EPM-DEF CyberArk Defender - EPM Free Practice Exam Questions (2025 Updated)
Prepare effectively for your CyberArk EPM-DEF CyberArk Defender - EPM certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Before enabling Ransomware Protection, what should the EPM Administrator do first?
Which of the following application options can be used when defining trusted sources?
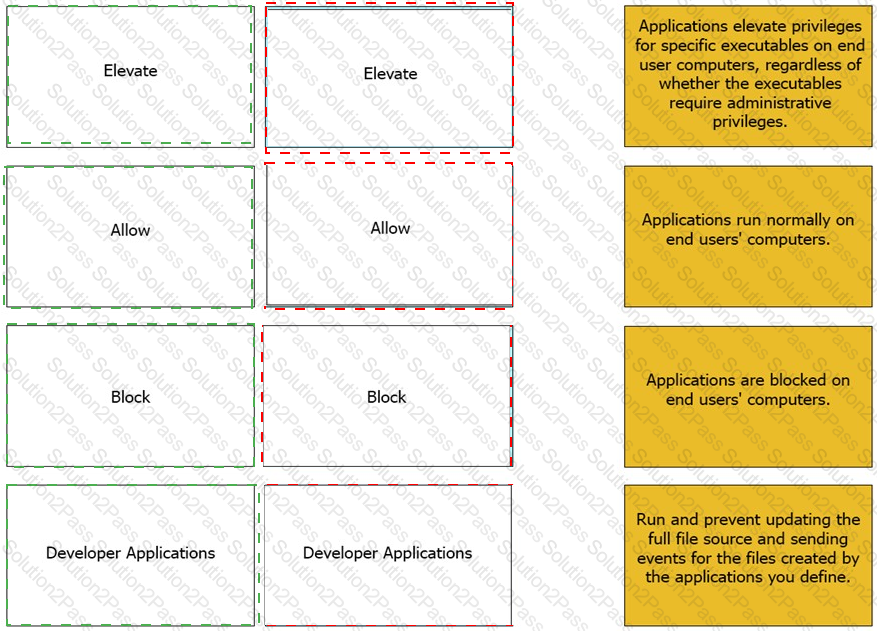
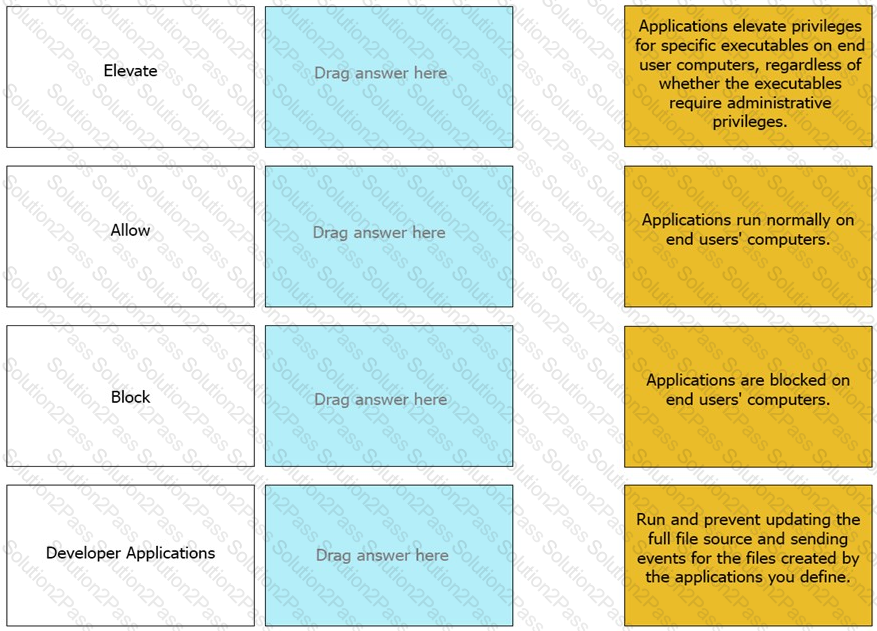
Match the Application Groups policy to their correct description.
Which user or group will not be removed as part of CyberArk EPM's Remove Local Administrators feature?
A company is looking to manage their Windows Servers and Desktops with CyberArk EPM. Management would like to define different default policies between the Windows Servers and Windows Desktops.
What should the EPM Administrator do?
For the CyberArk EPM Threat Deception Credential Lure feature, what is the recommendation regarding the username creation?
What is a valid step to investigate an EPM agent that is unable to connect to the EPM server?
A particular user in company ABC requires the ability to run any application with administrative privileges every day that they log in to their systems for a total duration of 5 working days.
What is the correct solution that an EPM admin can implement?
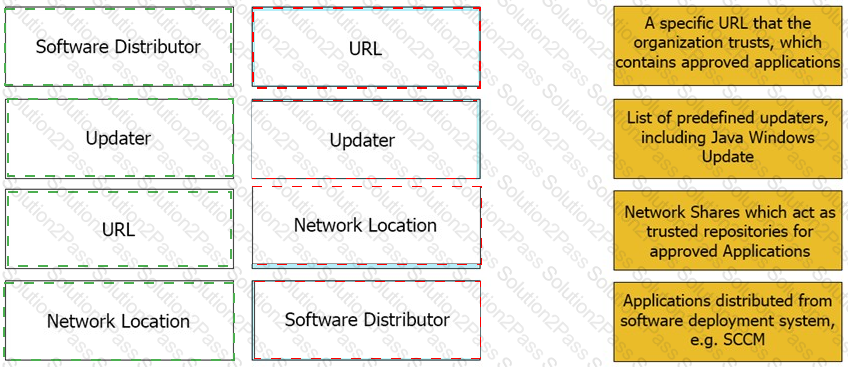
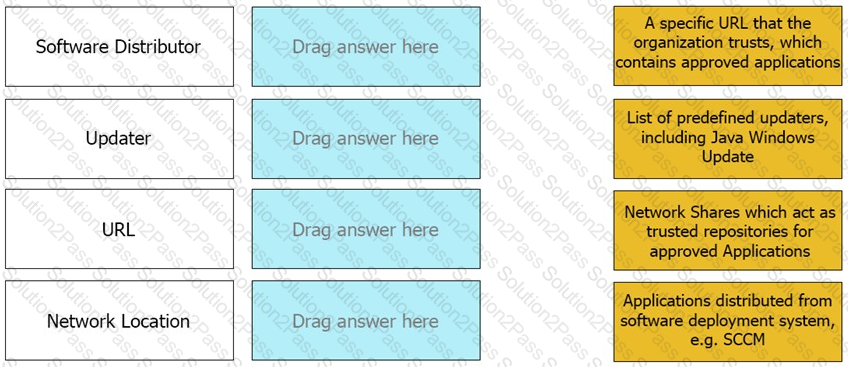
Match the Trusted Source to its correct definition:
CyberArk EPM's Ransomware Protection comes with file types to be protected out of the box. If an EPM Administrator would like to remove a file type from Ransomware Protection, where can this be done?
An application has been identified by the LSASS Credentials Harvesting Module.
What is the recommended approach to excluding the application?
Select the default threat intelligence source that requires additional licensing.
When blocking applications, what is the recommended practice regarding the end-user UI?
An end user is experiencing performance issues on their device after the EPM Agent had been installed on their machine. What should the EPM Administrator do first to help resolve the issue?
Where would an EPM admin configure an application policy that depends on a script returning true for an end user's machine being connected to an open (no password protection) Wi-Fi?
Where can you view CyberArk EPM Credential Lures events?
An EPM Administrator would like to exclude an application from all Threat Protection modules. Where should the EPM Administrator make this change?
What are Trusted sources for Windows endpoints used for?