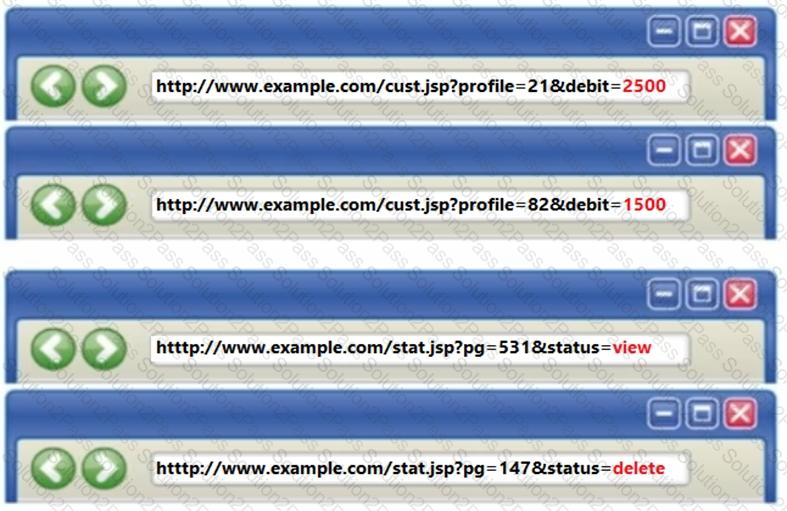
312-96 ECCouncil Certified Application Security Engineer (CASE) JAVA Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-96 Certified Application Security Engineer (CASE) JAVA certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
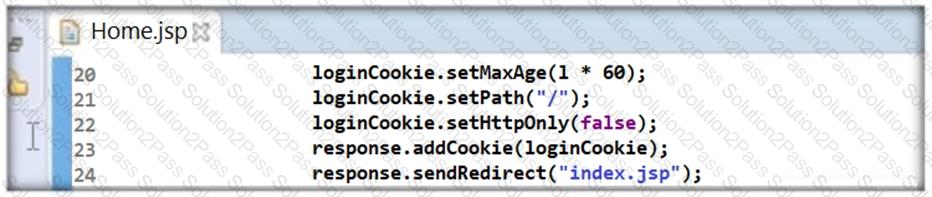
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of the consequences of insecure coding. One day, he wrote code as shown in the following screenshot. He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.
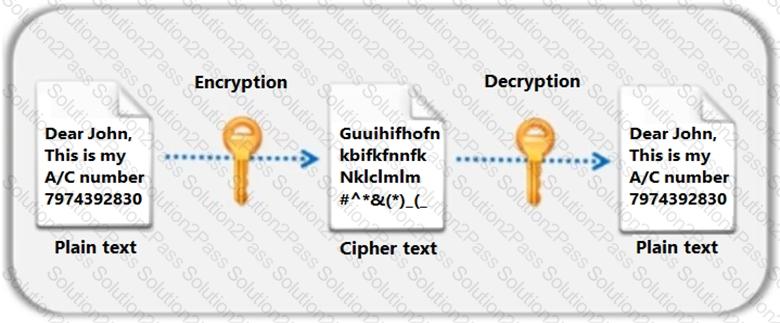
Identify the type of encryption depicted in the following figure.
Which of the threat classification model is used to classify threats during threat modeling process?
Which of the following can be derived from abuse cases to elicit security requirements for software system?
A developer to handle global exception should use _________ annotation along with @ExceptionHandler method annotation for any class
Alice, a security engineer, was performing security testing on the application. He found that users can view the website structure and file names. As per the standard security practices, this can pose a serious security risk as attackers can access hidden script files in your directory. Which of the following will mitigate the above security risk?
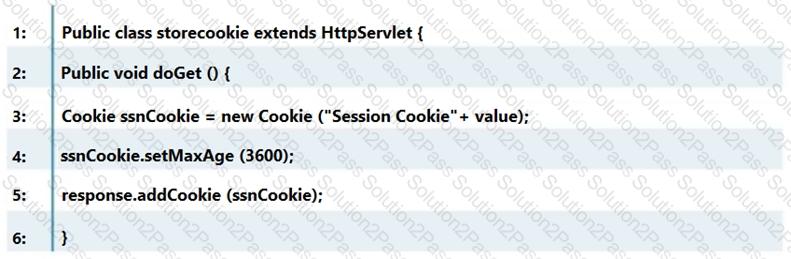
Which line of the following example of Java Code can make application vulnerable to a session attack?
The software developer has implemented encryption in the code as shown in the following screenshot.
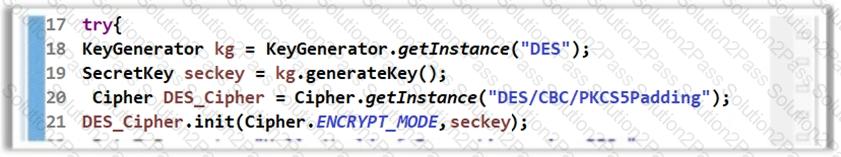
However, using the DES algorithm for encryption is considered to be an insecure coding practice as DES is a weak encryption algorithm. Which of the following symmetric encryption algorithms will you suggest for strong encryption?
Which of the following relationship is used to describe abuse case scenarios?
James is a Java developer working INFR INC. He has written Java code to open a file, read it line by line and display its content in the text editor. He wants to ensure that any unhandled exception raised by the code should automatically close the opened file stream. Which of the following exception handling block should he use for the above purpose?
Which of the following configuration settings in server.xml will allow Tomcat server administrator to impose limit on uploading file based on their size?
In a certain website, a secure login feature is designed to prevent brute-force attack by implementing account lockout mechanism. The account will automatically be locked after five failed attempts. This feature will not allow the users to login to the website until their account is unlocked. However, there is a possibility that this security feature can be abused to perform __________ attack.
It is recommended that you should not use return, break, continue or throw statements in _________
Identify the type of attack depicted in the following figure.