FCP_FCT_AD-7.4 Fortinet NSE 6 - FortiClient EMS 7.4 Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet FCP_FCT_AD-7.4 Fortinet NSE 6 - FortiClient EMS 7.4 Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which security fabric component sends a notification to quarantine an endpoint after IOC detection in the automation process?
A new chrome book is connected in a school's network.
Which component can the EMS administrator use to manage the FortiClient web filter extension installed on the Google Chromebook endpoint?
Refer to the exhibit.
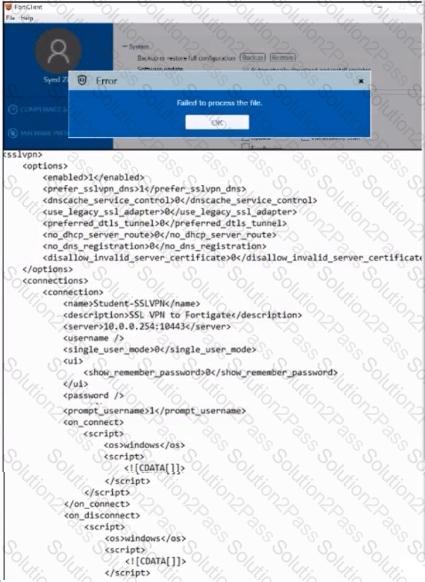
An administrator has restored the modified XML configuration file to FortiClient and sees the error shown in the exhibit.
Based on the XML settings shown in the exhibit, what must the administrator do to resolve the issue with the XML configuration file?
Which two statements apply to FortiClient forensics analysis? (Choose two answers)
Refer to the exhibits.

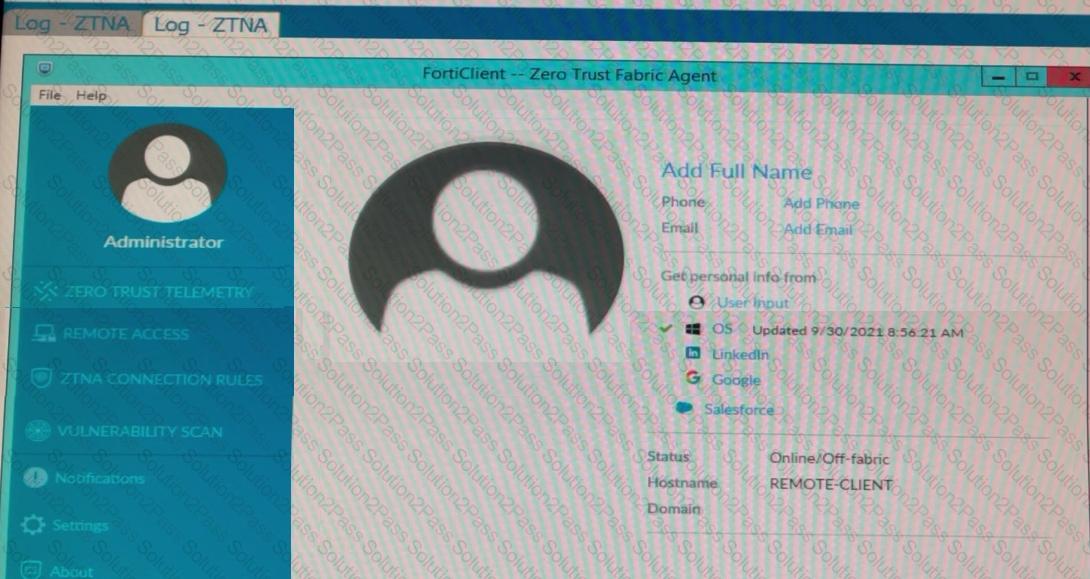
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
Which three features does FortiClient endpoint security include? (Choose three.)
Which statement about FortiClient enterprise management server is true?
Which component or device shares ZTNA tag information through Security Fabric integration?
An administrator wants to simplify remote access without asking users to provide user credentials Which access control method provides this solution?
ZTNA Network Topology

Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-Client endpoint information, however Remote-Client is not showing up in the endpoint record list.
What is the cause of this issue?
Refer to the exhibits.
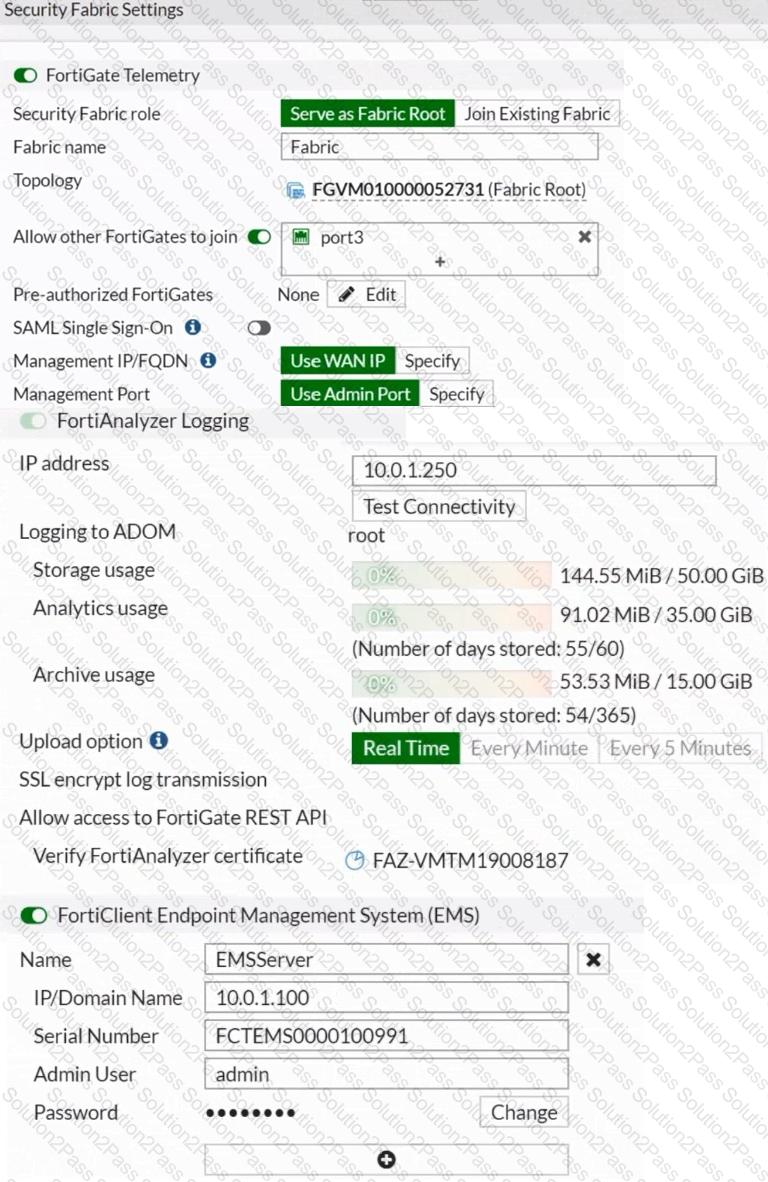
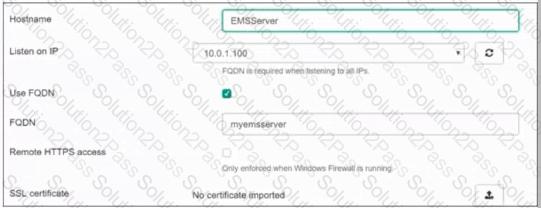
Based on the FortiGate Security Fabric settings shown in the exhibits, what must an administrator do on the EMS server to successfully quarantine an endpoint. when it is detected as a compromised host (loC)?
Refer to the exhibit, which shows the endpoint summary information on FortiClient EMS.
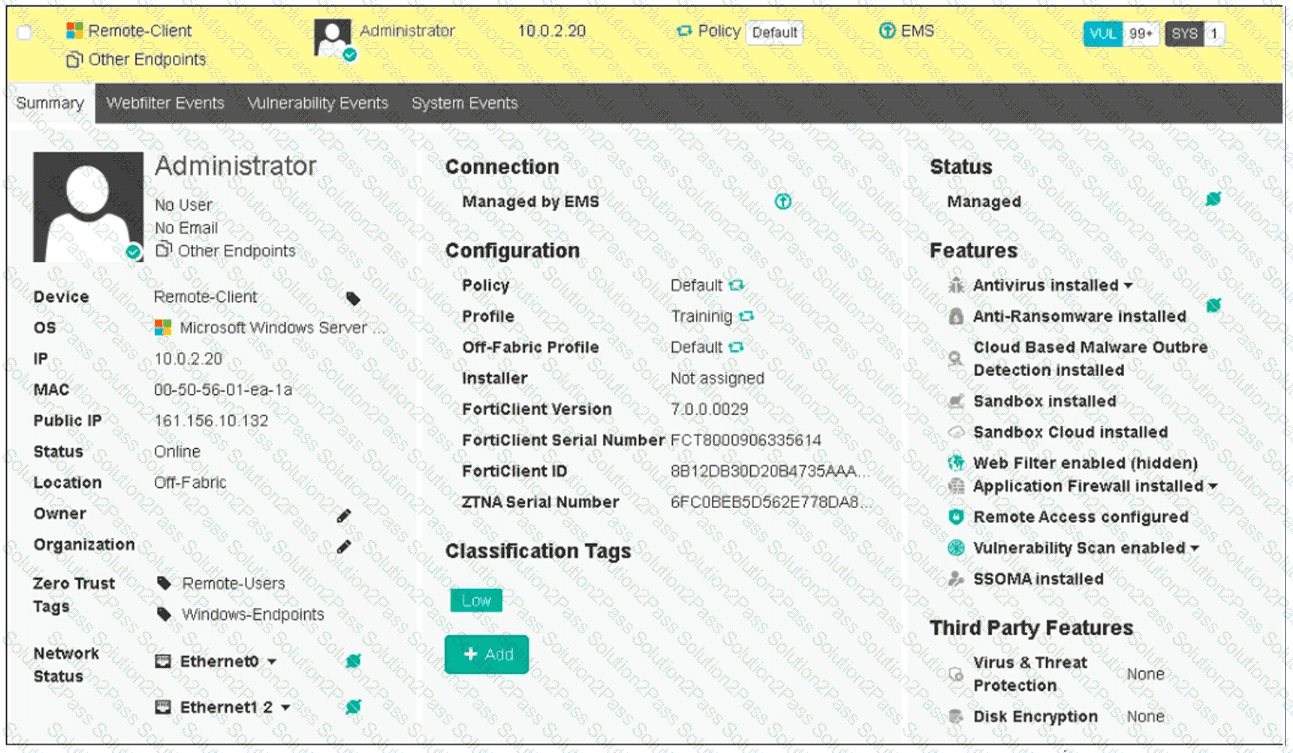
What two conclusions can you make based on the Remote-Client status shown above? (Choose two.)
Refer to the exhibit.

Based on the FortiClient logs shown in the exhibit which application is blocked by the application firewall?
Exhibit.
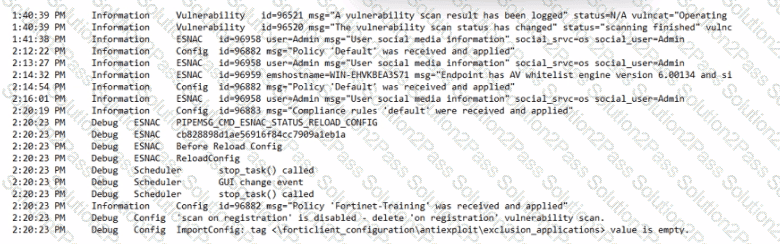
Based on the FortiClient logs shown in the exhibit, which endpoint profile policy is currently applied lo the ForliClient endpoint from the EMS server?
An administrator must add an authentication server on FortiClient EMS in a different security zone that cannot allow a direct connection.
Which solution can provide secure access between FortiClient EMS and the Active Directory server?
Refer to the exhibit.
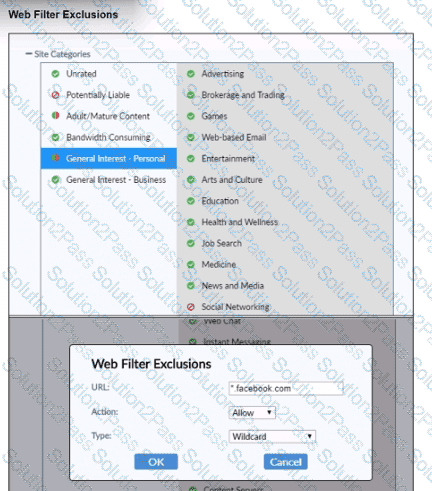
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www facebook com?
An administrator has lost web access to the FortiClient EMS console, and the web page to access to the console is timing out.
How can the administrator gather information to investigate the issue? (Choose one answer)
Refer to the exhibit.

Based on the CLI output from FortiGate. which statement is true?
A company must integrate the FortiClient EMS with their existing identity management infrastructure for user authentication, and implement and enforce administrative access with multi-factor authentication (MFA). Which two authentication methods can they use in this scenario? (Choose two answers)
Exhibit.
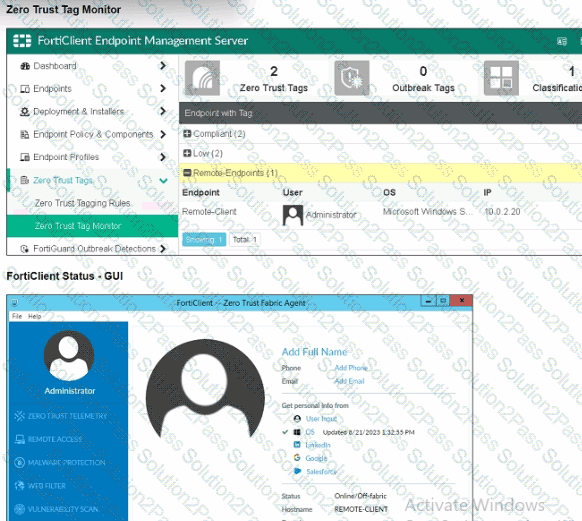
Refer to the exhibits, which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-User* on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
