done to resolve this issue?
An engineer needs to configure remote storage on Cisco FMC. Configuration backups must be available from a secure location on the network for disaster recovery. Reports need to back up to a shared location that auditors can access with their Active Directory logins. Which strategy must the engineer use to meet these objectives?
An engineer is investigating connectivity problems on Cisco Firepower for a specific SGT. Which command allows the engineer to capture real packets that pass through the firewall using an SGT of 64?
Which two packet captures does the FTD LINA engine support? (Choose two.)
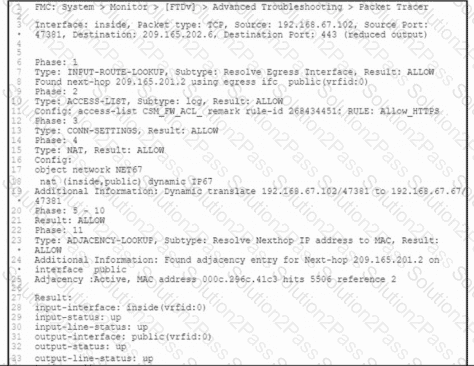
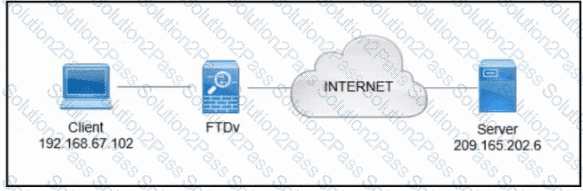
Refer to the exhibit. A client that has IP address 192.168.67.102 reports issues when connecting to a remote server. Based on the topology and output of packet tracer tool, which action resolves the connectivity issue?
