350-201 Cisco Performing CyberOps Using Core Security Technologies (CBRCOR) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-201 Performing CyberOps Using Core Security Technologies (CBRCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.
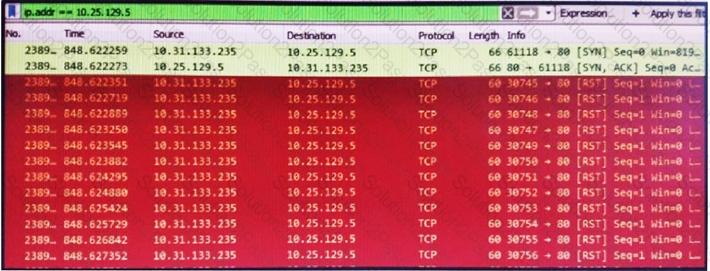
What is occurring in this packet capture?
Refer to the exhibit.
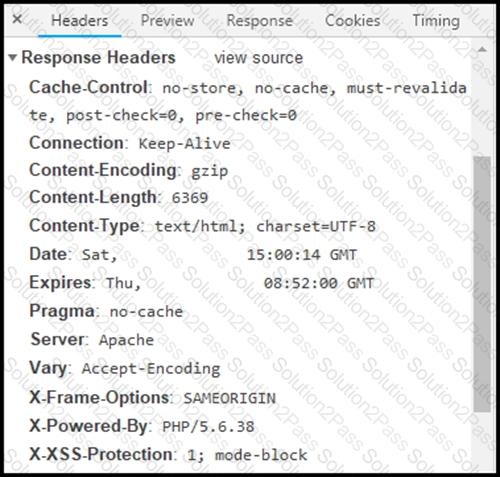
Where are the browser page rendering permissions displayed?
An engineer has created a bash script to automate a complicated process. During script execution, this error occurs: permission denied. Which command must be added to execute this script?
A threat actor attacked an organization’s Active Directory server from a remote location, and in a thirty-minute timeframe, stole the password for the administrator account and attempted to access 3 company servers. The threat actor successfully accessed the first server that contained sales data, but no files were downloaded. A second server was also accessed that contained marketing information and 11 files were downloaded. When the threat actor accessed the third server that contained corporate financial data, the session was disconnected, and the administrator’s account was disabled. Which activity triggered the behavior analytics tool?
What is a benefit of key risk indicators?
An organization is using a PKI management server and a SOAR platform to manage the certificate lifecycle. The SOAR platform queries a certificate management tool to check all endpoints for SSL certificates that have either expired or are nearing expiration. Engineers are struggling to manage problematic certificates outside of PKI management since deploying certificates and tracking them requires searching server owners manually. Which action will improve workflow automation?
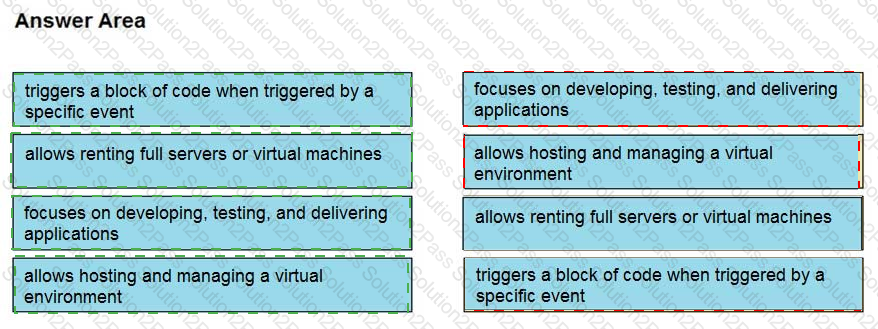
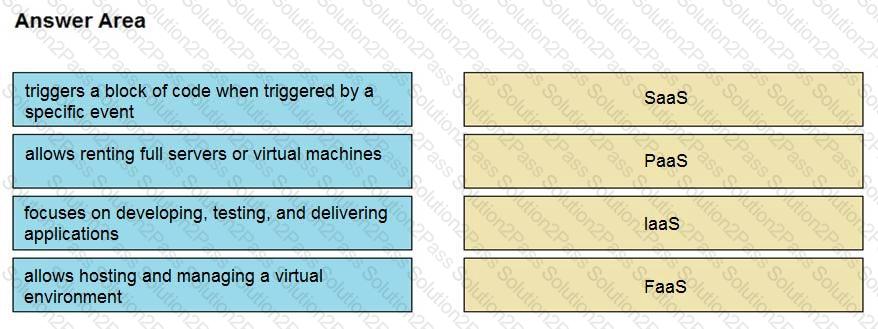
Drag and drop the cloud computing service descriptions from the left onto the cloud service categories on the right.
An engineer receives a report that indicates a possible incident of a malicious insider sending company information to outside parties. What is the first action the engineer must take to determine whether an incident has occurred?
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads. Which standard must the company follow to safeguard the resting data?
Refer to the exhibit.
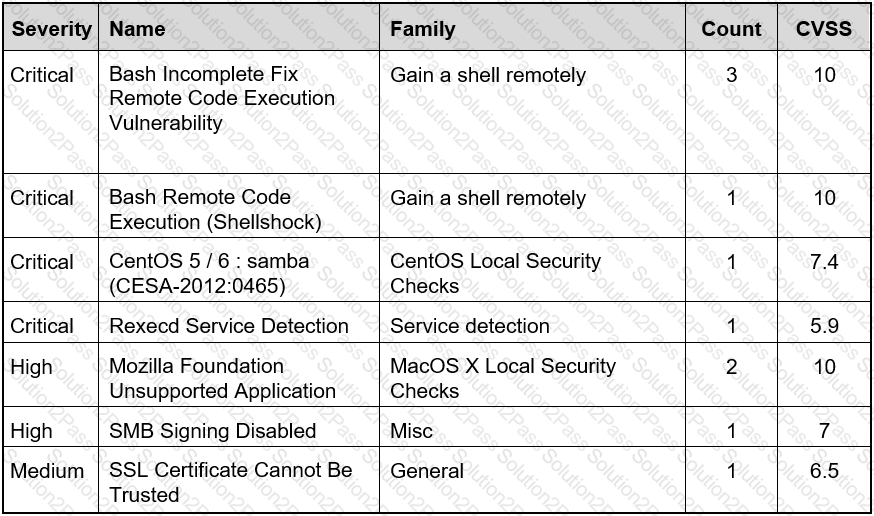
Based on the detected vulnerabilities, what is the next recommended mitigation step?
An engineer is analyzing a possible compromise that happened a week ago when the company? (Choose two.)
Refer to the exhibit.
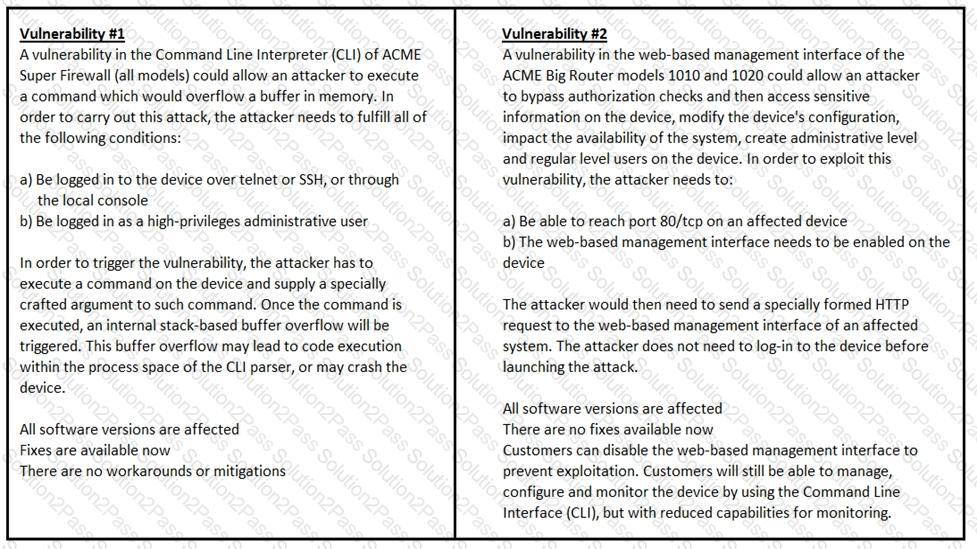
How must these advisories be prioritized for handling?
Refer to the exhibit.
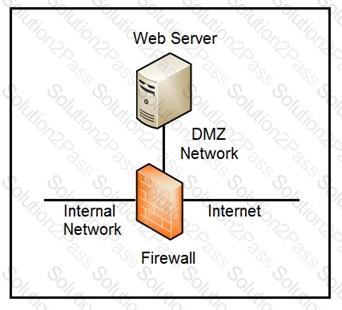
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
A company’s web server availability was breached by a DDoS attack and was offline for 3 hours because it was not deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An analyst conducted the risk assessment using the threat sources, events, and vulnerabilities. Which additional element is needed to calculate the risk?
An API developer is improving an application code to prevent DDoS attacks. The solution needs to accommodate instances of a large number of API requests coming for legitimate purposes from trustworthy services. Which solution should be implemented?
An engineer detects an intrusion event inside an organization’s network and becomes aware that files that contain personal data have been accessed. Which action must be taken to contain this attack?
An engineer is developing an application that requires frequent updates to close feedback loops and enable teams to quickly apply patches. The team wants their code updates to get to market as often as possible. Which software development approach should be used to accomplish these goals?
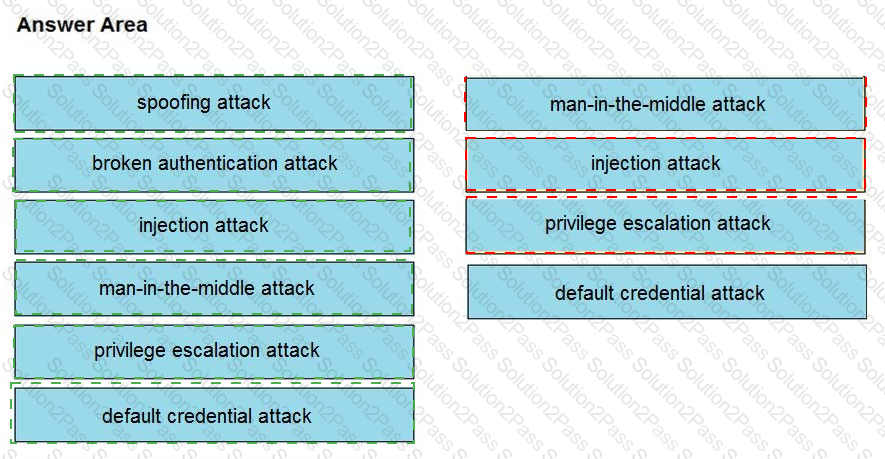
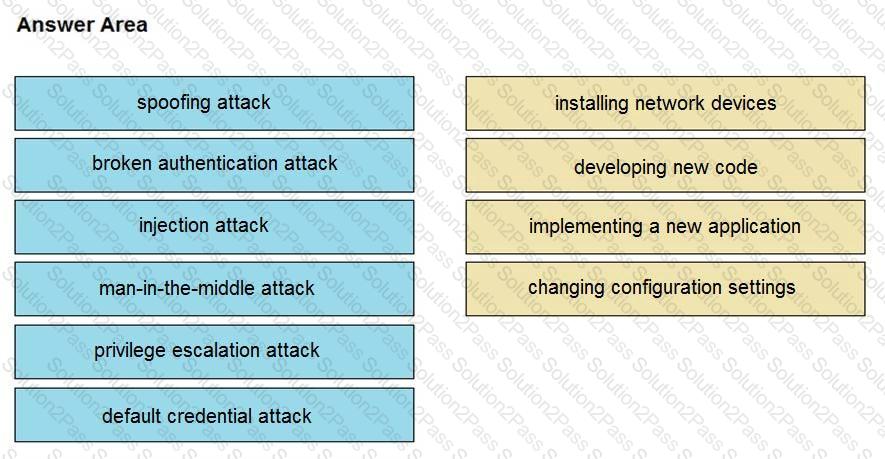
Drag and drop the threat from the left onto the scenario that introduces the threat on the right. Not all options are used.
Refer to the exhibit.
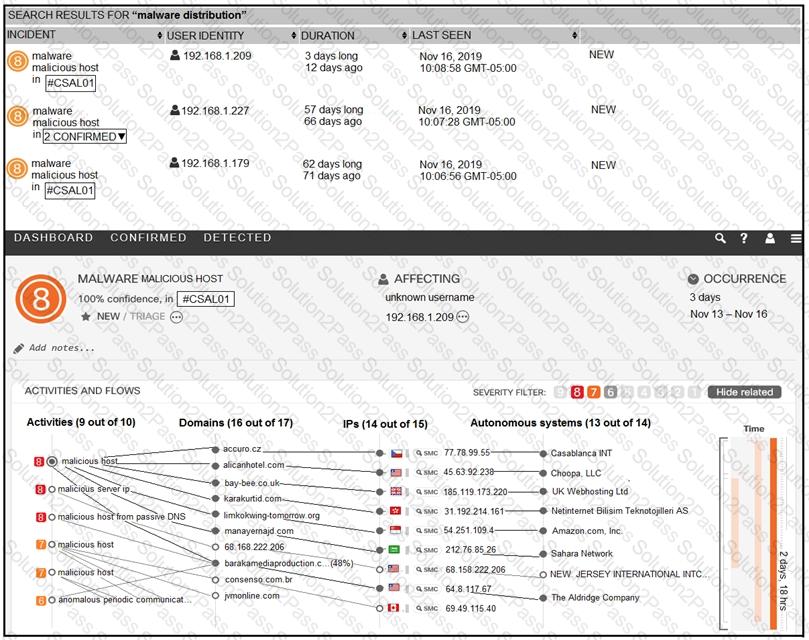
For IP 192.168.1.209, what are the risk level, activity, and next step?
A SOC team is investigating a recent, targeted social engineering attack on multiple employees. Cross- correlated log analysis revealed that two hours before the attack, multiple assets received requests on TCP port 79. Which action should be taken by the SOC team to mitigate this attack?