SECRET-SEN CyberArk Sentry Secrets Manager Free Practice Exam Questions (2025 Updated)
Prepare effectively for your CyberArk SECRET-SEN CyberArk Sentry Secrets Manager certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
When working with Summon, what is the purpose of the secrets.yml file?
When installing the CCP and configuring it for use behind a load balancer, which authentication methods may be affected? (Choose two.)
When installing the Vault Conjur Synchronizer, you see this error:
Forbidden
Logon Token is Empty – Cannot logon
Unauthorized
What must you ensure to remediate the issue?
Which statement is correct about this message?
Message: “[number-of-deleted-rows] rows has successfully deleted “CEADBR009D Finished vacuum”?
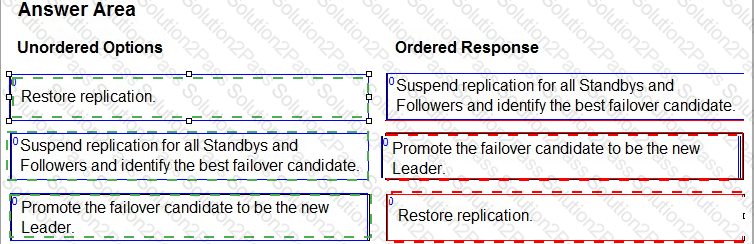
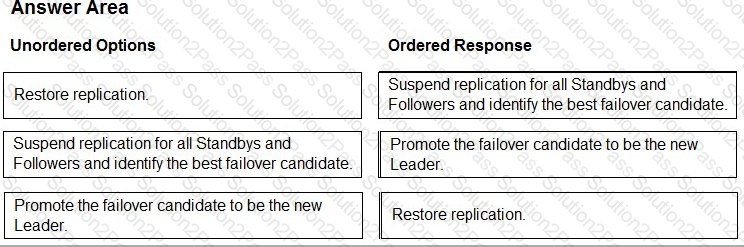
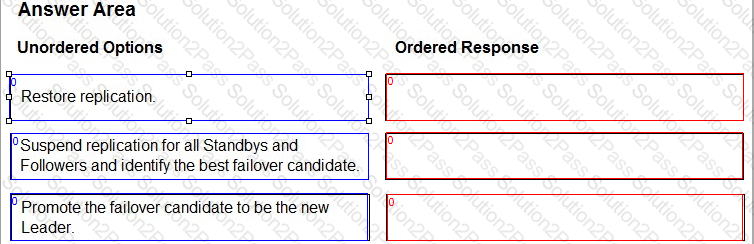
Arrange the manual failover configuration steps in the correct sequence.
You have a PowerShell script that is being used on 1000 workstations. It requires a Windows Domain credential that is currently hard coded in the script.
What is the simplest solution to remove that credential from the Script?
What is a possible Conjur node role change?
While retrieving a secret through REST, the secret retrieval fails to find a matching secret. You know the secret onboarding process was completed, the secret is in the expected safe with the expected object name, and the CCP is able to provide secrets to other applications.
What is the most likely cause for this issue?
You have a request to protect all the properties around a credential object. When configuring the credential in the Vault, you specified the address, user and password for the credential.
How do you configure the Vault Conjur Synchronizer to properly sync all properties?
In a 3-node auto-failover cluster, the Leader has been brought down for patching that lasts longer than the configured TTL. A Standby has been promoted.
Which steps are required to repair the cluster when the old Leader is brought back online?
While installing the first CP in an environment, errors that occurred when the environment was created are displayed; however, the installation procedure continued and finished successfully.
What should you do?
An application owner reports that their application is suddenly receiving an incorrect password. CPM logs show the password was recently changed, but the value currently being retrieved by the application is a different value. The Vault Conjur Synchronizer service is running.
What is the most likely cause of this issue?
A customer wants to ensure applications can retrieve secrets from Conjur in three different data centers if the Conjur Leader becomes unavailable. Conjur Followers are already deployed in each of these data centers.
How should you architect the solution to support this requirement?
Refer to the exhibit.
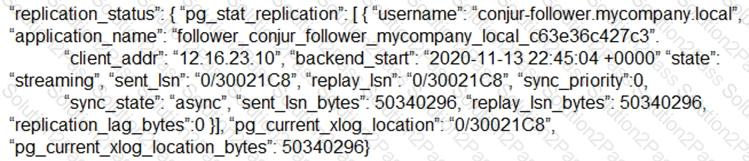
How can you confirm that the Follower has a current copy of the database?
When loading policy, you receive a 422 Response from Conjur with a message.
What could cause this issue?
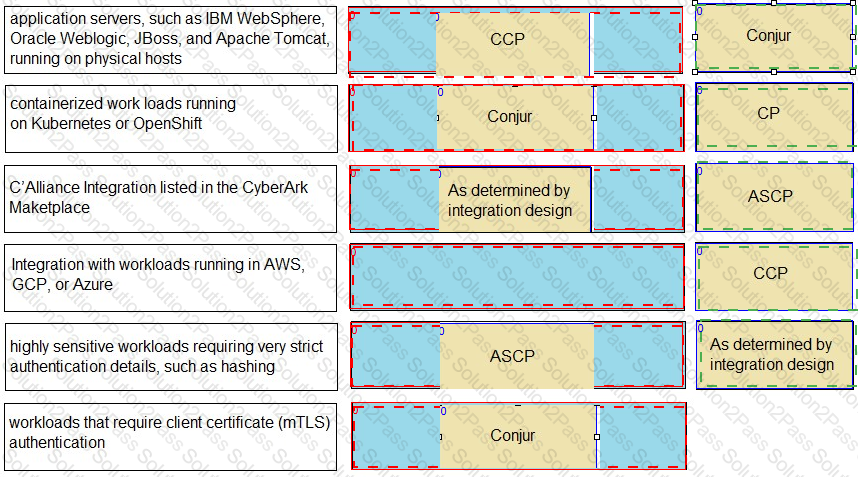
Match each use case to the appropriate Secrets Manager Solution.
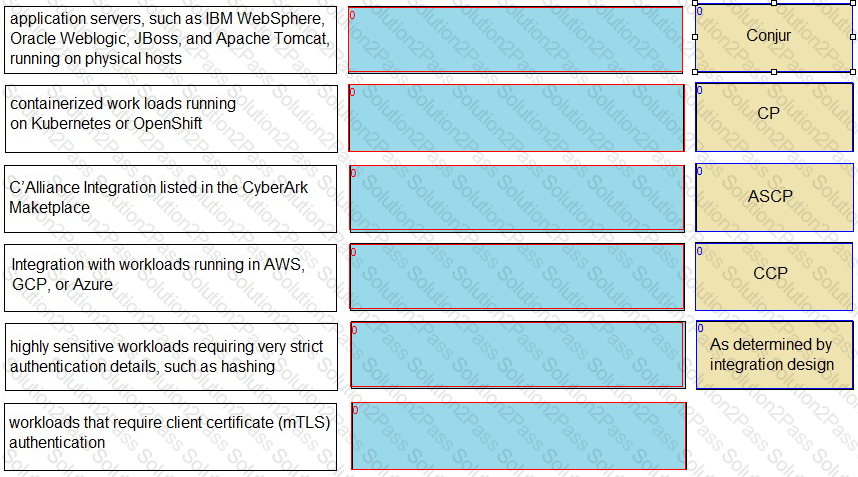
When working with Credential Providers in a Privileged Cloud setting, what is a special consideration?
What is the correct command to import the root CA certificate into Conjur?