D-ISM-FN-23 EMC Dell Information Storage and Management Foundations 2023 Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your EMC D-ISM-FN-23 Dell Information Storage and Management Foundations 2023 Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An Ethernet switch has eight ports and all ports must be operational for 24 hours; from Monday through Friday. However, a failure of Port 5 occurs as follows:
Tuesday = 6 AM to 7 AM Thursday = 5 PM to 9 PM Friday = 8 AM to 9 AM
What is the MTBF of Port 5?
If the erasure coding technique used divides data into 12 data segments and 5 coding segments, what is the maximum number of disk drive failures against which data is protected by the configuration?
In a RAID 6 array with four disks, what is the total usable data storage capacity on the array if the disk size is 200 GB?
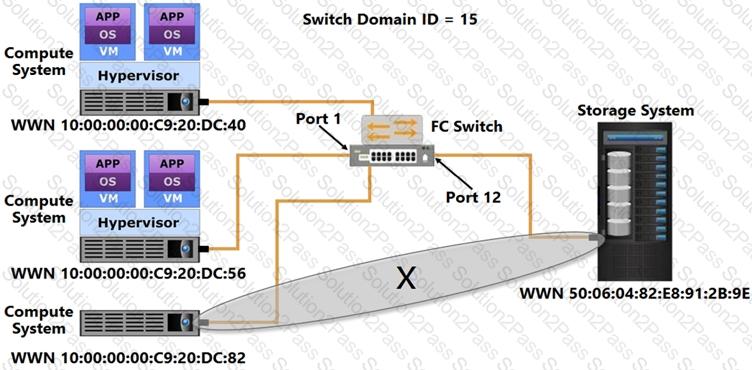
Which type of zoning does the “X” represent?
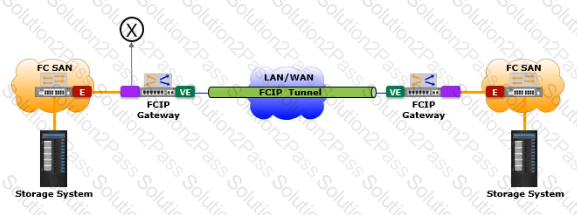
Based on the exhibit, what does the "X" represent in the FCIP tunnel configuration?
What is an accurate statement regarding virtual LANs?
Which is a characteristic of RAID 6?
A company finance department needs 250 GB of storage for their business applications. A LUN is created with 250 GB, and RAID 1 protection. The LUN is configured to support application I/O performance.
If storage cost is $2 per GB, what is the chargeback amount to the department for application storage?
An organization is planning to adopt pre integrated systems to deploy compute, network, storage, and management functions as a single engineered solution.
Which approach should the organization adopt?
What occurs during a Shared Technology Vulnerability threat?
Which storage management function ensures that the services and service levels are delivered per SLAs?
Which loT architecture component provides the connection to monitor and control user devices? (First Choose Correct option and give detailed explanation delltechnologies.com)
What functionality does the control layer provide in a software-defined networking architecture?
An organization wants to deploy a VM storage migration solution into their data center environment.
What is the result of deploying this type of solution?
What statement describes machine learning?
What is an advantage of deploying intelligent storage systems in the data center?
What is a benefit of using a Scale-Out NAS system vs. general purpose file servers?
What is an accurate statement about Challenge Handshake Authentication Protocol (CHAP) control?
Which Connectrix FC switch model supports NVMe in a 32Gb/s SAN fabric exclusively?
In continuous data protection, what does the amount of journal space determine?
