FCSS_SASE_AD-25 Fortinet FCSS - FortiSASE 25 Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet FCSS_SASE_AD-25 FCSS - FortiSASE 25 Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What are two advantages of using zero-trust tags? (Choose two.)
Refer to the exhibits.




A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub.
Based on the exhibits, what is the reason for the access failure?
Which FortiSASE feature ensures least-privileged user access to corporate applications that are protected by an on-premises FortiGate device?
Your organization is currently using FortiSASE for its cybersecurity. They have recently hired a contractor who will work from the HQ office and who needs temporary internet access in order to set up a web-based point of sale (POS) system.
What is the recommended way to provide internet access to the contractor?
Which FortiSASE component protects users from online threats by hosting their browsing sessions on a remote container within a secure environment?
What happens to the logs on FortiSASE that are older than the configured log retention period?
Which authentication method overrides any other previously configured user authentication on FortiSASE?
Refer to the exhibit.
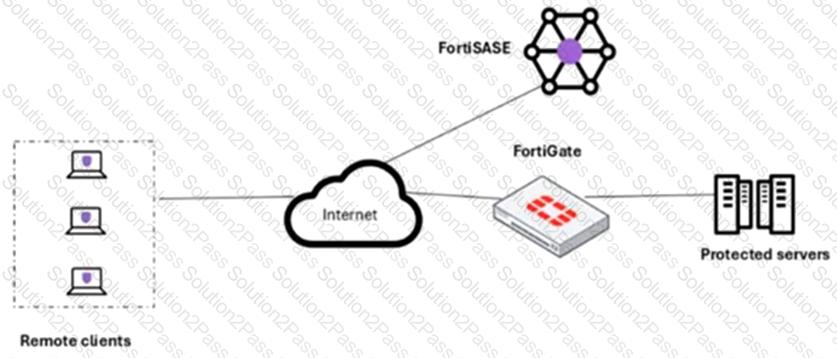
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which two setups will achieve these requirements? (Choose two.)
Which two purposes is the dedicated IP address used for in a FortiSASE deployment? (Choose two.)
A customer wants to ensure secure access for private applications for their users by replacing their VPN.
Which two SASE technologies can you use to accomplish this task? (Choose two.)
Which statement applies to a single sign-on (SSO) deployment on FortiSASE?
How can digital experience monitoring (DEM) on an endpoint assist in diagnosing connectivity and network issues?
A customer wants to upgrade their legacy on-premises proxy to a cloud-based proxy for a hybrid network.
Which two FortiSASE features would help the customer achieve this outcome? (Choose two.)
Which two advantages does FortiSASE bring to businesses with microbranch offices that have FortiAP deployed for unmanaged devices? (Choose two.)
Refer to the exhibit.

Based on the configuration shown, in which two ways will FortiSASE process sessions that require FortiSandbox inspection? (Choose two.)
