CPC-SEN CyberArk Sentry - Privilege Cloud Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CyberArk CPC-SEN CyberArk Sentry - Privilege Cloud certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Following the installation of the PSM for SSH server, which additional tasks should be performed? (Choose 2.)
Which option correctly describes the authentication differences between CyberArk Privilege Cloud and CyberArk PAM Self-Hosted?
What is the default username for the PSM for SSH maintenance user?
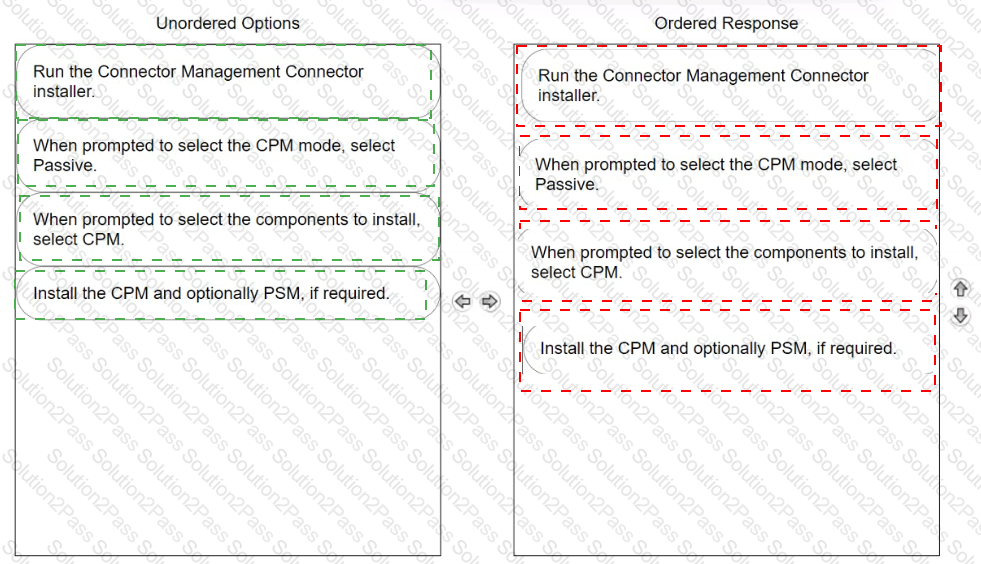
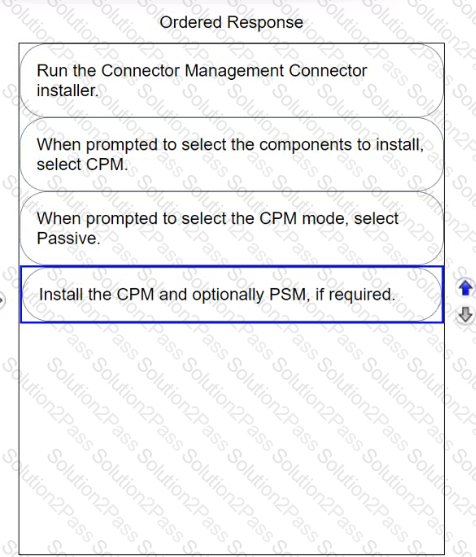
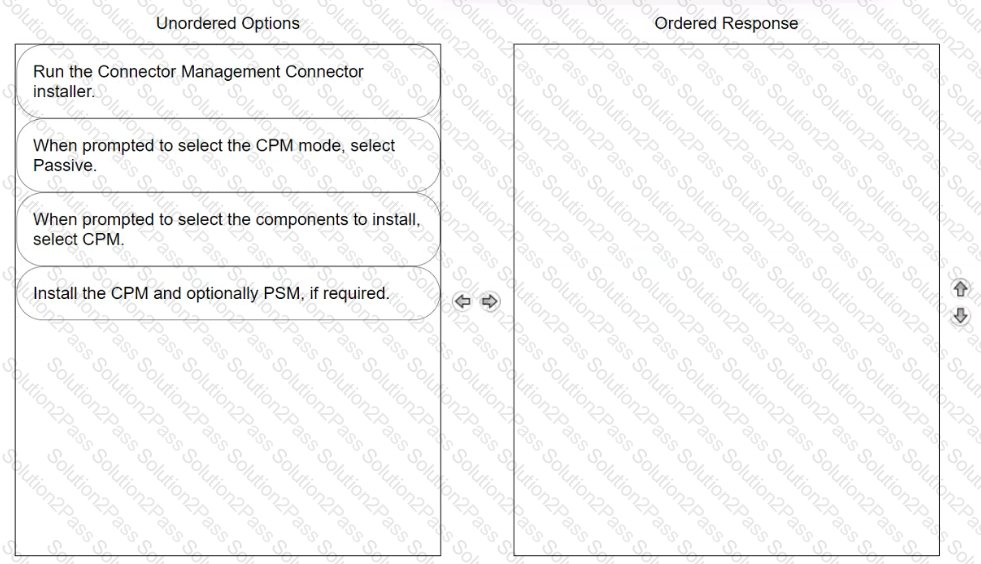
Arrange the steps to install passive CPM using Connector Management in the correct sequence
On Privilege Cloud, what can you use to update users' Permissions on Safes? (Choose 2.)
After correctly configuring reconciliation parameters in the Prod-AIX-Root-Accounts Platform, this error message appears in the CPM log: CACPM410E Ending password policy Prod-AIX-Root-Accounts since the reconciliation task is active but the AllowedSafes parameter was not updated What caused this situation?
On the CPM, you want to verify if DEP is disabled for the required executables According to best practices, which executables should be listed? (Choose 2.)
How can a platform be configured to work with load-balanced PSMs?
Which statement is correct about using the AllowedSafes platform parameter?
What is the recommended method to enable load balancing and failover of the CyberArk Identity Connector?
A CyberArk Privileged Cloud Shared Services customer asks you how to find recent failed login events for all users. Where can you do this without generating reports?
You are planning to configure Multi-Factor Authentication (MFA) for your CyberArk Privilege Cloud Shared Service. What are the available authentication methods?
What are the basic network requirements to deploy a CPM server?
Which tool configures the user object that will be used during the installation of the PSM for SSH component?
In the directory lookup order, which directory service is always looked up first for the CyberArk Privilege Cloud solution?