300-740 Cisco Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-740 Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
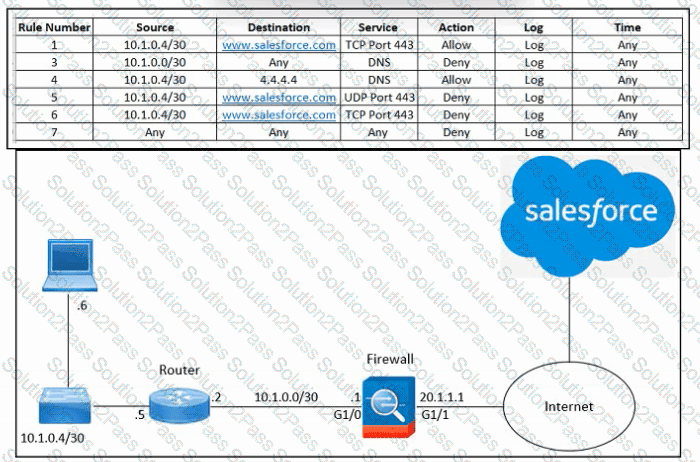
Refer to the exhibit. An engineer must configure the Cisco ASA firewall to allow the client with IP address 10.1.0.6 to access the Salesforce login page at https://www.salesforce.com. The indicated configuration was applied to the firewall and public DNS 4.4.4.4 is used for name resolution; however, the client still cannot access the URL. What should be done to meet the requirements?
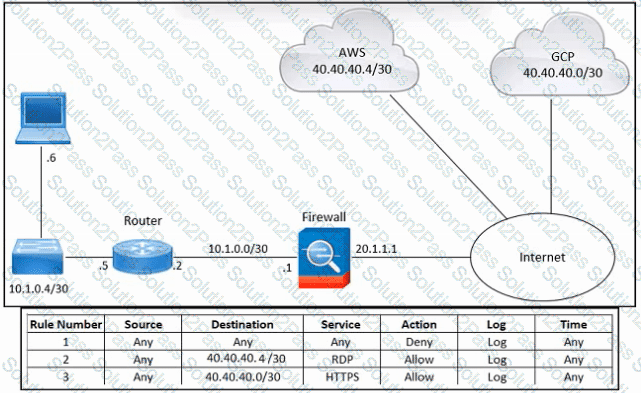
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?
A security analyst detects an employee endpoint making connections to a malicious IP on the internet and downloaded a file named Test0511127691C.pdf. The analyst discovers the machine is infected by trojan malware. What must the analyst do to mitigate the threat using Cisco Secure Endpoint?
What is associated with implementing Cisco zero-trust architecture?
What must be automated to enhance the efficiency of a security team response?
Which types of algorithm does a web application firewall use for zero-day DDoS protection?
Which web application firewall deployment in the Cisco Secure DDoS protects against application layer and volumetric attacks?
A network administrator uses Cisco Umbrella to protect internal users from malicious content. A customer is using an IPsec tunnel to connect to an Umbrella Organization. The administrator was informed about a zero-day vulnerability that infects user machines and uploads sensitive data through the RDP port. The administrator must ensure that no users are connected to the internet using the RDP protocol. Which Umbrella configuration must the administrator apply?
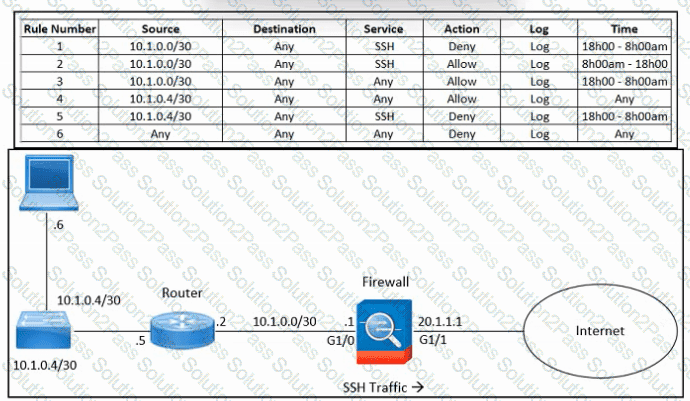
Refer to the exhibit. An engineer must troubleshoot an issue with excessive SSH traffic leaving the internal network between the hours of 18:00 and 08:00. The engineer applies a policy to the Cisco ASA firewall to block outbound SSH during the indicated hours; however, the issue persists. What should be done to meet the requirement?
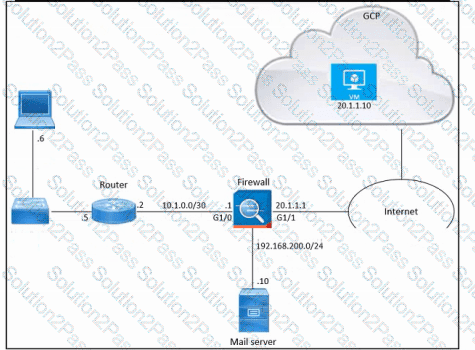
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
An organization is distributed across several sites. Each site is connected to the main HQ using site-to-site VPNs implemented using Secure Firewall Threat Defense. Which functionality must be implemented if the security manager wants to send SaaS traffic directly to the internet?
What does the Cisco Telemetry Broker provide for telemetry data?
What does the MITRE ATT&CK framework catalog?
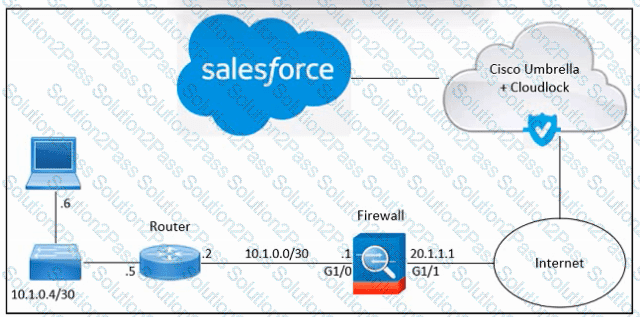
Refer to the exhibit. An engineer must integrate Cisco Cloudlock with Salesforce in an organization. Despite the engineer's successful execution of the Salesforce integration with Cloudlock, the administrator still lacks the necessary visibility. What should be done to meet the requirement?
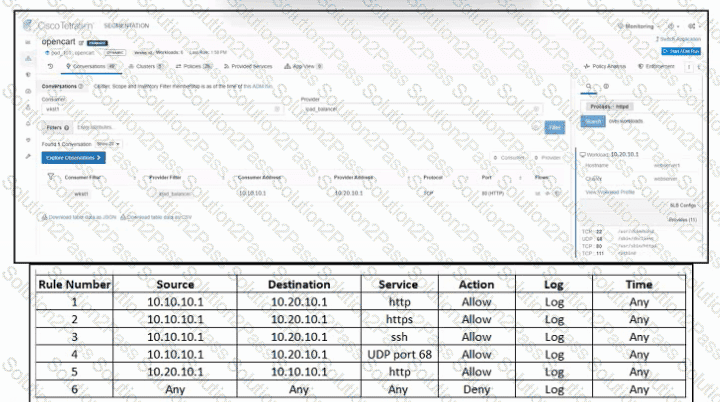
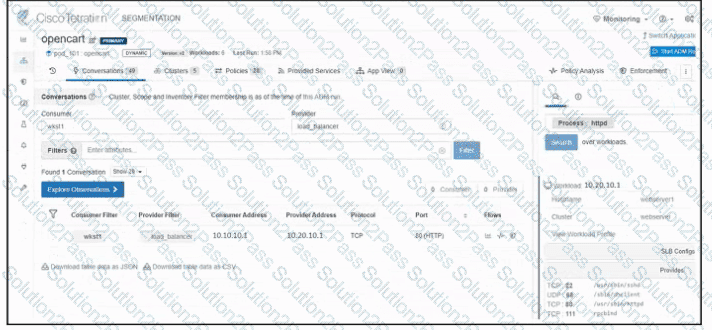
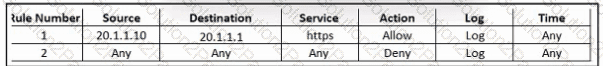
Refer to the exhibit. An engineer must create a firewall policy to allow web server communication only. The indicated firewall policy was applied; however, a recent audit requires that all firewall policies be optimized. Which set of rules must be deleted?
According to the MITRE ATT&CK framework, which approach should be used to mitigate exploitation risks?
How does Cisco XDR perform threat prioritization by using its visibility across multiple platforms?
An administrator received an incident report indicating suspicious activity of a user using a corporate device. The manager requested that the credentials of user user1@cisco.com be reset and synced via the Active Directory. Removing the account should be avoided and used for further investigation on data leak. Which configuration must the administrator apply on the Duo Admin Panel?
