DES-9131 EMC Specialist - Infrastructure Security Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your EMC DES-9131 Specialist - Infrastructure Security Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which NIST Cybersecurity Framework function should be executed before any others?
What must be done before returning a compromised laptop to normal operations in the environment?
An organization has a policy to respond “ASAP” to security incidents. The security team is having a difficult time prioritizing events because they are responding to all of them, in order of receipt.
Which part of the IRP does the team need to implement or update?
What determines the technical controls used to restrict access to USB devices and help prevent their use
within a company?
What type of system processes information, the loss of which would have a debilitating impact to an
organization?
What are the four tiers of integration within the NIST Cybersecurity Framework?
Refer to the exhibit.
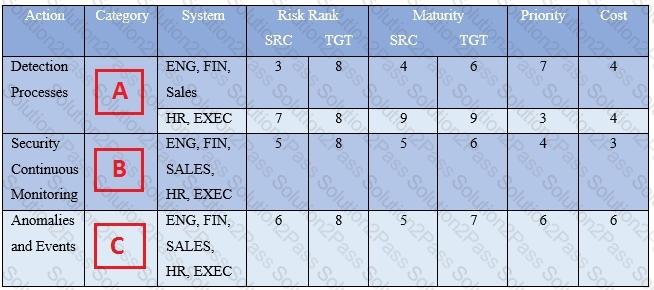
Your organization’s security team has been working with various business units to understand their business requirements, risk tolerance, and resources used to create a Framework Profile.
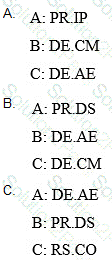
Based on the Profile provided, what entries correspond to labels A, B, and C?
What is the main goal of a gap analysis in the Identify function?
The network security team in your company has discovered a threat that leaked partial data on a compromised file server that handles sensitive information. Containment must be initiated and addresses by the CSIRT.
Service disruption is not a concern because this server is used only to store files and does not hold any critical workload. Your company security policy required that all forensic information must be preserved.
Which actions should you take to stop data leakage and comply with requirements of the company security policy?
The Backup Recovery Plan is dependent on what effort?
What are the five functions of the NIST Framework Core?
The CSIRT team is following the existing recovery plans on non-production systems in a PRE-BREACH
scenario. This action is being executed in which function?
You need to review your current security baseline policy for your company and determine which security
controls need to be applied to the baseline and what changes have occurred since the last update.
Which category addresses this need?
A continuously updated CMDB is an output of which NIST function and category?
You have been tasked with documenting mission critical procedures of an organization that need to be
sustained through a significant disruption.
What document would you develop?
What procedure is designed to enable security personnel to detect, analyze, contain, eradicate, respond, and
recover from malicious computer incidents such as a denial-of-service attack?
Which mechanism within the NIST Cybersecurity Framework describes a method to capture the current state and define the target state for understanding gaps, exposure, and prioritize changes to mitigate risk?
Your data center uses a diesel generator as backup for two different power grids provided by your regional power company. During a period of unprecedented heat, you experience brown-outs on both grids simultaneously. The diesel generator starts up but only runs for two minutes before it also shuts down, leaving your entire data center down until grid power can be restored. Further inspection reveals a clogged fuel filter.
Failing to schedule preventive service for the backup generator is a failure in which function?
