312-49v9 ECCouncil Computer Hacking Forensic Investigator (v9) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-49v9 Computer Hacking Forensic Investigator (v9) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Identify the file system that uses $BitMap file to keep track of all used and unused clusters on a volume.
What technique is used by JPEGs for compression?
Self-Monitoring, Analysis, and Reporting Technology (SMART) is built into the hard drives to monitor and report system activity. Which of the following is included in the report generated by SMART?
What value of the "Boot Record Signature" is used to indicate that the boot-loader exists?
Which of the following is NOT an anti-forensics technique?
Which of the following processes is part of the dynamic malware analysis?
As a part of the investigation, Caroline, a forensic expert, was assigned the task to examine the transaction logs pertaining to a database named Transfers. She used SQL Server Management Studio to collect the active transaction log files of the database. Caroline wants to extract detailed information on the logs, including AllocUnitId, page id, slot id, etc. Which of the following commands does she need to execute in order to extract the desired information?
Which of the following is NOT an anti-forensics technique?
Which of the following registry hive gives the configuration information about which application was used to open various files on the system?
Which of these ISO standards define the file system for optical storage media, such as CD-ROM and DVD-ROM?
Which of the following does Microsoft Exchange E-mail Server use for collaboration of various e-mail applications?
Which of the following does not describe the type of data density on a hard disk?
What is the name of the first reserved sector in File allocation table?
Which of the following tool can reverse machine code to assembly language?
Graphics Interchange Format (GIF) is a ____ RGB bitmap image format for images with up to 256 distinct colors per frame.
Which of the following statements is incorrect when preserving digital evidence?
Which of the following tools is not a data acquisition hardware tool?
What malware analysis operation can the investigator perform using the jv16 tool?
A section of your forensics lab houses several electrical and electronic equipment. Which type of fire extinguisher you must install in this area to contain any fire incident?
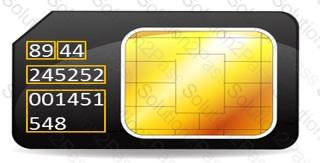
During an investigation, Noel found the following SIM card from the suspect's mobile. What does the code 89 44 represent?
Which among the following web application threats is resulted when developers expose various internal implementation objects, such as files, directories, database records, or key-through references?
Which of these rootkit detection techniques function by comparing a snapshot of the file system, boot records, or memory with a known and trusted baseline?
Which type of attack is possible when attackers know some credible information about the victim's password, such as the password length, algorithms involved, or the strings and characters used in its creation?
The Apache server saves diagnostic information and error messages that it encounters while processing requests. The default path of this file is usr/local/apache/logs/error.log in Linux. Identify the Apache error log from the following logs.
Which of the following email headers specifies an address for mailer-generated errors, like "no such user" bounce messages, to go to (instead of the sender's address)?
Which of the following web browser uses the Extensible Storage Engine (ESE) database format to store browsing records, including history, cache, and cookies?
Which of the following files store the MySQL database data permanently, including the data that had been deleted, helping the forensic investigator in examining the case and finding the culprit?
What is the role of Alloc.c in Apache core?
Consider that you are investigating a machine running an Windows OS released prior to Windows Vista. You are trying to gather information about the deleted files by examining the master database file named INFO2 located at C:\Recycler\
Jacob is a computer forensics investigator with over 10 years of experience in investigations and has written over 50 articles on computer forensics. He has been called upon as a qualified witness to testify the accuracy and integrity of the technical log files gathered in an investigation into computer fraud. What is the term used for Jacob’s testimony in this case?
