300-725 Cisco Securing the Web with Cisco Web Security Appliance (300-725 SWSA) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-725 Securing the Web with Cisco Web Security Appliance (300-725 SWSA) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two features can be used with an upstream and downstream Cisco WSA web proxy to have the upstream WSA identify users by their client IP address? (Choose two.)
By default, which two pieces of information does the Cisco WSA access log contain? (Choose two.)
Which key is needed to pair a Cisco WSA and Cisco ScanCenter for CTA?
Which command is used to flush a single user from authentication memory?
Which two benefits does AMP provide compared to the other scanning engines on the Cisco WSA? (Choose two.)
Which two parameters are mandatory to control access to websites with proxy authentication on a Cisco WSA? (Choose two.)
Which IP address and port are used by default to run the system setup wizard?
What must be configured first when creating an access policy that matches the Active Directory group?
Which port is configured in a browser to use the Cisco WSA web proxy with default settings?
B.8443
C.8021
D.3128
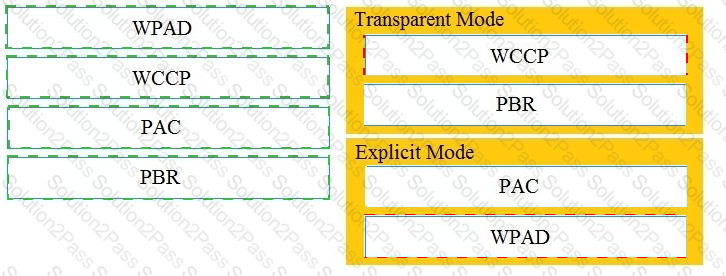
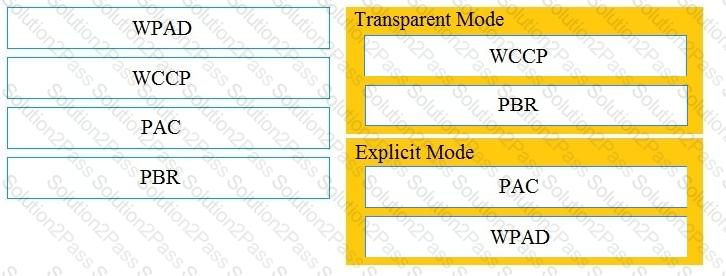
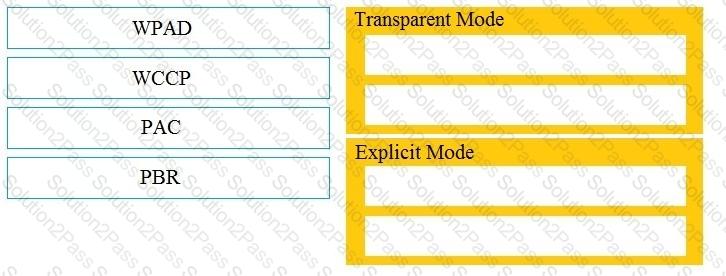
Drag and drop the Cisco WSA methods from the left onto the correct deployment modes on the right.
Which two configuration options can be configured when invalid certificates are processed with the HTTPS proxy on WSA enabled? (Choose two.)
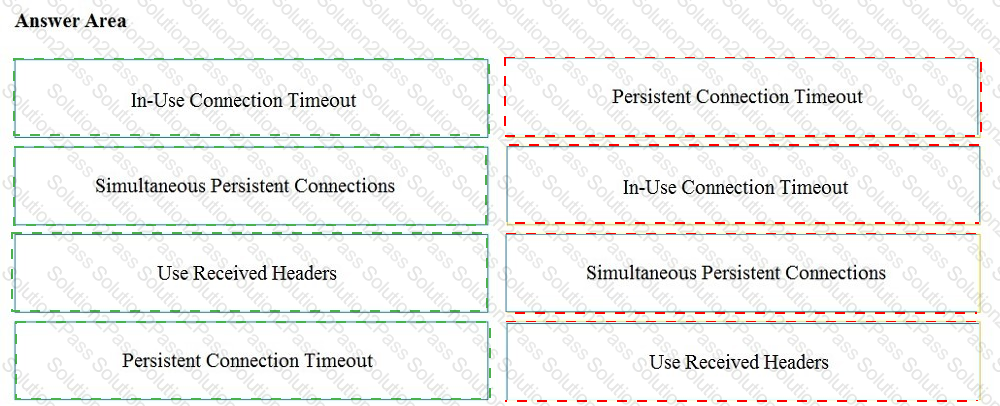
Drag and drop the properties from the left onto the correct advanced web proxy setting descriptions on the right.

What is needed to enable an HTTPS proxy?
What is a valid predefined time range when configuring a Web Tracking query?
When an access policy is created, what is the default option for the Application Settings?
What must be configured to require users to click through an acceptance page before they are allowed to go to the Internet through the Cisco WSA?
Which statement about identification profile default settings on the Cisco WSA is true?
What is the purpose of using AMP file analysis on a Cisco WSA to continuously evaluate emerging threats?