312-38 ECCouncil Certified Network Defender (CND) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-38 Certified Network Defender (CND) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Identify the attack signature analysis technique carried out when attack signatures are contained in packet headers.
Which command is used to change the permissions of a file or directory?
Which of the following is a drawback of traditional perimeter security?
Which among the following options represents professional hackers with an aim of attacking systems for profit?
John wants to implement a firewall service that works at the session layer of the OSI model. The firewall must also have the ability to hide the private network information. Which type of firewall service is John thinking of
implementing?
The CEO of Max Rager wants to send a confidential message regarding the new formula for its coveted soft drink, SuperMax, to its manufacturer in Texas. However, he fears the message could be altered in
transit. How can he prevent this incident from happening and what element of the message ensures the success of this method?
Steven is a Linux system administrator at an IT company. He wants to disable unnecessary services in the system, which can be exploited by the attackers. Which among the following is the correct syntax for
disabling a service?
Kyle, a front office executive, suspects that a Trojan has infected his computer. What should be his first course of action to deal with the incident?
Implementing access control mechanisms, such as a firewall, to protect the network is an example of which of the following network defense approach?
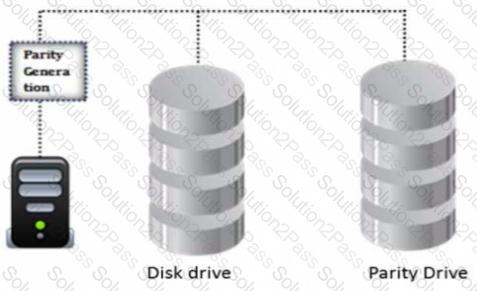
Identify the minimum number of drives required to setup RAID level 5.
Malone is finishing up his incident handling plan for IT before giving it to his boss for review. He is outlining the incident response methodology and the steps that are involved. What is the last step he should list?
Which VPN QoS model guarantees the traffic from one customer edge (CE) to another?
Which of the following systems includes an independent NAS Head and multiple storage arrays?
The agency Jacob works for stores and transmits vast amounts of sensitive government data that cannot be compromised. Jacob has implemented Encapsulating Security Payload (ESP) to encrypt IP traffic. Jacob
wants to encrypt the IP traffic by inserting the ESP header in the IP datagram before the transport layer protocol header. What mode of ESP does Jacob need to use to encrypt the IP traffic?
What is Azure Key Vault?
Which of the following DDoS attacks overloads a service by sending inundate packets?
Which of the following filters car be applied to detect an ICMP ping sweep attempt using Wireshark?
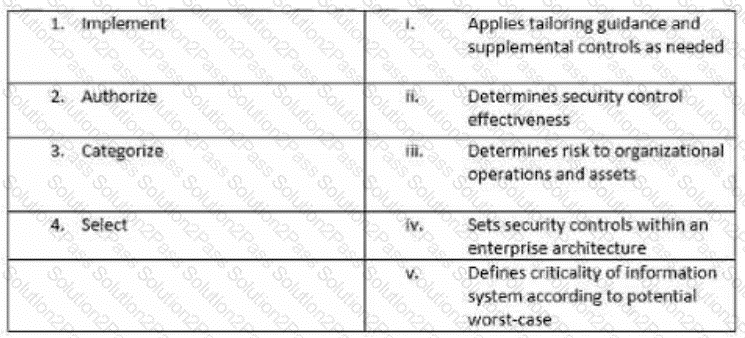
Match the following NIST security life cycle components with their activities:
Identify the firewall technology that monitors the TCP handshake between the packets to determine whether a requested session is legitimate.
Tom works as a network administrator in a multinational organization having branches across North America and Europe. Tom wants to implement a storage technology that can provide centralized data storage and
provide free data backup on the server. He should be able to perform data backup and recovery more efficiently with the selected technology. Which of the following storage technologies best suits Tom's requirements?
