771-101 F5 Application Delivery Fundamentals Free Practice Exam Questions (2026 Updated)
Prepare effectively for your F5 771-101 Application Delivery Fundamentals certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What are the two primary functions of the OSI 7 layer model (Choose two)
Which security mode. functions by defining what traffic is allowed and rejecting all other traffic?
In the Network Map a red diamond appears next to the three member servers in the Virtual Server’s pool. The nodes in the pool each show a green circle. What is the most likely reason for this scenario?
AD VLAN must be created with an 802.19 tag of 705 on interface 11. What is the proper TSH command to create this new VLAN on the BIG-IP?
Where is the MAC masquerade address configured?
An administrator needs to prepare change control documents for operations staff To reduce possible errors the administrator killed number of default configuration options is choose from. Which F5 feature is intended to help with this task?
A BIG IP Administrator configures three Network Time Protocol servers to keep the time of the devices in sync. Which tool should the administrator use to show the synchronization status with the Network Time Protocol servers?
Which protocol data unit (POU) is associated with the OSI model’s Network layer
An application has a mix of both and short and long lived connections. Which algorithm would provide and event distributionof all connections across the pool?
A BIO IP Administrator is troubleshooting a slow web application. A packet capture shows that some of the packets coming from a window size of zero A packet capture shows that som a window size of zero
What does this mean?
An administrator needs to selectively compress HTTP traffic based on geographical location Which FS Feature should the administrator use?
A BIG IP administrator is testing a web server behind ADC. The connection to a Virtual Server is successful but the page is still not loading Where should the administrator test to determine if theserver is available?
What is used to establish trust relationships between BIG-IP devices?
An administrator encounter an error while working on eBiG.IP device and contacts F5 Support to open a case. While opening the case Support of the administrator that a BIO-IP version update is required.
Which F5 Support policy requires the administrator to upgrade the BIG-IP version.
Tl SISSL prides which functionary when a web browser connects to web site using the HTTPS protocol?
What is a common use of an iRule?
An administrator needs to create a structured application delivery configuration that will prevent individual objects from being modified directly
Which F5 technology should the administrator use?
The BIG-IP device has the following configured routes:
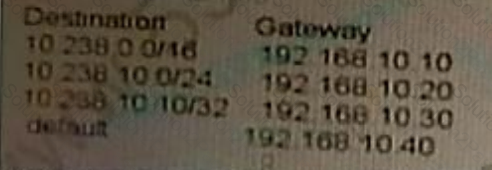
Which gateway will be chosen to send the packet to the destination 10 238 10 11?
ARP provides translation between which two address types?
An administrator needs to lower .he amount of new TCP connections to help with network congest?
How should the administrator accomplish this?
