FCP_FWB_AD-7.4 Fortinet FCP - FortiWeb 7.4 Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet FCP_FWB_AD-7.4 FCP - FortiWeb 7.4 Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.
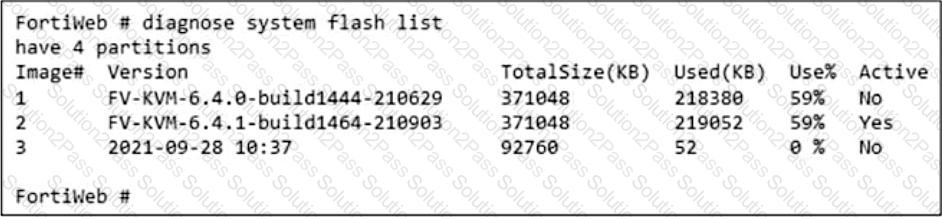
What is true about this FortiWeb device? (Choose two.)
When is it possible to use a self-signed certificate, rather than one purchased from a commercial certificate authority?
Refer to the exhibit.
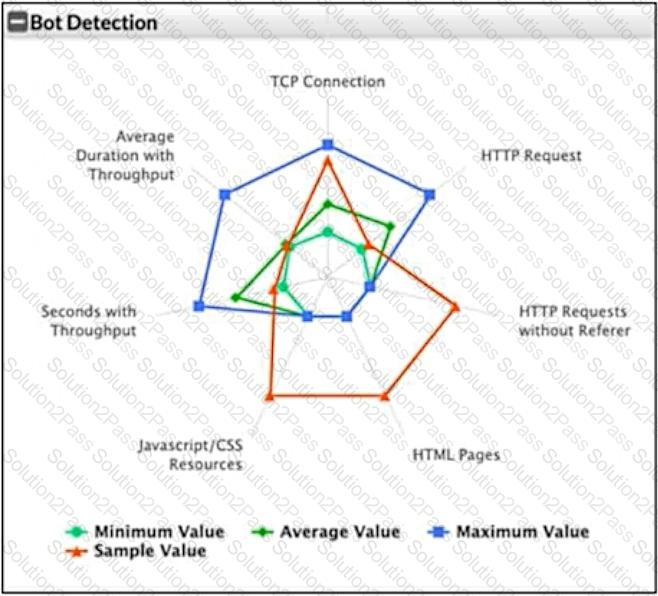
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?
Which two items can be defined in a FortiWeb XML Protection Rule? (Choose two.)
How are bot machine learning (ML) models different from API or anomaly detection models?
Which two statements about running a vulnerability scan are true? (Choose two.)
What are two possible impacts of a DoS attack on your web server? (Choose two.)
Refer to the exhibit.
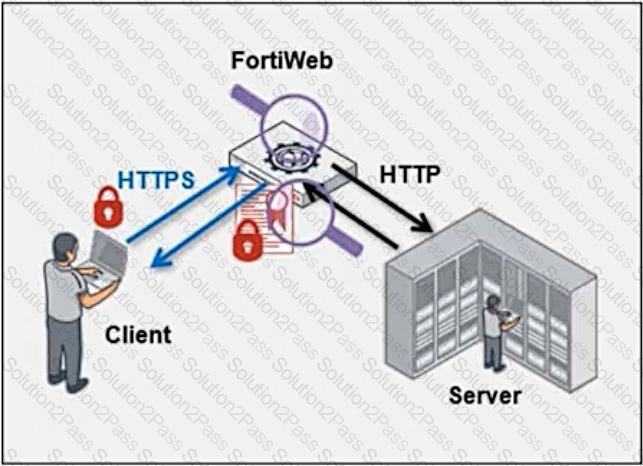
Which statement is true?
Which three stages are part of creating a machine learning (ML) bot detection algorithm? (Choose three.)
Refer to the exhibit.
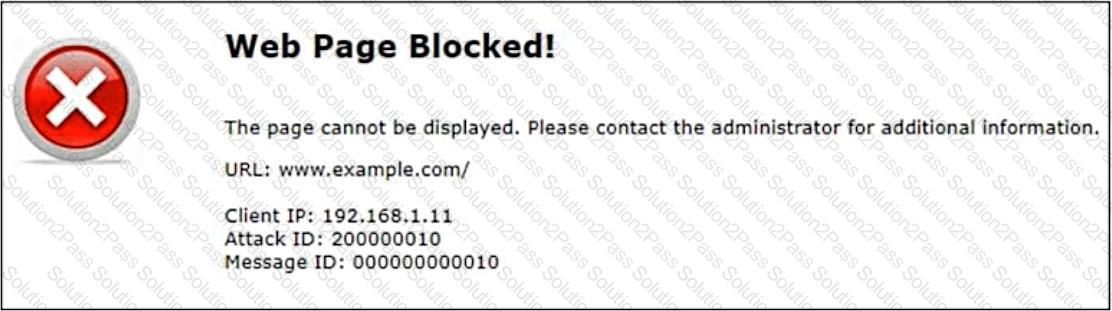
Attack ID20000010is brute force logins.
Which statement is accurate about the potential attack?
