FCSS_NST_SE-7.6 Fortinet NSE 6 - Network Security 7.6 Support Engineer Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet FCSS_NST_SE-7.6 Fortinet NSE 6 - Network Security 7.6 Support Engineer certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
The local OSPF router is unable to establish adjacency with a peer.
Which two things should the administrator do to troubleshoot the issue? (Choose two.)
When FortiGate enters conserve mode because of memory pressure, which action can FortiGate perform to preserve memory?
Which statement about parallel path processing is correct (PPP)?
Exhibit.

Refer to the exhibit, which shows two entries that were generated in the FSSO collector agent logs.
What three conclusions can you draw from these log entries? {Choose three.)
During which phase of IKEv2 does the Diffie-Helman key exchange take place?
Refer to the exhibit, which shows the output o! the BGP database.
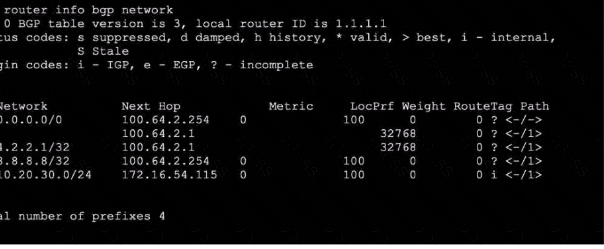
Which two statements are correct? (Choose two.)
What is the correct order of the IKEv2 request-and-response protocol?
Exhibit.
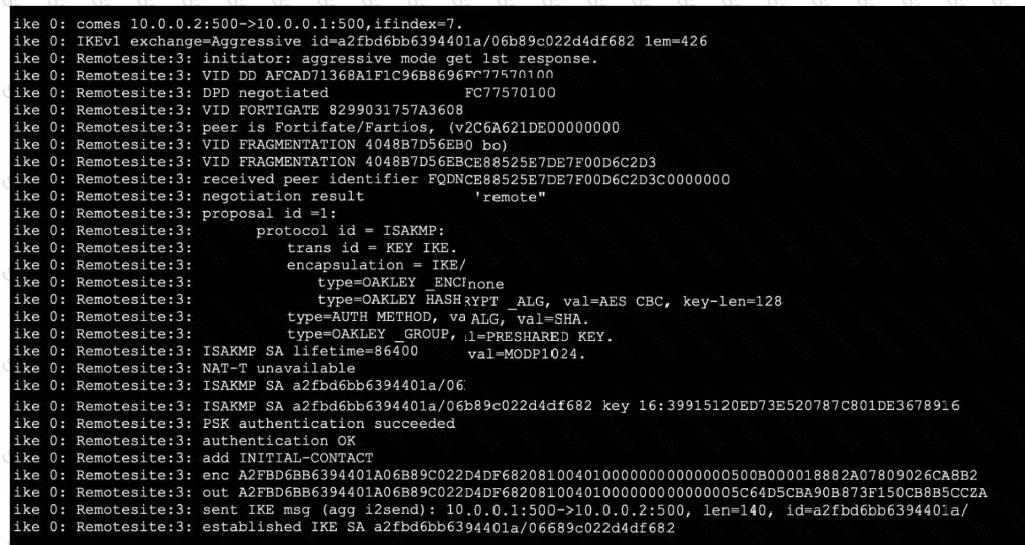
Refer to the exhibit, which contains partial output from an IKE real-time debug.
Which two statements about this debug output are correct? (Choose two.)
Which three common FortiGate-to-collector-agent connectivity issues can you identify using the FSSO real-time debug? (Choose three.)
Refer to the exhibit, which contains partial output from an IKE real-time debug.
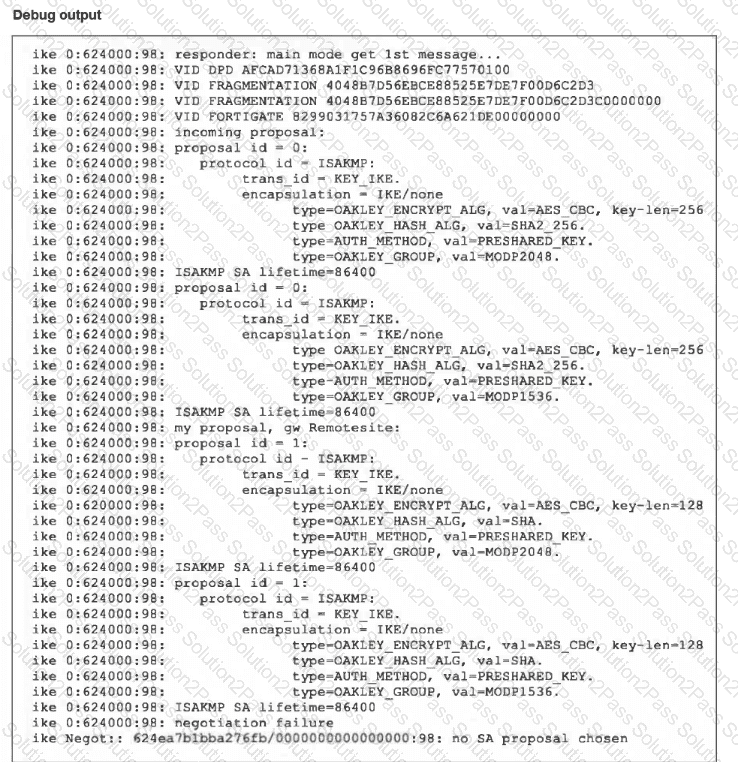
The administrator does not have access to the remote gateway.
Based on the debug output, which configuration change the administrator make to the local gateway to resolve the phase 1 negotiation error?
Exhibit.
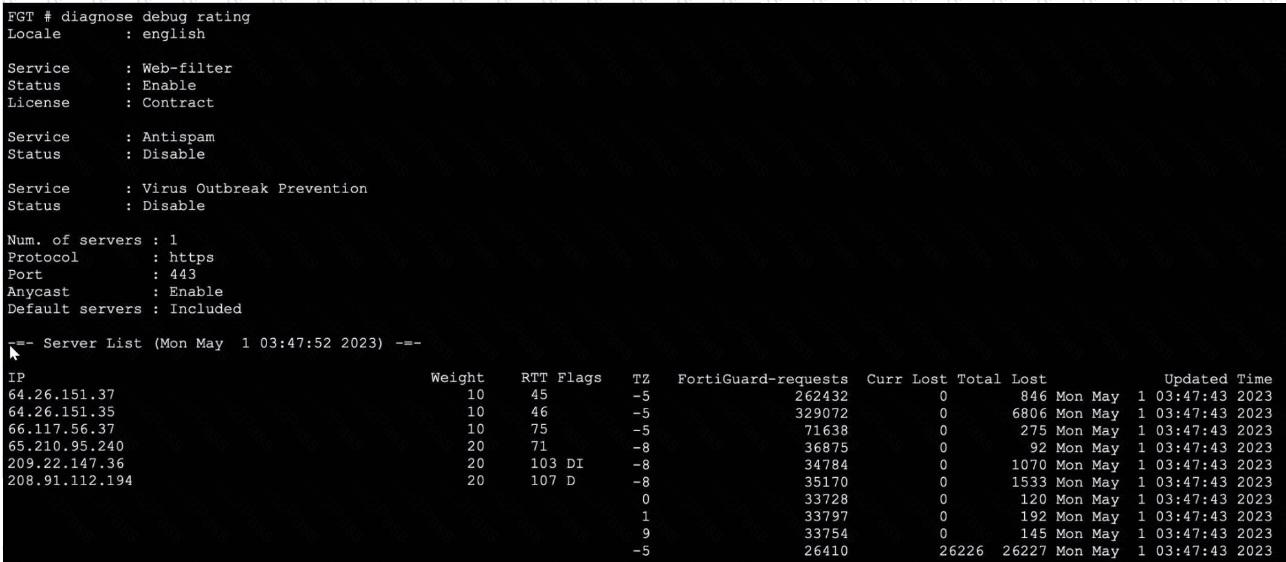
Refer to the exhibit, which shows the output of a diagnose command.
What can you conclude about the debug output in this scenario?
Refer to the exhibit, which shows the partial output of a real-time OSPF debug.
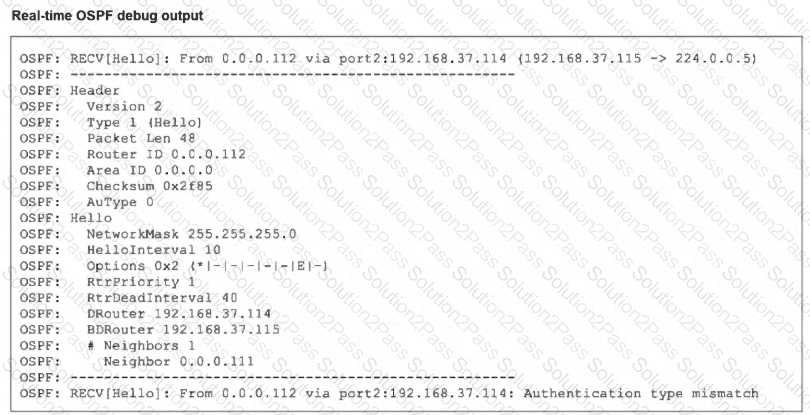
Why are the two FortiGate devices unable to form an adjacency?
In IKEv2, which exchange establishes the first CHILD_SA?
Refer to the exhibit, which shows a session entry.
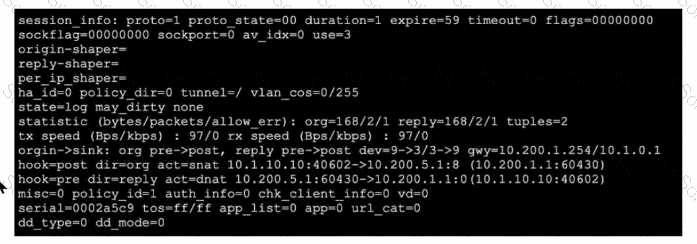
Which statement about this session is true?
Refer to the exhibit, which shows a partial output of a real-time LDAP debug.
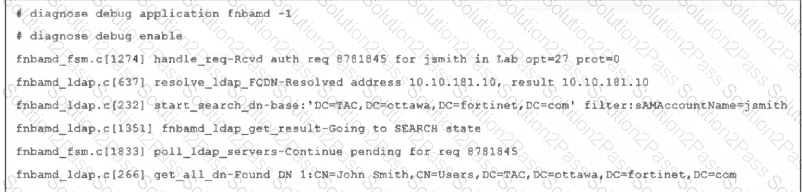
What two conclusions can you draw from the output? (Choose two.)
Refer to the exhibit.
The output of a BGO debug command is shown.

What is the most likely reason that the local FortiGate is not receiving any prefixes from its neighbors?
Which statement about IKEv2 is true?
Refer to the exhibit.
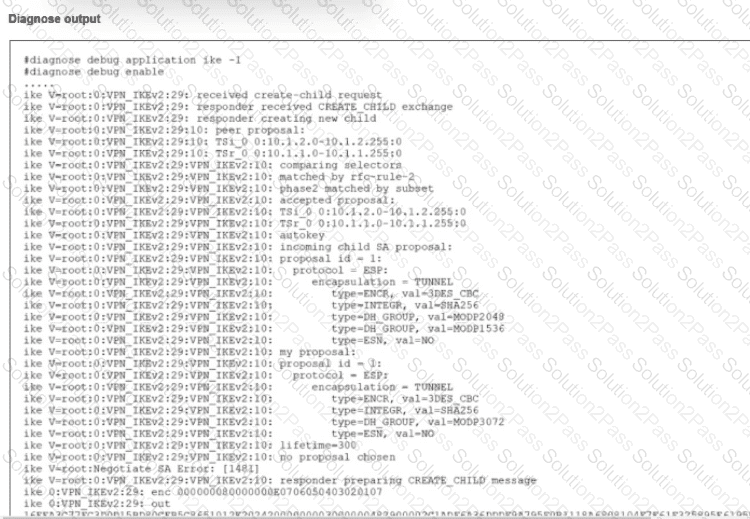
An IPsec VPN tunnel using IKEv2 was brought up successfully, but when the tunnel rekey takes place the tunnel goes down.
The debug command for IKE was enabled and, in the exhibit, you can review the partial output of the debug IKE while attempting to bring the tunnel up.
What is causing. The tunnel to be down?
Which two statements are true regarding heartbeat messages sent from an FSSO collector agent to FortiGate? (Choose two.)
Which Iwo troubleshooting steps should you perform lf you encounter issues with intermittent web filter behavior? (Choose two.)
