101 F5 Application Delivery Fundamentals Free Practice Exam Questions (2026 Updated)
Prepare effectively for your F5 101 Application Delivery Fundamentals certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
HTTP pool attached to a Virtual Server has three members
Pool member A default HTTP monitor in red
Pool member 6 custom HTTP monitor in green
Pool member C does not monitor
Which pool members participate in the load balancing?
A BIG IP Administrator observes that the pool member status is a blue square What does this status indicate?
Which HTTP response code indicates an OK status?
Which security model provides protection from unknown attacks?
In an administrator's environment, the administrator wants to inspect a high volume of SSL traffic
What should be used for this task?
An administrator security policy defines allowed URLs, file types and parameter values Which security model is the administrator using?
What is a benefit of configuring BIG-IP devicesin active-active high availabilitymode?
An administrator connects two devices using an Ethernet cable. The link fails to come up on either device, which setting could prevent the link from being established?
HTTPS traffic is being passed from behind a NAT router, through a load balancer, to servers without being decrypted.
What is the F5-recommended persistence method in this situation?
An administrator needs to create a structured application delivery configuration that will prevent individual objects from being modified directly
Which F5 technology should the administrator use?
A BIG-IP administrator is interested in using some of the vCMP
What should impact the administrator's decision?

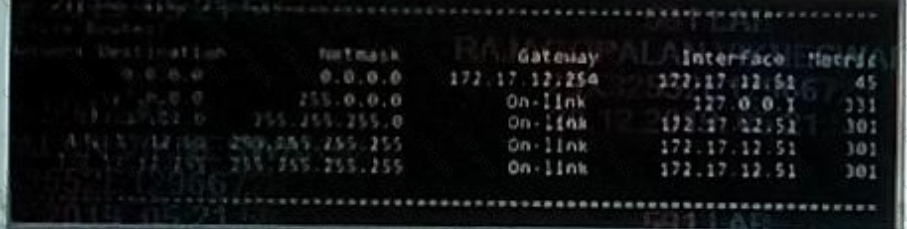
An administrator is trying to debug why the 10.0.10.0/24 network is inaccessible from a certain server. The server is able to access the internet Successfully.
The administrator inspects the routing table and ARP table on the affected server.
Given the terminal output shown, what could be causing this issue?
Which device group type allows a BIG IP system to automatically become active in the event that the current active system fails?
in which scenario is a full proxy TCP connection required?
A BIG-IP Administrator needs to create a route to send traffic destined to 10.1.1 1 to another router with an address of 192 168 1 1 Which TMSH command should the administrator use?
What is the nest hop used to send traffic to reach 192.168.1.50?
A BIG-IP Administrator wants to send packets from one subnet to another. What device is required to allow this to function?
In which scenario does the client act as a server?
Which support service is required to synchrony the time stamps in system logs from these devices?
A BIO IP Administrator is troubleshooting a slow web application. A packet capture shows that some of the packets coming from a window size of zero A packet capture shows that som a window size of zero
What does this mean?
