PT0-002 CompTIA PenTest+ Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA PT0-002 CompTIA PenTest+ Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A penetration tester wants to identify CVEs that can be leveraged to gain execution on a Linux server that has an SSHD running. Which of the following would BEST support this task?
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server.
Which of the following can be done with the pcap to gain access to the server?
A company that requires minimal disruption to its daily activities needs a penetration tester to perform information gathering around the company’s web presence. Which of the following would the tester find MOST helpful in the initial information-gathering steps? (Choose two.)
Which of the following should a penetration tester attack to gain control of the state in the HTTP protocol after the user is logged in?
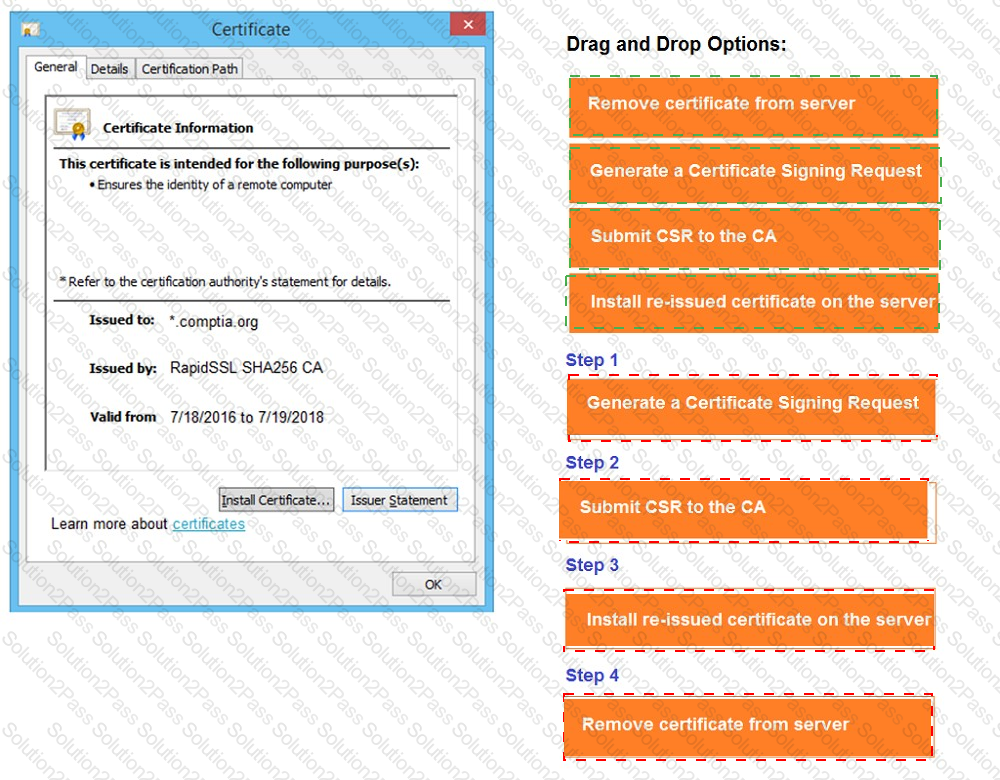
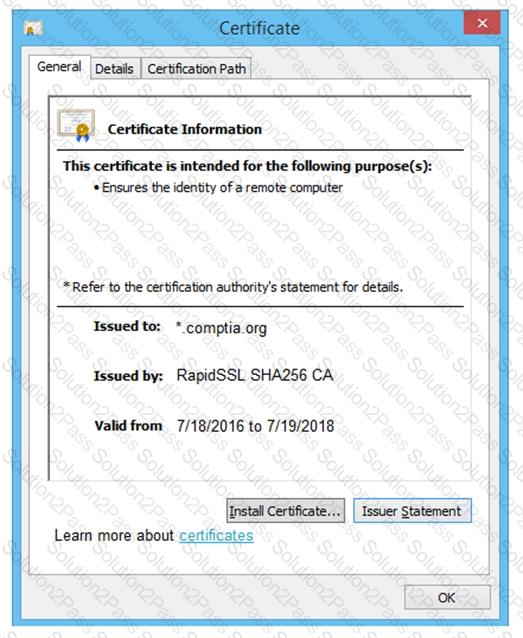
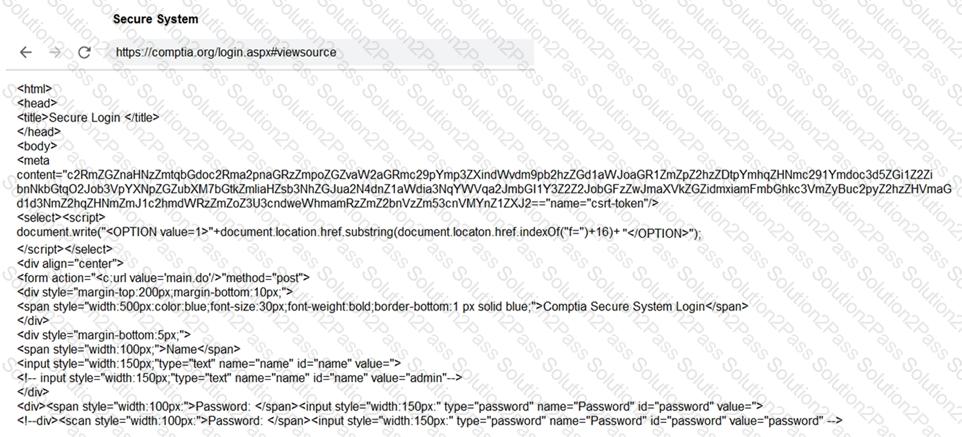
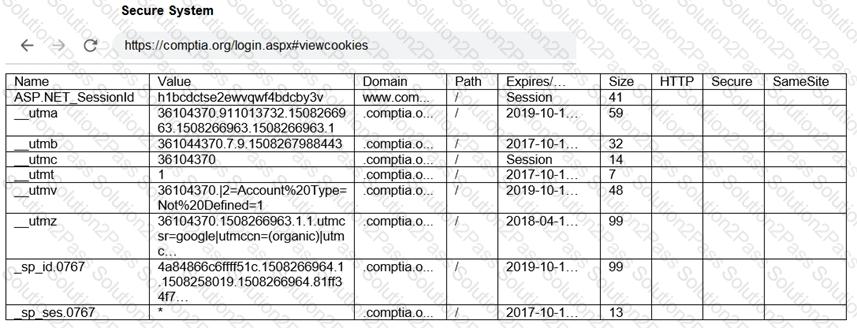
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

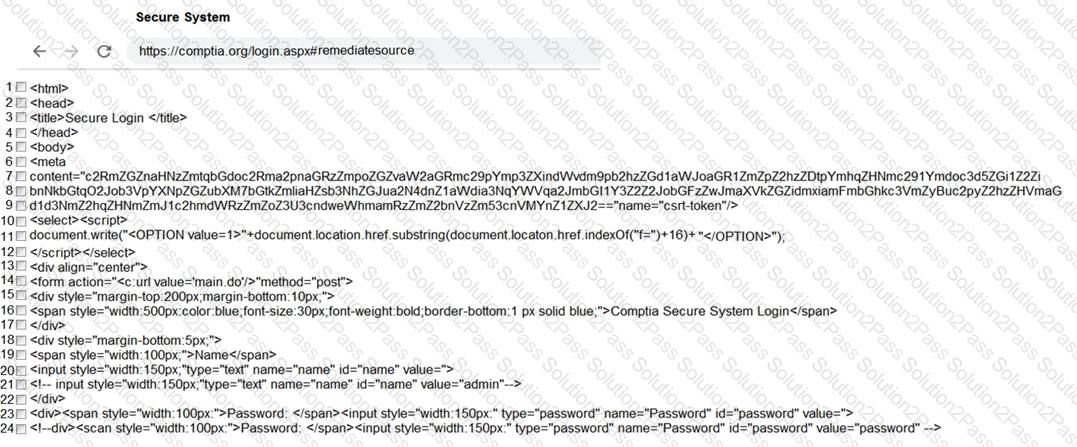
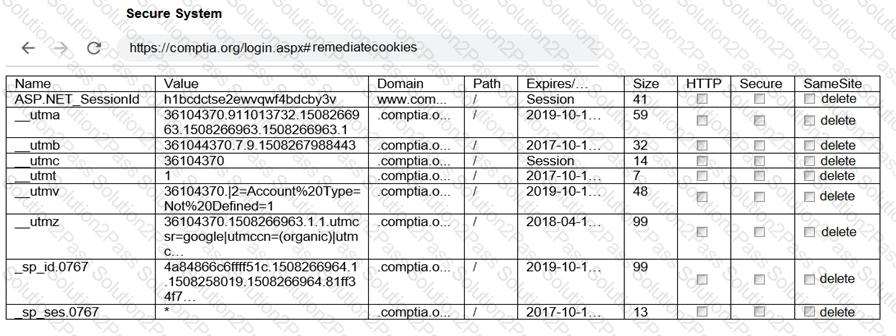
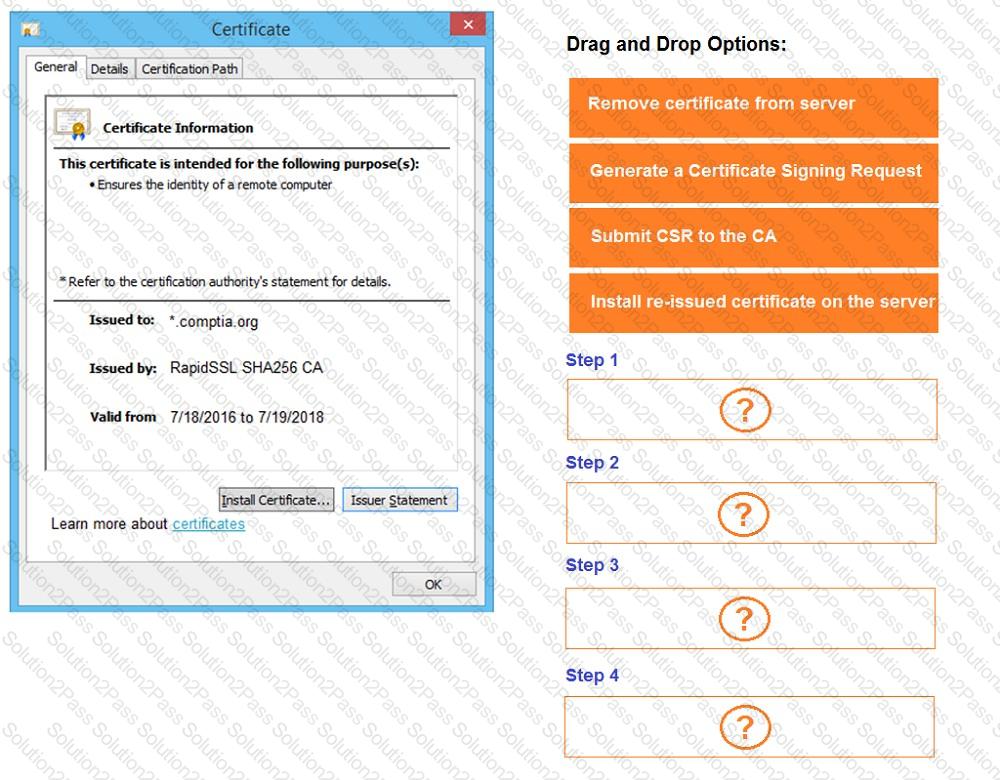
Given the following code:
Which of the following are the BEST methods to prevent against this type of attack? (Choose two.)
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
Appending string values onto another string is called:
A penetration tester is attempting to discover live hosts on a subnet quickly.
Which of the following commands will perform a ping scan?
A penetration tester has been hired to perform a physical penetration test to gain access to a secure room within a client’s building. Exterior reconnaissance identifies two entrances, a WiFi guest network, and multiple security cameras connected to the Internet.
Which of the following tools or techniques would BEST support additional reconnaissance?
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
Which of the following should a penetration tester consider FIRST when engaging in a penetration test in a cloud environment?
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
A penetration tester wants to validate the effectiveness of a DLP product by attempting exfiltration of data using email attachments. Which of the following techniques should the tester select to accomplish this task?
A penetration tester who is performing a physical assessment of a company’s security practices notices the company does not have any shredders inside the office building. Which of the following techniques would be BEST to use to gain confidential information?
A customer adds a requirement to the scope of a penetration test that states activities can only occur during normal business hours. Which of the following BEST describes why this would be necessary?
A security professional wants to test an IoT device by sending an invalid packet to a proprietary service listening on TCP port 3011. Which of the following would allow the security professional to easily and programmatically manipulate the TCP header length and checksum using arbitrary numbers and to observe how the proprietary service responds?
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the wmic.exe process call create function. Which of the following OS or filesystem mechanisms is MOST likely to support this objective?