300-735 Cisco Automating and Programming Cisco Security Solutions (300-735 SAUTO) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 300-735 Automating and Programming Cisco Security Solutions (300-735 SAUTO) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which URI string is used to create a policy that takes precedence over other applicable policies that are configured on Cisco Stealthwatch?
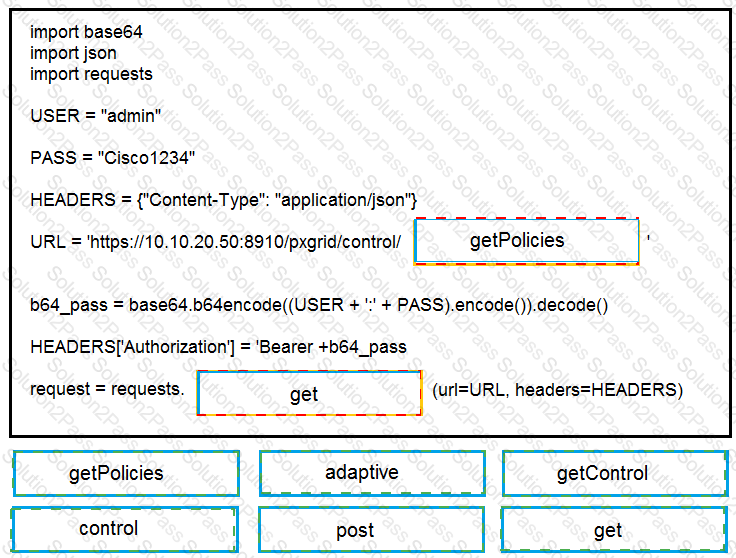
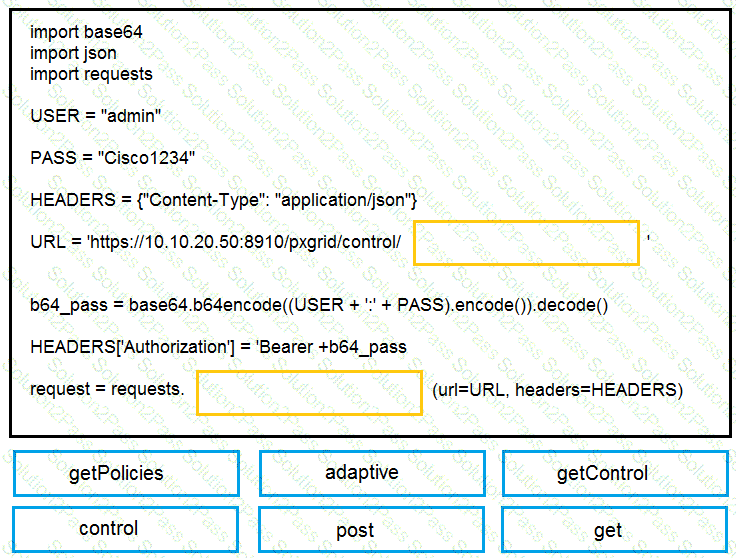
Drag and drop the items to complete the pxGrid script to retrieve all Adaptive Network Control policies. Assume that username, password, and base URL are correct. Not all options are used.
Refer to the exhibit.

Which expression prints the text "802.1x"?
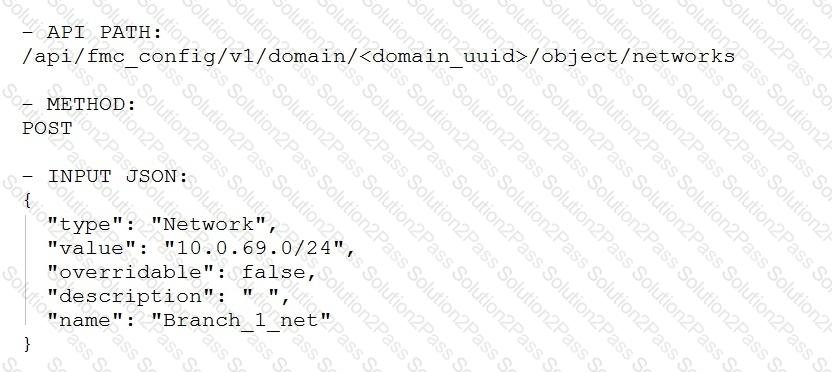
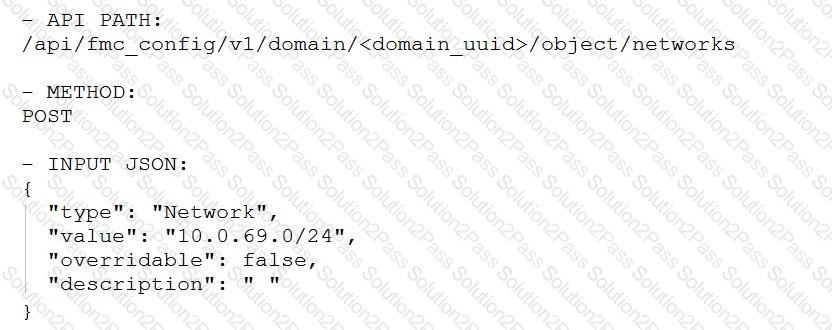
Which snippet is used to create an object for network 10.0.69.0/24 using Cisco Firepower Management Center REST APIs?
A)
B)
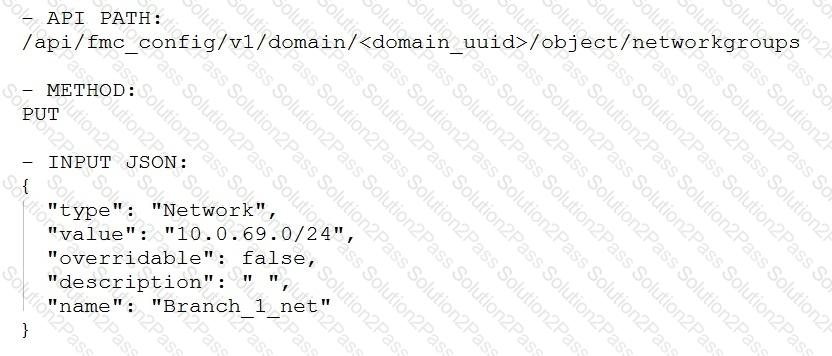
C)
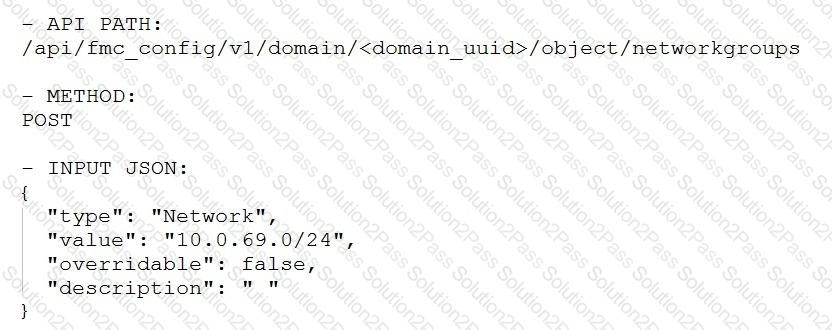
D)
What are two advantages of Python virtual environments? (Choose two.)
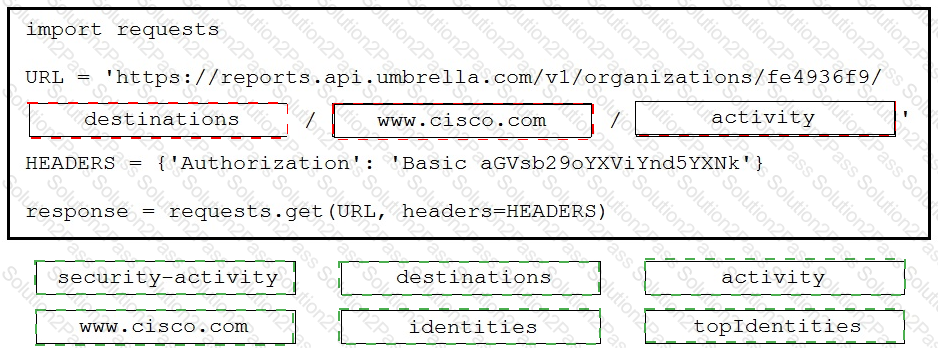
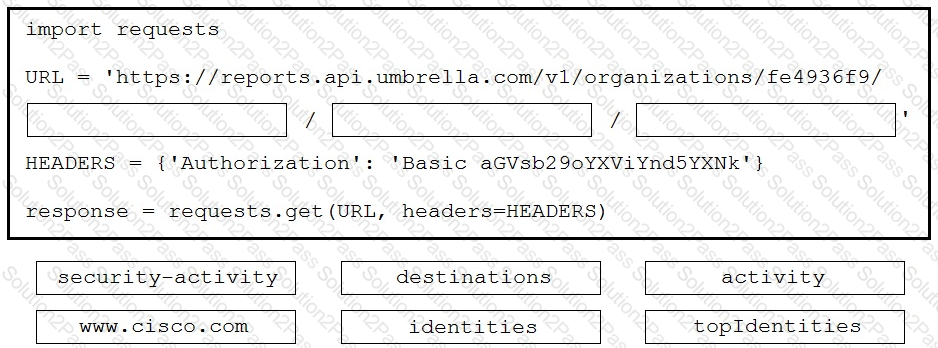
A Python script is being developed to return the top 10 identities in an organization that have made a DNS request to "www.cisco.com ".
Drag and drop the code to complete the Cisco Umbrella Reporting API query to return the top identities. Not all options are used.
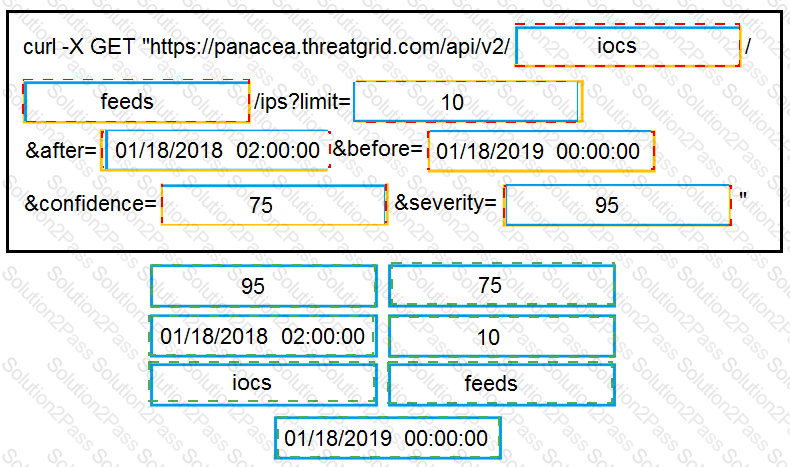
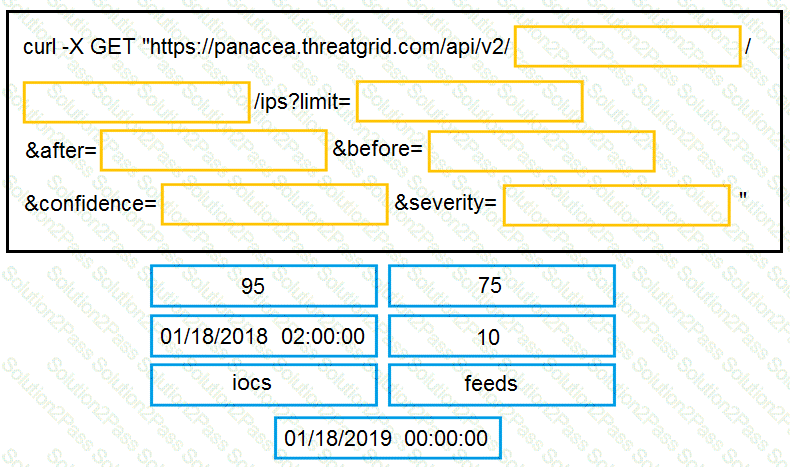
Drag and drop the items to complete the curl request to the ThreatGRID API. The API call should request the first 10 IP addresses that ThreatGRID saw samples communicate with during analysis, in the first two hours of January 18th (UTC time), where those communications triggered a Behavior Indicator that had a confidence equal to or higher than 75 and a severity equal to or higher than 95.
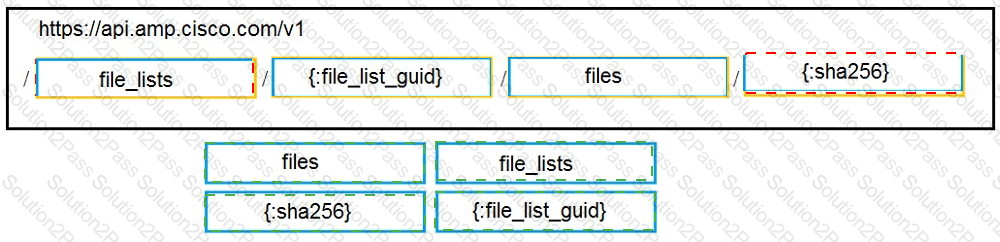
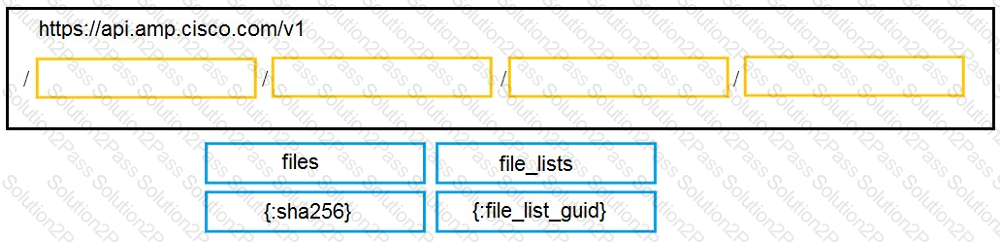
Drag and drop the code to complete the URL for the Cisco AMP for Endpoints API POST request so that it will add a sha256 to a given file_list using file_list_guid.
Which curl command lists all tags (host groups) that are associated with a tenant using the Cisco Stealthwatch Enterprise API?
Which query parameter is required when using the reporting API of Cisco Security Management Appliances?
Refer to the exhibit.
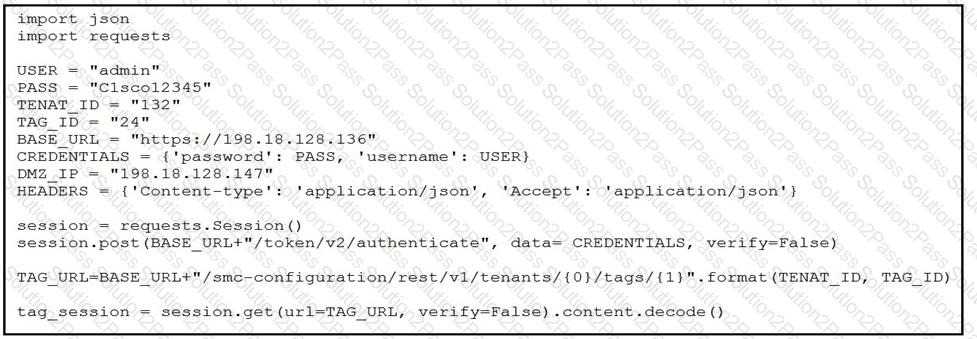
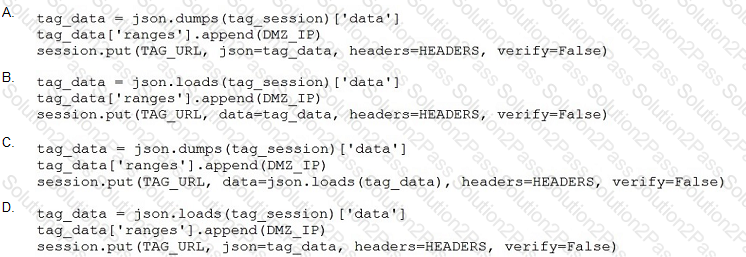
A network operator wants to add a certain IP to a DMZ tag.
Which code segment completes the script and achieves the goal?
Refer to the exhibit.
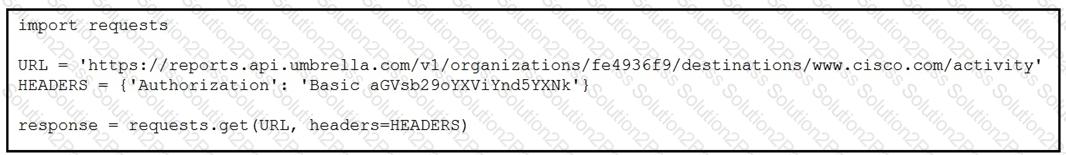
The script outputs too many results when it is queried against the Cisco Umbrella Reporting API.
Which two configurations restrict the returned result to only 10 entries? (Choose two.)
Which API is used to query if the domain “example.com” has been flagged as malicious by the Cisco Security Labs team?
Refer to the exhibit.
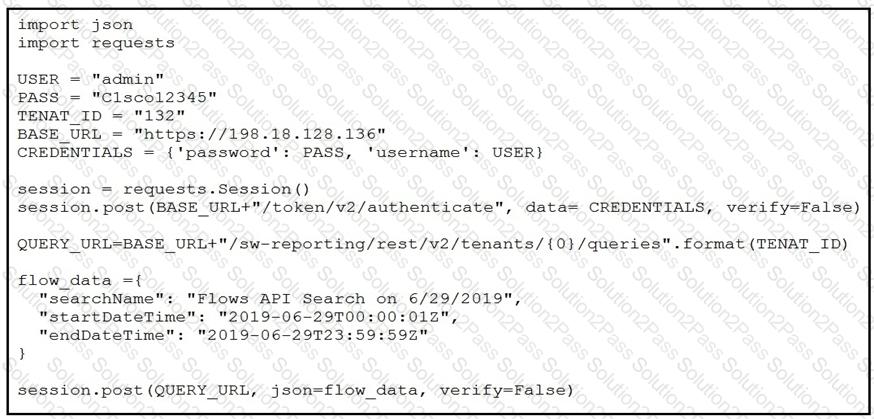
A network operator must generate a daily flow report and learn how to act on or manipulate returned data. When the operator runs the script, it returns an enormous amount of information.
Which two actions enable the operator to limit returned data? (Choose two.)
Which snippet describes the way to create an URL object in Cisco FDM using FDM REST APIs with curl?
A)
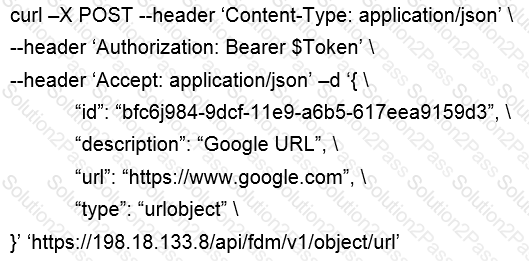
B)
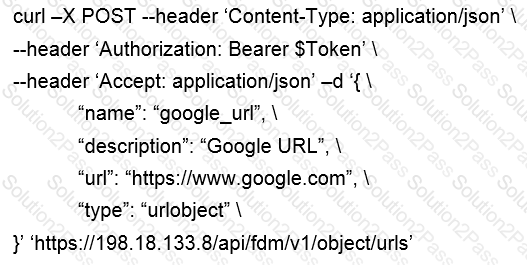
C)
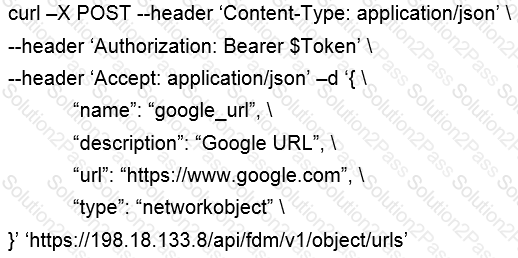
D)
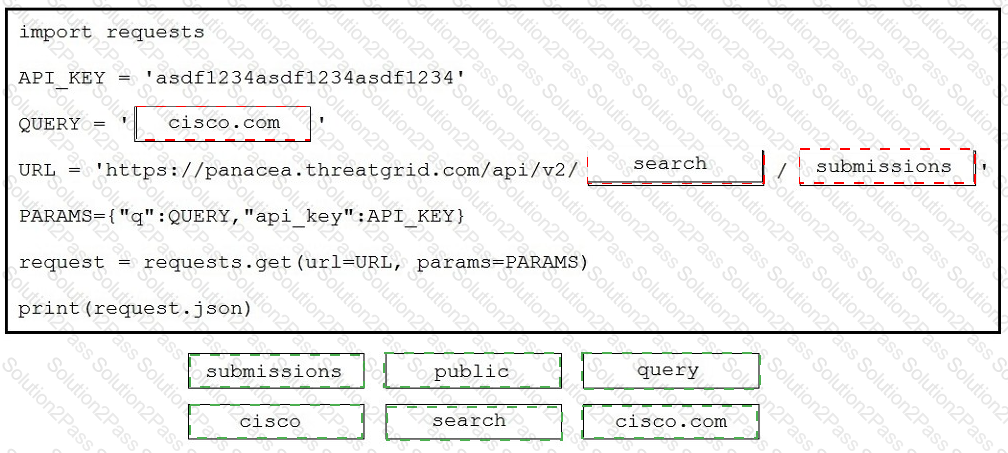
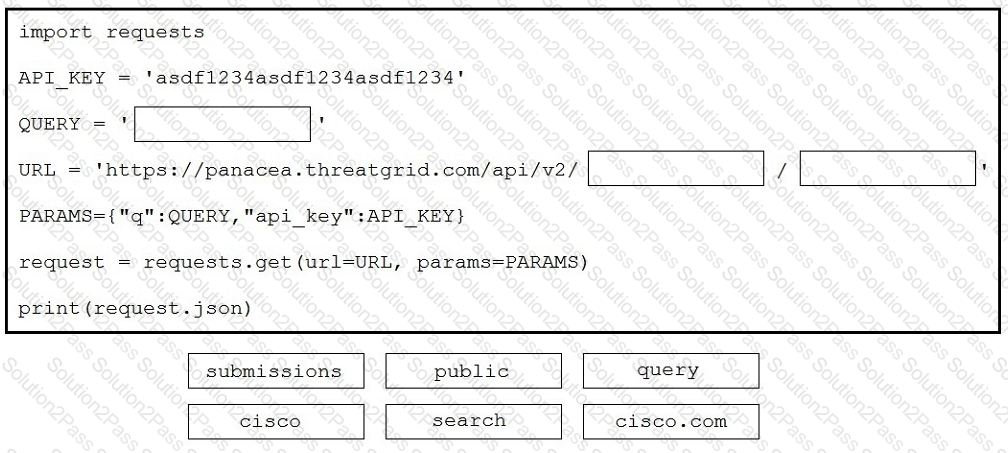
Drag and drop the code to complete the script to search Cisco ThreatGRID and return all public submission records associated with cisco.com. Not all options are used.
Which two destinations are supported by the Cisco Security Management Appliance reporting APIs? (Choose two.)
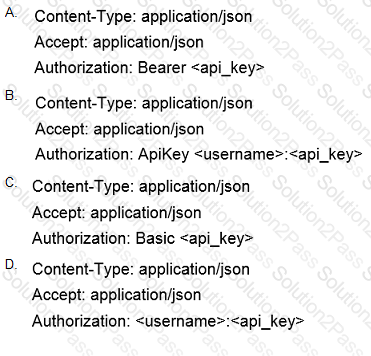
Which header set should be sent with all API calls to the Cisco Stealthwatch Cloud API?