220-1102 CompTIA A+ Certification Core 2 Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA 220-1102 CompTIA A+ Certification Core 2 Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An IT technician is attempting to access a user's workstation on the corporate network but needs more information from the user before an invitation can be sent. Which of the following command-line tools should the technician instruct the user to run?
A company-owned mobile device is displaying a high number of ads, receiving data-usage limit notifications, and experiencing slow response. After checking the device, a technician notices the device has been jailbroken. Which of the following should the technician do next?
A technician is partitioning a hard disk. The five primary partitions should contain 4TB of free space. Which of the following partition styles should the technician use to partition the device?
A technician needs to replace a PC's motherboard. The technician shuts down the PC. Which of the following steps should the technician take next?
Which of the following macOS utilities uses AES-128 to encrypt the startup disk?
A user is setting up a new Windows 10 laptop. Which of the following Windows settings should be used to input the SSID and password?
A systems administrator is tasked with configuring desktop systems to use a new proxy server that the organization has added to provide content filtering. Which of the following Windows utilities is the best choice for accessing the necessary configuration to complete this goal?
Which of the following wireless security features can be enabled lo allow a user to use login credentials to attach lo available corporate SSIDs?
A systems administrator notices that a server on the company network has extremely high CPU utilization. Upon further inspection, the administrator sees that the server Is consistently communicating with an IP address that is traced back to a company that awards digital currency for solving hash algorithms. Which of the following was MOST likely used to compromise the server?
A new employee is having difficulties using a laptop with a docking station The laptop is connected to the docking station, and the laptop is closed. The external monitor works for a few seconds, but then the laptop goes to sleep. Which of the following options should the technician configure in order to fix the Issue?
Which of the following languages is used for scripting the creation of Active Directory accounts?
A user submits a request to have a graphics application installed on a desktop When the technician attempts to install the application, the installation fails and the error message "Not compatible with OS' is displayed. Which of the following is the most likely reason for this error message?
A malicious user was able to export an entire website's user database by entering specific commands into a field on the company's website. Which of the following did the malicious user most likely exploit to extract the data?
A user’s Windows 10 workstation with an HDD is running really slowly. The user has opened, closed, and saved many large files over the past week. Which of the following tools should a technician use to remediate the issue?
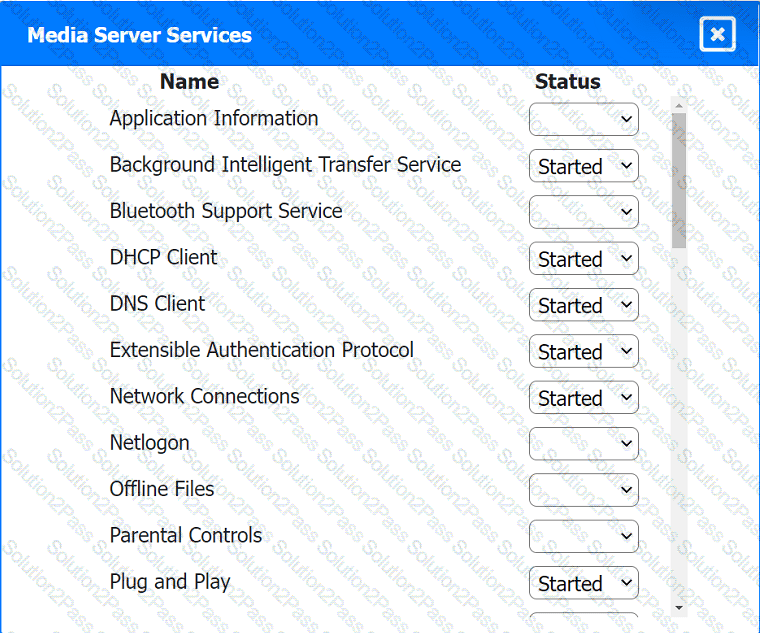
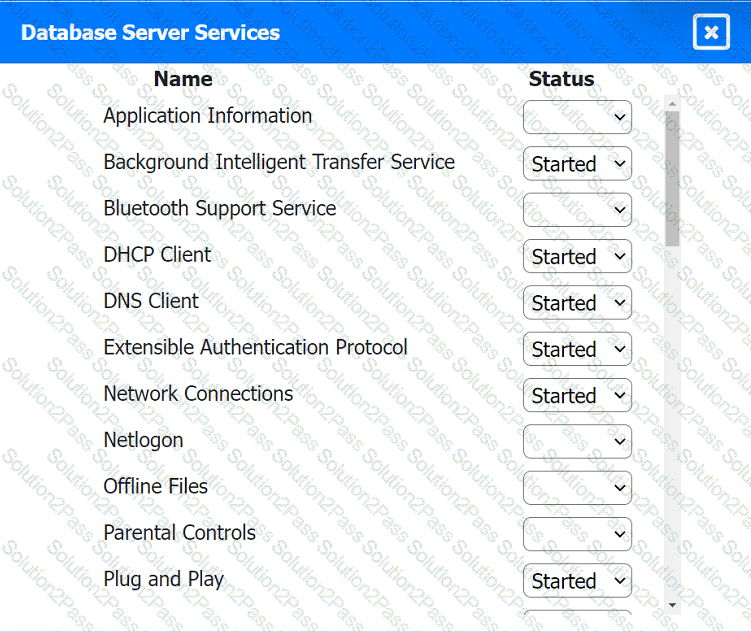
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users' audio issues are
resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.

Users report having difficulty using the Windows Hello facial recognition feature. Which of the following is a secondary feature of Windows Hello that can be used to log in?
A user's company phone has several pending software updates. A technician completes the following steps:
•Rebooted the phone
•Connected to Wi-Fi
•Disabled metered data
Which of the following should the technician do next?
Which of the following best describes a rollback plan?
A technician is troubleshooting a smartphone that is unable to download and install the latest OS update. The technician notices the device operates more slowly than expected, even after rebooting and closing all applications. Which of the following should the technician check next?
A company using Active Directory wants to change the location of all users' "Documents" to a file server on the network. Which of the following should the company set up to accomplish this task?
A user wants to back up a device's OS and data. Which of the following is the best way to accomplish this task?
A technician is following the ticketing system’s best practices when handling user support requests. Which of the following should the technician do first when responding to a user support request that contains insufficient information?
A company uses shared drives as part of a workforce collaboration process. To ensure the correct access permissions, inheritance at the top-level folder is assigned to each department. A manager's team is working on confidential material and wants to ensure only the immediate team can view a specific folder and its subsequent files and subfolders. Which of the following actions should the technician most likely take?
A user reports that an Android mobile device takes a long time to boot, and all applications crash when launched. The user installed the applications from a third-party website. Which of the following steps should the technician complete to diagnose the issue?
A company wants to take advantage of modern technology and transition away from face-to-face meetings. Which of the following types of software would benefit the company the most? (Select two).
An employee has been using the same password for multiple applications and websites for the past several years. Which of the following would be best to prevent security issues?
A technician is setting up a printer on a Linux workstation. Which of the following commands should the technician use to set the default printer?
A company was recently attacked by ransomware. The IT department has remediated the threat and determined that the attack method used was email. Which of the following is the most effective way to prevent this issue from reoccurring?
A user clicked a link in an email, and now the cursor is moving around on its own. A technician notices that File Explorer is open and data is being copied from the local drive to an unknown cloud storage location. Which of the following should the technician do first?
A user is experiencing the following issues with Bluetooth on a smartphone:
•The user cannot hear any sound from a speaker paired with the smartphone.
•The user is having issues synchronizing data from their smart watch, which is also connected via Bluetooth.
A technician checked the Bluetooth settings, confirmed it is successfully paired with a speaker, and adjusted the volume levels, but still could not hear anything. Which of the following steps should the technician take next to troubleshoot the Bluetooth issues?
An administrator needs to back up the following components of a single workstation:
•The installation of the operating system
•Applications
•User profiles
•System settings
Which of the following backup methods can the administrator use to ensure the workstation is properly backed up?
Which of the following environmental controls is most important to maintain the safety of a data center?
A customer, whose smartphone's screen was recently repaired, reports that the device has no internet access through Wi-Fi. The device shows that it is connected to Wi-Fi, has an address of 192.168.1.42. and has no subnet mask. Which of the following should the technician check next?
A workstation is displaying a message indicating that a user must exchange cryptocurrency for a decryption key. Which of the following is the best way for a technician to return the device to service safely?
The courts determined that a cybercrimes case could no longer be prosecuted due to the agency's handling of evidence. Which of the following was MOST likely violated during the investigation?
Which of the following operating systems were designed for smartphones? (Select two).
A desktop technician has received reports that a user's PC is slow to load programs and saved files. The technician investigates and discovers an older HDD with adequate free space. Which of the following should the technician use to alleviate the issue first?
A change advisory board authorized a setting change so a technician is permitted to Implement the change. The technician successfully implemented the change. Which of the following should be done next?
A company recently experienced a security incident in which a USB drive containing malicious software was able to covertly install malware on a workstation. Which of the following actions should be taken to prevent this incident from happening again? (Select two).
A user is receiving repeated pop-up advertising messages while browsing the internet. A malware scan Is unable to locate the source of an infection. Which of the following should the technician check NEXT?
