EC0-350 ECCouncil Ethical Hacking and Countermeasures V8 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil EC0-350 Ethical Hacking and Countermeasures V8 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is "Hacktivism"?
What port scanning method involves sending spoofed packets to a target system and then looking for adjustments to the IPID on a zombie system?
Which one of the following is defined as the process of distributing incorrect Internet Protocol (IP) addresses/names with the intent of diverting traffic?
What are the default passwords used by SNMP? (Choose two.)
A person approaches a network administrator and wants advice on how to send encrypted email from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following is the most secure encryption protocol that the network administrator should recommend?
Sandra is the security administrator of XYZ.com. One day she notices that the XYZ.com Oracle database server has been compromised and customer information along with financial data has been stolen. The financial loss will be estimated in millions of dollars if the database gets into the hands of competitors. Sandra wants to report this crime to the law enforcement agencies immediately.
Which organization coordinates computer crime investigations throughout the United States?
Your XYZ trainee Sandra asks you which are the four existing Regional Internet Registry (RIR's)?
Bob is acknowledged as a hacker of repute and is popular among visitors of “underground” sites. Bob is willing to share his knowledge with those who are willing to learn, and many have expressed their interest in learning from him. However, this knowledge has a risk associated with it, as it can be used for malevolent attacks as well.
In this context, what would be the most affective method to bridge the knowledge gap between the “black” hats or crackers and the “white” hats or computer security professionals? (Choose the test answer)
Exhibit
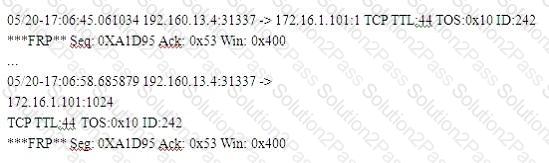
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.)
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
What does a type 3 code 13 represent?(Choose two.
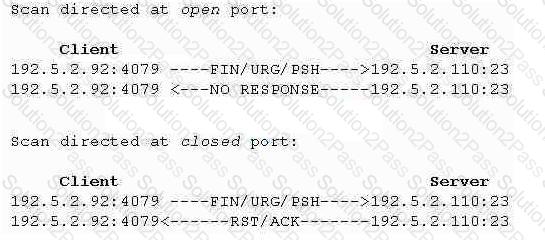
What type of port scan is shown below?
The following excerpt is taken from a honeyput log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. Study the log given below and answer the following question:
(Note: The objective of this questions is to test whether the student has learnt about passive OS fingerprinting (which should tell them the OS from log captures): can they tell a SQL injection attack signature; can they infer if a user ID has been created by an attacker and whether they can read plain source – destination entries from log entries.)
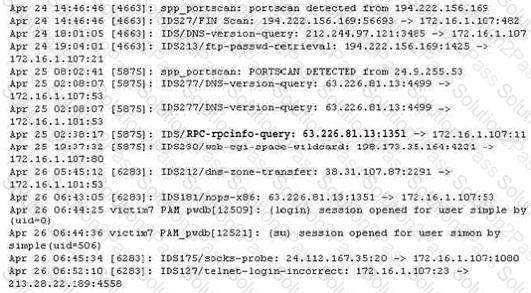
What can you infer from the above log?
You are conducting a port scan on a subnet that has ICMP blocked. You have discovered 23 live systems and after scanning each of them you notice that they all show port 21 in closed state.
What should be the next logical step that should be performed?
An nmap command that includes the host specification of 202.176.56-57.* will scan _______ number of hosts.
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is just called "file.txt" but when he opens it, he finds the following:
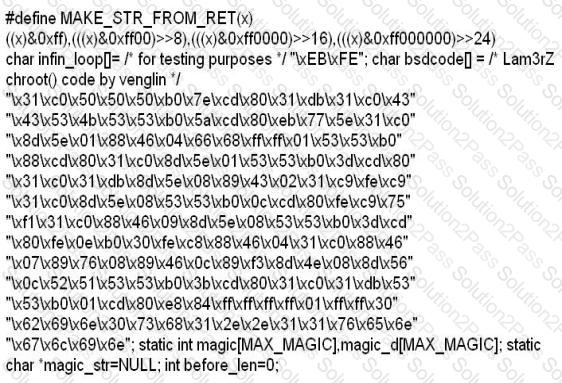
What can he infer from this file?
Sandra has been actively scanning the client network on which she is doing a vulnerability assessment test. While conducting a port scan she notices open ports in the range of 135 to 139. What protocol is most likely to be listening on those ports?
One of your team members has asked you to analyze the following SOA record. What is the version?
Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600
3600 604800 2400.
__________ is found in all versions of NTFS and is described as the ability to fork file data into existing files without affecting their functionality, size, or display to traditional file browsing utilities like dir or Windows Explorer
What does the term “Ethical Hacking” mean?
Bob has been hired to perform a penetration test on XYZ.com. He begins by looking at IP address ranges owned by the company and details of domain name registration. He then goes to News Groups and financial web sites to see if they are leaking any sensitive information of have any technical details online.
Within the context of penetration testing methodology, what phase is Bob involved with?
At a Windows Server command prompt, which command could be used to list the running services?
Which of the following is an automated vulnerability assessment tool?
The use of alert thresholding in an IDS can reduce the volume of repeated alerts, but introduces which of the following vulnerabilities?
What flags are set in a X-MAS scan?(Choose all that apply.
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
What are two things that are possible when scanning UDP ports? (Choose two.
Which property ensures that a hash function will not produce the same hashed value for two different messages?
Which of the following descriptions is true about a static NAT?
Which of the following levels of algorithms does Public Key Infrastructure (PKI) use?
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
Which of the following business challenges could be solved by using a vulnerability scanner?
Which of the following resources does NMAP need to be used as a basic vulnerability scanner covering several vectors like SMB, HTTP and FTP?
Fingerprinting VPN firewalls is possible with which of the following tools?
Which of the following is a primary service of the U.S. Computer Security Incident Response Team (CSIRT)?
The Open Web Application Security Project (OWASP) testing methodology addresses the need to secure web applications by providing which one of the following services?
WPA2 uses AES for wireless data encryption at which of the following encryption levels?
An NMAP scan of a server shows port 25 is open. What risk could this pose?
Which of the following defines the role of a root Certificate Authority (CA) in a Public Key Infrastructure (PKI)?
Which of the following techniques will identify if computer files have been changed?
The network administrator for a company is setting up a website with e-commerce capabilities. Packet sniffing is a concern because credit card information will be sent electronically over the Internet. Customers visiting the site will need to encrypt the data with HTTPS. Which type of certificate is used to encrypt and decrypt the data?
