350-501 Cisco Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 350-501 Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which feature describes the weight parameter for BGP path selection?
Refer to the exhibit:
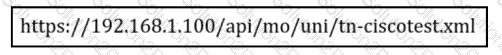
What is the URL used for with REST API?
What is the role of NSO?
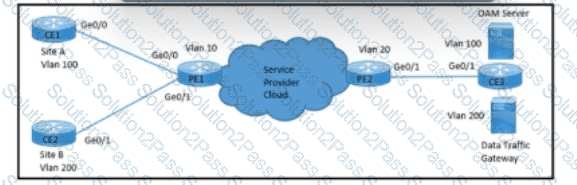
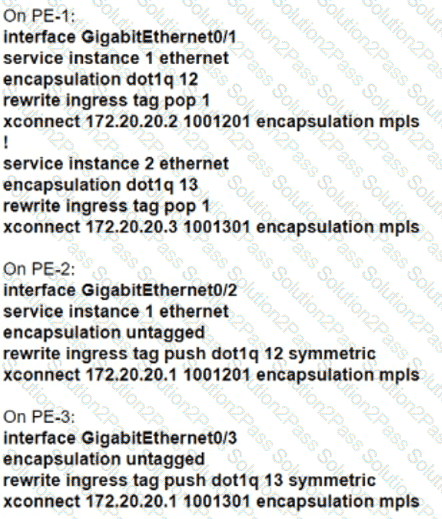
Refer to the exhibit. A network engineer with an employee ID: 5086:72:817 is configuring a connection to manage CE1 from the OAM server on VLAN 100. PE1 must push S-VLAN tag 10 toward PE2 while forwarding traffic from CE1 to the OAM server. PE1 must push S-VLAN tag 20 toward PE2 while forwarding traffic from CE2 to the data traffic gateway. Which configuration must the engineer implement on PE2?
A network architect at ISP must implement a loop-avoidance mechanism in the organization's ring network topology. The architect decided to implement ITU-T G.8032. Intermittent link flaps within two seconds should be ignored. Which two configurations must the architect apply? (Choose two.)
Refer to the exhibit:
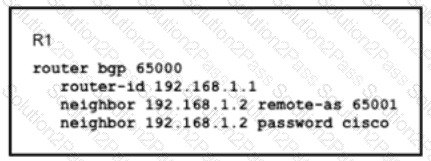
Router R1 and its peer R2 reside on the same subnet in the network, If does it make connections to R27
Refer to the exhibit. Tier 1 ISP A purchased several Tier 2 ISPs to increase their customer base and provide more regional coverage. ISP A plans to implement MPLS services in the access layer, with scalability up to 100.000 devices In one packet network and service recovery up to 50 ms. The network architect decided to use different independent IGP and LDP domains and interconnect LSPs that are based on RFC 3107. Which two actions must the network engineer perform to meet the requirements? (Choose two.)
Refer to the exhibit:

What does this value mean when it is received in XML?
A regional MPLS VPN provider operates m two regions and wants to provide MPLS L 3VPN service for a customer with two sites in these separate locations. The VPN provider approaches another organization to provide backbone carrier services so that the provider can connect to these two locations.
Which statement about this scenario is true?
Refer to the exhibit.
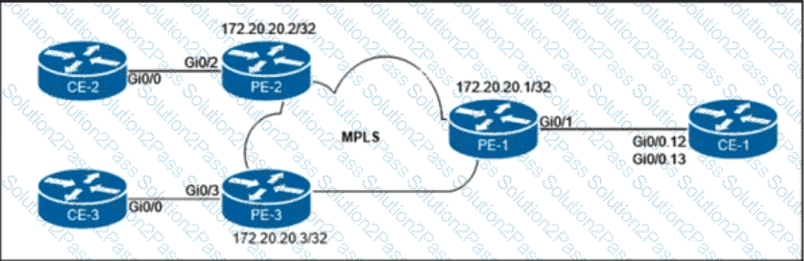
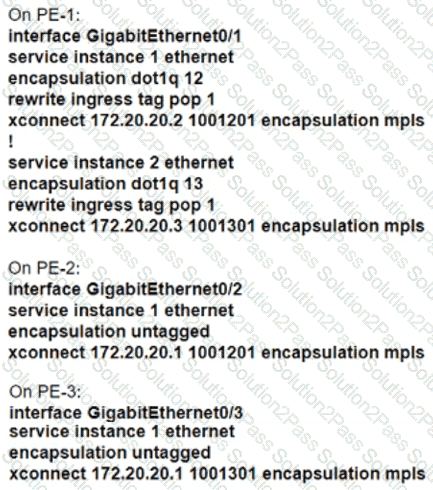
The customer that owns the CE-1, CE-2, and CE-3 routers purchased point-to-point E-Line services from the Carrier Ethernet provider. The service provider is delivering multiplexed UNI at the customer HQ location on PE-1 and untagged UNIs at the PE-2 and PE-3 locations. Additionally, the customer provided these VLAN to EVC mapping requirements:
• EVC 1 between CE-1 and CE-2 must be provisioned with C-VLAN 12 at the HQ location.
• EVC 2 between CE-1 and CE-3 must be provisioned with C-VLAN 13 at the HQ location.
Which configuration must the network engineer implement on the PE routers to provide end-to-end Carrier Ethernet service to the customer?
After troubleshooting multiple outages on the network due to repeated configuration errors, the network architect asked an engineer to enable NETCONF to facilitate future configurations. The configuration must enable syslog messaging to record NETCONF notifications from each of the numerous devices on the network. Which configuration must the engineer apply?
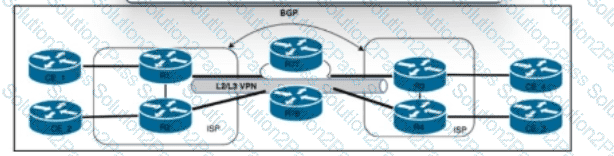
Refer to the exhibit. Company A's network architect is implementing the capabilities that are described in RFC 4379 to provide new options for troubleshooting the company's MPLS network. MPLS LSPs are signaled via the BGP routing protocol with IPv4 unicast prefix FECs. Due to company security policies, access is controlled on the control plane and management plane. Which two tasks must the architect perform to achieve the goal? (Choose two.)
A service provider is in the process of implementing Unified MPLS on an enterprise network with many nodes. After the migration, several new customers will be added to the environment. RFC 3107 is used to build BGP LSPs across the domains. Which action must the networking team take to reduce the full-mesh requirement for IBGP?
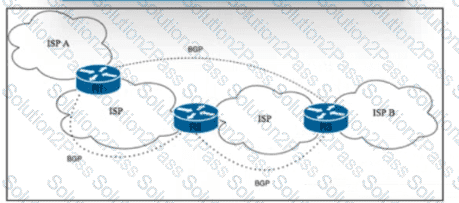
Refer to the exhibit. Tier 1 ISP A is connected to small Tier 3 ISP B. The EBGP routing protocol is used for route exchange. The networking team at ISP A noticed the flapping of BGP sessions with ISP B. The team decides to Improve stability on the network by suppressing the subnet for 30 minutes when a session begins to flap. Which action must the team perform to meet this goal?
Which MPLS design attribute can you use to provide Internet access to a major customer through a separate dedicated VPN?
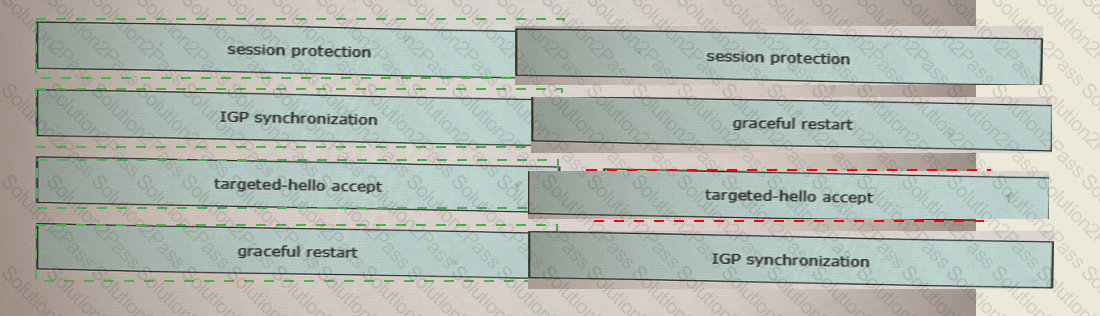
A new PE router is configured to run OSPF as an IGP with LDP on all interfaces. The engineer is trying to prevent black holes after convergence when the PERSON device loses an LDP session with other PE routers. Which action must the engineer take to implement LDP session protection on a new PE router?
Which OoS model allows hosts to report their QoS needs to the network?
Which feature will an operator use while implementing MPLS TE on customer's network, to prevent an LSP from using any overseas inks?
Which action occurs during the traceback phase of the six-phase approach to service provider security?
Drag and drop the LDP features from the left onto the correct usages on the right.

An engineer must apply an 802.1ad-compliant configuration to a new switchport with these requirements:
The switchport must tag all traffic when it enters the port.
The switchport is expected to provide the same level of service to traffic from any customer VLAN.
Which configuration must the engineer use?
Refer to the exhibit:

Which statement describes this configuration?
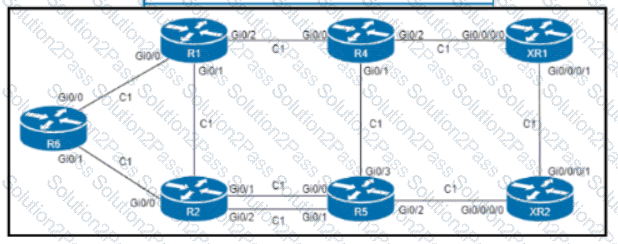
Refer to the exhibit. An engineer configured R6 as the headend LSR of an RSVP-TE LSP to router XR2, with the dynamic path signaled as R6-R2-R5-XR2. and set the OSPF cost of all links to 1. MPLS autotunnel backup Is enabled on all routers to protect the LSP. Which two NNHOP backup tunnels should the engineer use to complete the implementation? (Choose two.)
Refer to the exhibit:
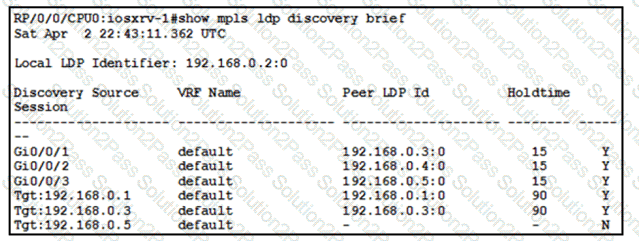
With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?
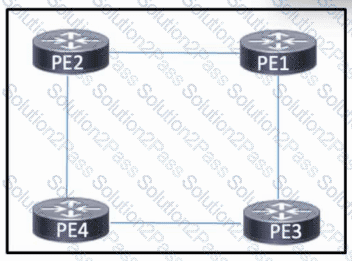
Refer to the exhibit. The four PE routers in the network are connected and running OSPF to share routes. MPLS is enabled on the four routers. The routers are connected and configured to use /30 networks. A network engineer must implement Layer 3 VPN support for traffic between customer sites.
Which task must the engineer perform?
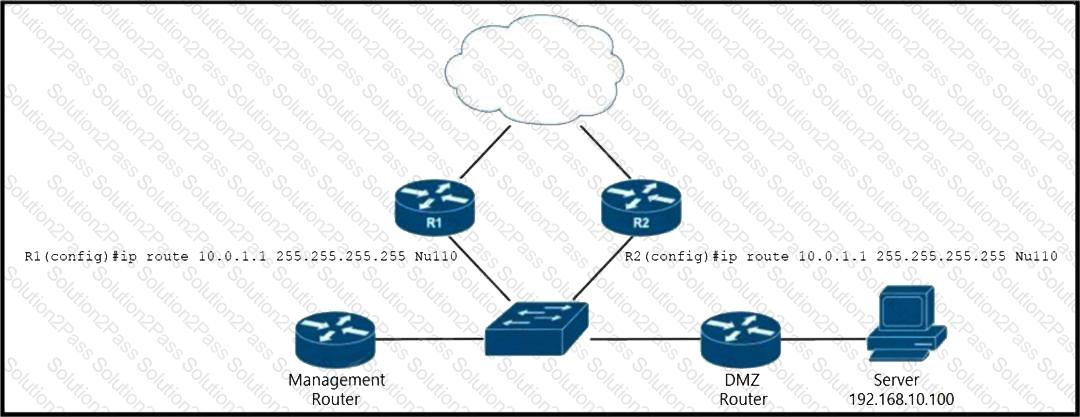
router(config)# route-map blackhole-trigger
router(config-route-map)# match tag 777
router(config-route-map)# set ip next-hop 10.0.1.1
router(config-route-map)# set origin igp
router{config-route-map)# set community no-export
Refer to the exhibit. EIGRP is running across the core to exchange internal routes, and each router maintains iBGP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1, which is used as a black hole route as shown. Which configuration should the operator implement to the management router to create a route map that will redistribute tagged static routes into BGP and create a static route to blackhole traffic with tag 777 that is destined to the server at 192.168.10.100?
Refer to the exhibit.

What does the script configure?

Refer to the exhibit. A multinational corporation with a Cisco-based network wants to leverage Cisco security features to enhance the security of their LAN and protect against eavesdropping and man-in-the-middle attacks. The solution must comply with the IEEE 802.1AE standard. A network engineer must implement the new security configurations on a pair of interconnected Cisco switches. The engineer already completed the configuration to enable AAA new-model and set up a basic AAA configuration for user authentication. Management VLAN 10 is in place for network administration. Which action must the engineer take to meet the requirements?
What is the purpose of OSPF-TE extensions to MPLS traffic engineering functionality?
An organization with big data requirements is implementing NETCONF as part of its migration to a new cloud-based environment. The organization has multiple offices across widespread geography. A network engineer is configuring NETCONF on one of the border routers. Which configuration must the engineer apply to save the running configuration?