ACCESS-DEF CyberArk Defender Access (ACC-DEF) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your CyberArk ACCESS-DEF CyberArk Defender Access (ACC-DEF) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You get the following error: "Not Authorized. You do not have permission to access this feature".
What is most likely the cause of the error?
Within a Web App connector, which feature does an admin use to grant users access?
Which dashboard can display the applications launched by users, the application type, and the number of times they were launched?
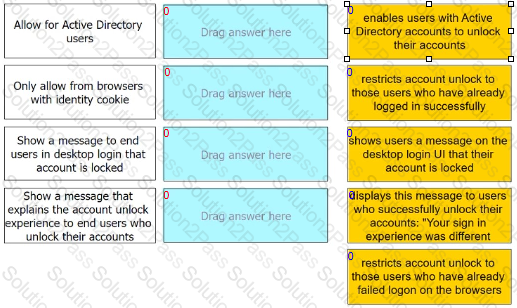
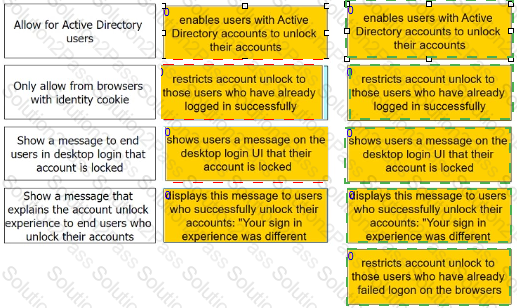
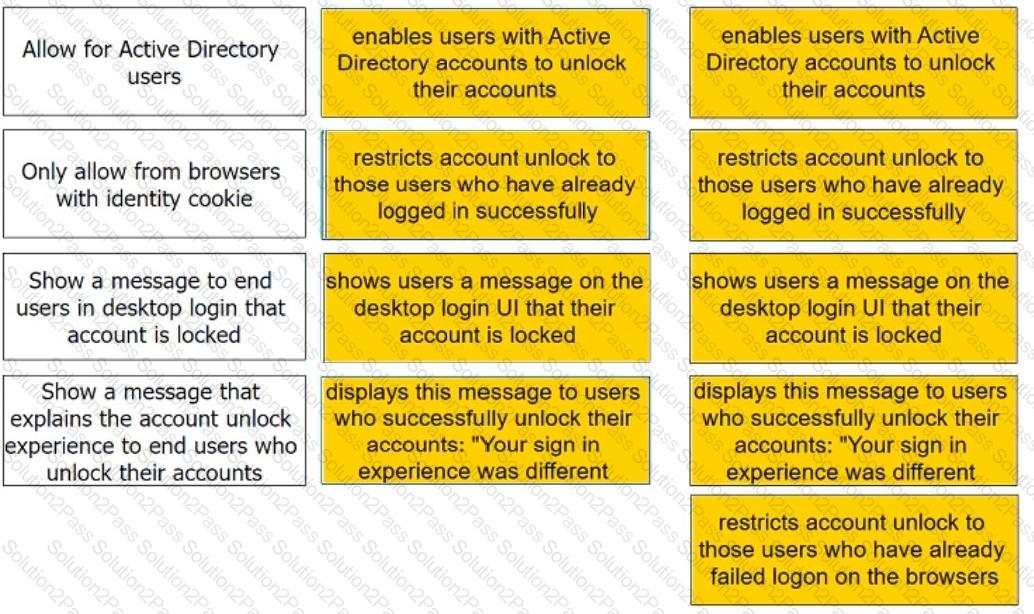
Admins can enable self-service for users to unlock their accounts. There are four options under the Admin Portal Core Services > Policies > User Security Policies > Self Service > Account Unlock options.
Match each option to the correct description.
What is the most likely reason a CyberArk Identity admin would turn on the "Provisioning" feature within a Web App connector?
Which settings can help minimize the number of 2FA / MFA prompts? (Choose two.)
Which predefined roles does CyberArk Identity provide?
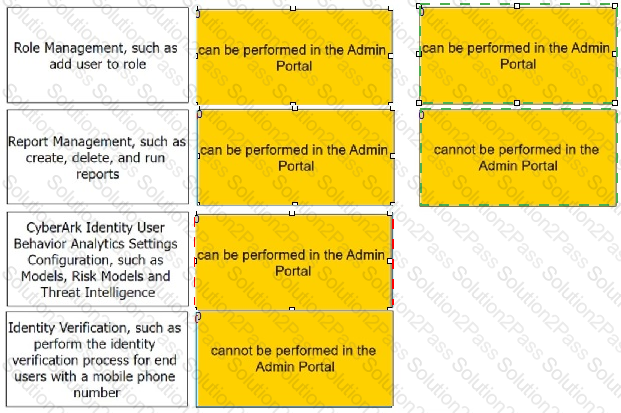
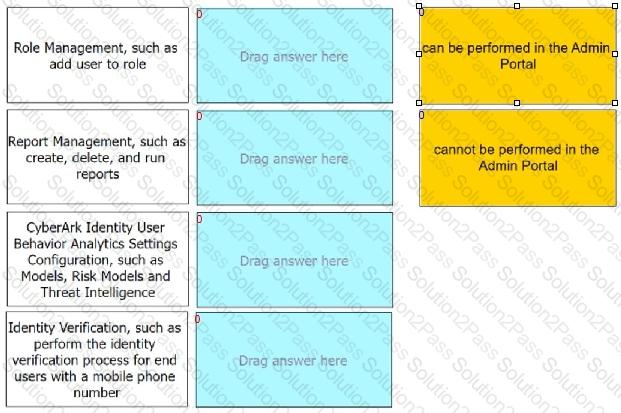
Match each listed task to indicate if an administrator can perform it in the Admin Portal.
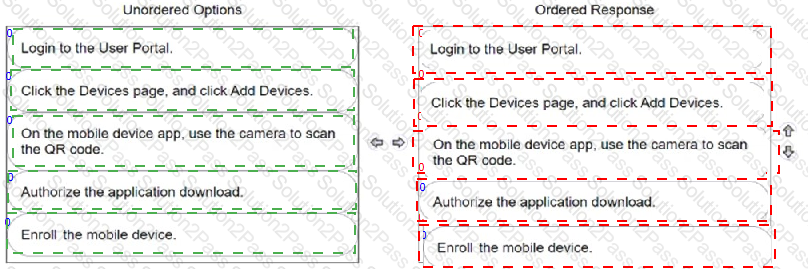
A user wants to install the CyberArk Identity mobile app by using a QR code.
Arrange the steps to do this in the correct sequence.

Which Custom Template app connectors are appropriate to use if a website does not require user authentication?
What does the CyberArk Identity App Gateway work with? (Choose three.)
Refer to the exhibit.
This exhibit shows the base authentication policy for ACME Corporation. You must edit the policy to allow users to authenticate once if they fulfill certain authentication criteria.
How should you configure this policy to support BOTH?
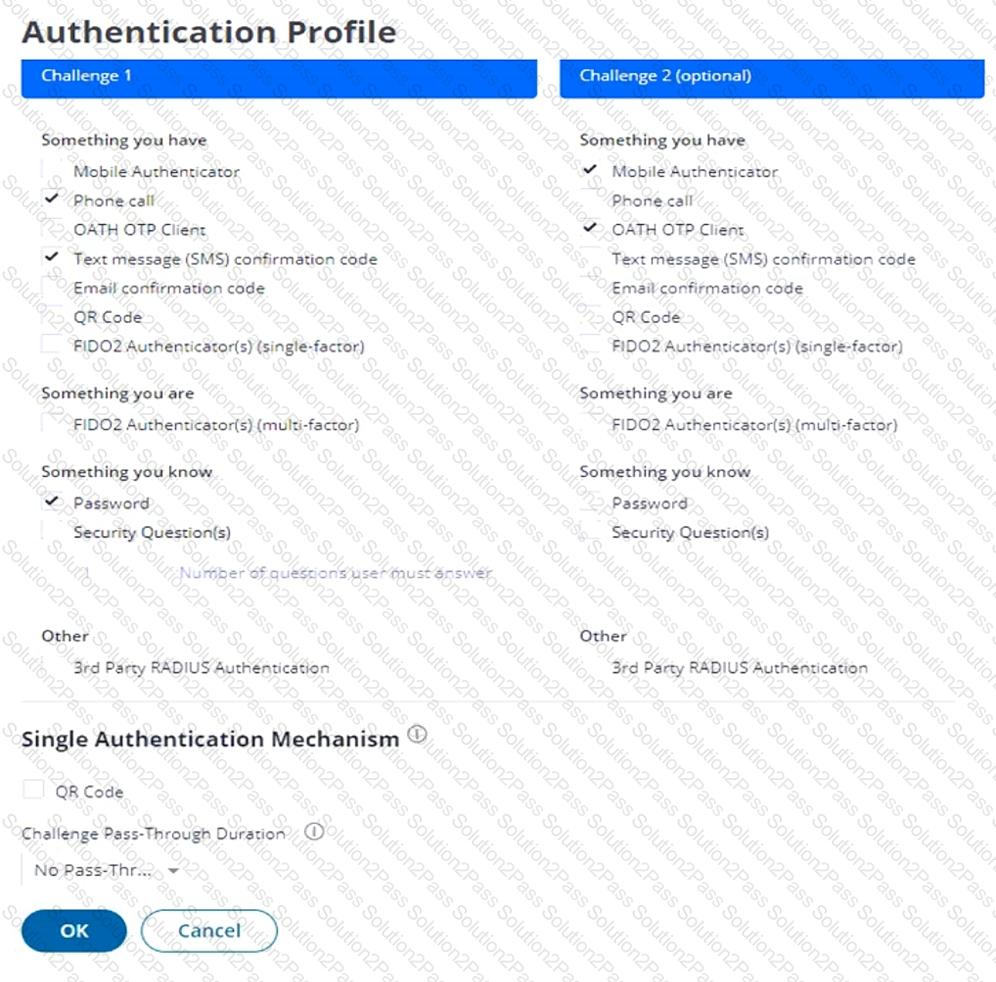
Which CyberArk Identity supported web standard is commonly used for enterprise Single Sign-On and issues XML tokens for authentication?
Your team is deploying endpoint authentication onto the corporate endpoints within an organization. Enrollment details include when the enrollment must be completed, and the enrollment code was sent out to the users. Enrollment can be performed in the office or remotely (without the assistance of an IT support engineer). You received feedback that many users are unable to enroll into the system using the enrollment code.
What can you do to resolve this? (Choose two.)
As part of an ongoing incident investigation, you want to examine all data/events that are relevant to updating user profiles.
Which dataset from the UBA portal should you use?
What does enabling "Workflow" allow within an app connector?
CyberArk Identity has created a CLI integration with which vendor?
Which device enrollment settings are valid? (Choose two.)
When a user enrolls a mobile device (iOS or Android) without enabling mobile device management, what happens? (Choose three.)
 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg