400-007 Cisco Certified Design Expert (CCDE v3.1) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 400-007 Cisco Certified Design Expert (CCDE v3.1) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which DCI technology utilizes a “flood and learn” technique to populate the Layer 2 forwarding table?
Company XYZ has 30 sites running a legacy private WAN architecture that connects to the Internet via multiple high-speed connections. The company is now redesigning their network and must comply with these design requirements:
Use a private WAN strategy that allows the sites to connect to each other directly and caters for future expansion.
Use the Internet as the underlay for the private WAN.
Securely transfer the corporate data over the private WAN.
Which two technologies should be incorporated into the design of this network? (Choose two.)
What is the most important operational driver in building a resilient and secure modular network design?
Sometimes SDN leverages various overlay networking technologies to create layer(s) of network abstraction. What describes an overlay network?
Refer to the exhibit.
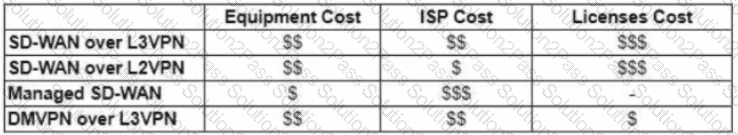
The WAN network of the General Bank of Greece has experienced several outages. It takes too long to activate a new branch site. The networking department of the bank plans to upgrade the legacy end-of-life WAN network with a new flexible, manageable, and scalable in-house solution. The number of branches will increase exponentially in the next fiscal year. The CTO states that the bank’s main goal is OPEX reduction. The network engineering team prepares a table to evaluate the available options. Which WAN technology can be used for the solution?
As part of workspace digitization, a large enterprise has migrated all their users to Desktop as a Service (DaaS), by hosting the backend system in their on-premises data center. Some of the branches have started to experience disconnections to the DaaS at periodic intervals, however, local users in the data center and head office do not experience this behavior. Which technology can be used to mitigate this issue?
Which feature is supported by NETCONF but is not supported by SNMP?
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
You want to mitigate failures that are caused by STP loops that occur before UDLD detects the failure or that are caused by a device that is no longer sending BPDUs. Which mechanism do you use along with UDLD?
Enterprise XYZ wants to implement fast convergence on their network and optimize timers for OSPF. However, they also want to prevent excess flooding of LSAs if there is a constantly flapping link on the network. Which timers can help prevent excess flooding of LSAs for OSPF?
Two enterprise networks must be connected together. Both networks are using the same private IP addresses. The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload feature to save IP addresses from the NAT pools. Which design addresses this requirement using only one Cisco IOS NAT router for both directions?
Company XYZ asks for design recommendations for Layer 2 redundancy. The company wants to prioritize fast convergence and resiliency elements. In the design, which two technologies are recommended? (Choose two.)
In a redundant hub-and-spoke design with inter-spoke links, load oscillation and routing instability occur due to overload conditions. Which two design changes improve resiliency? (Choose two)
A key to maintaining a highly available network is building in the appropriate redundancy to protect against failure. This redundancy is carefully balanced with the inherent complexity of redundant systems. Which design consideration is relevant for enterprise WAN use cases when it comes to resiliency?
How can EIGRP topologies be designed to converge as fast as possible in the event of a point-to-point link failure?
Identity and access management between multiple users and multiple applications has become a mandatory requirement for Company XYZ to fight against ever-increasing cybersecurity threats. To achieve this, federated identity services have been deployed to provide Single Sign-On and Multi-Factor Authentication. Which protocol can be used by Company XYZ to provide authentication and authorization services?
Various teams in different organizations within an enterprise are preparing low-level design documents using a Waterfall project model. Input from relevant stakeholders was captured at the start of the project, and the scope has been defined. What impact will it have if stakeholders ask for changes before documentation is complete?
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
You are tasked with the design of a high available network. Which two features provide fail closed environments? (Choose two.)
Company XYZ is running BGP as their routing protocol. An external design consultant recommends that TCP Path MTU Discovery be enabled. Which effect will this have on the network?
