FCSS_SOC_AN-7.4 Fortinet FCSS - Security Operations 7.4 Analyst Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet FCSS_SOC_AN-7.4 FCSS - Security Operations 7.4 Analyst certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit,
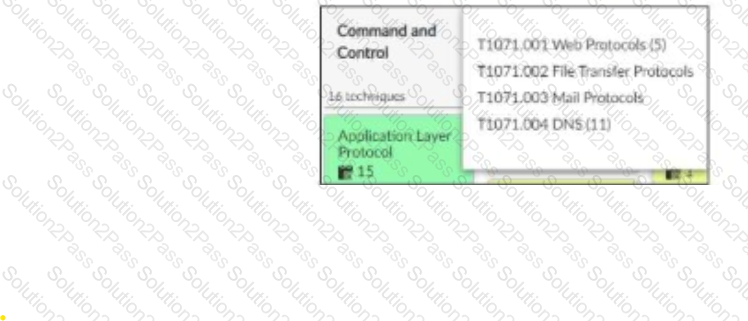
which shows the partial output of the MITRE ATT&CK Enterprise matrix on FortiAnalyzer.
Which two statements are true? (Choose two.)
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
Which two ways can you create an incident on FortiAnalyzer? (Choose two.)
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables? (Choose two.)
Refer to the exhibits.
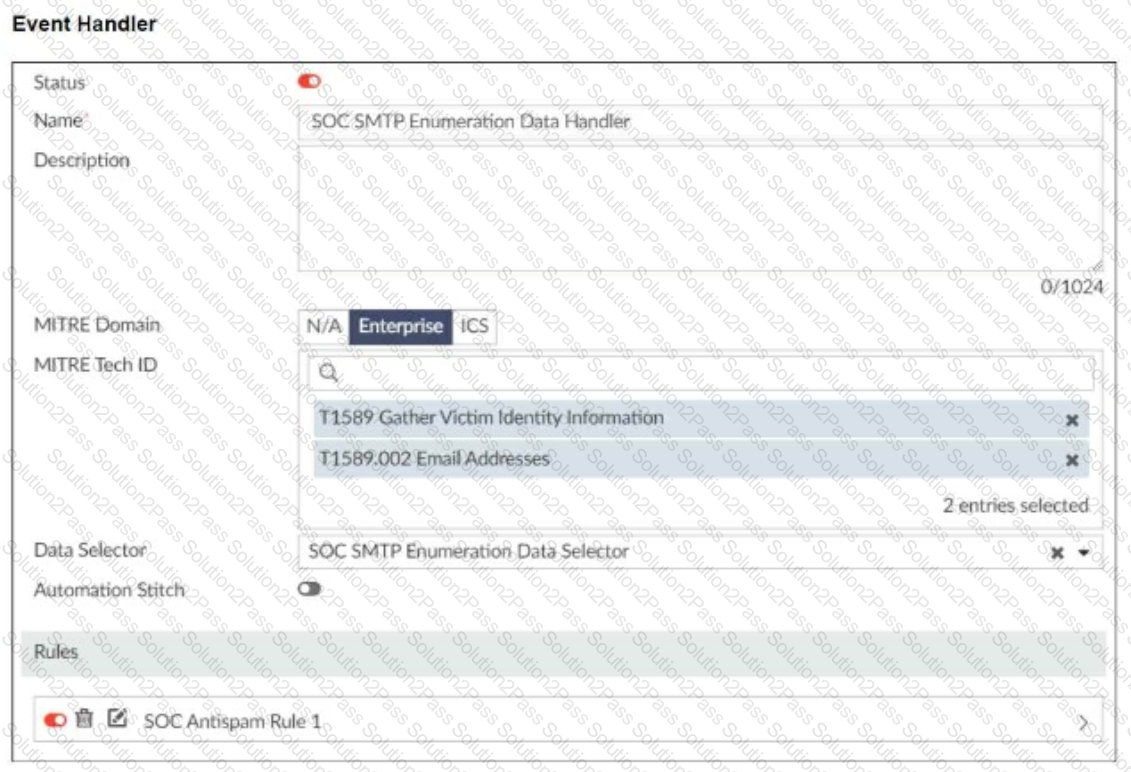
You configured a custom event handler and an associated rule to generate events whenever FortiMail detects spam emails. However, you notice that the event handler is generating events for both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
Refer to the exhibits.
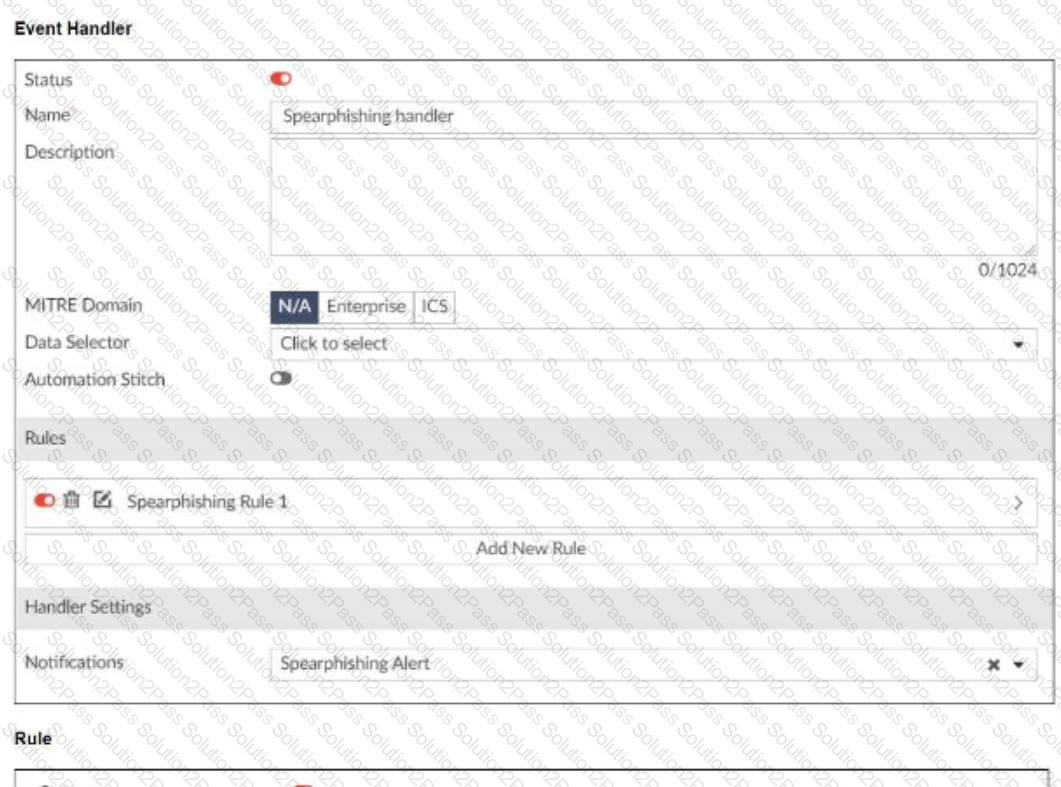
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an event?
Refer to the exhibit.
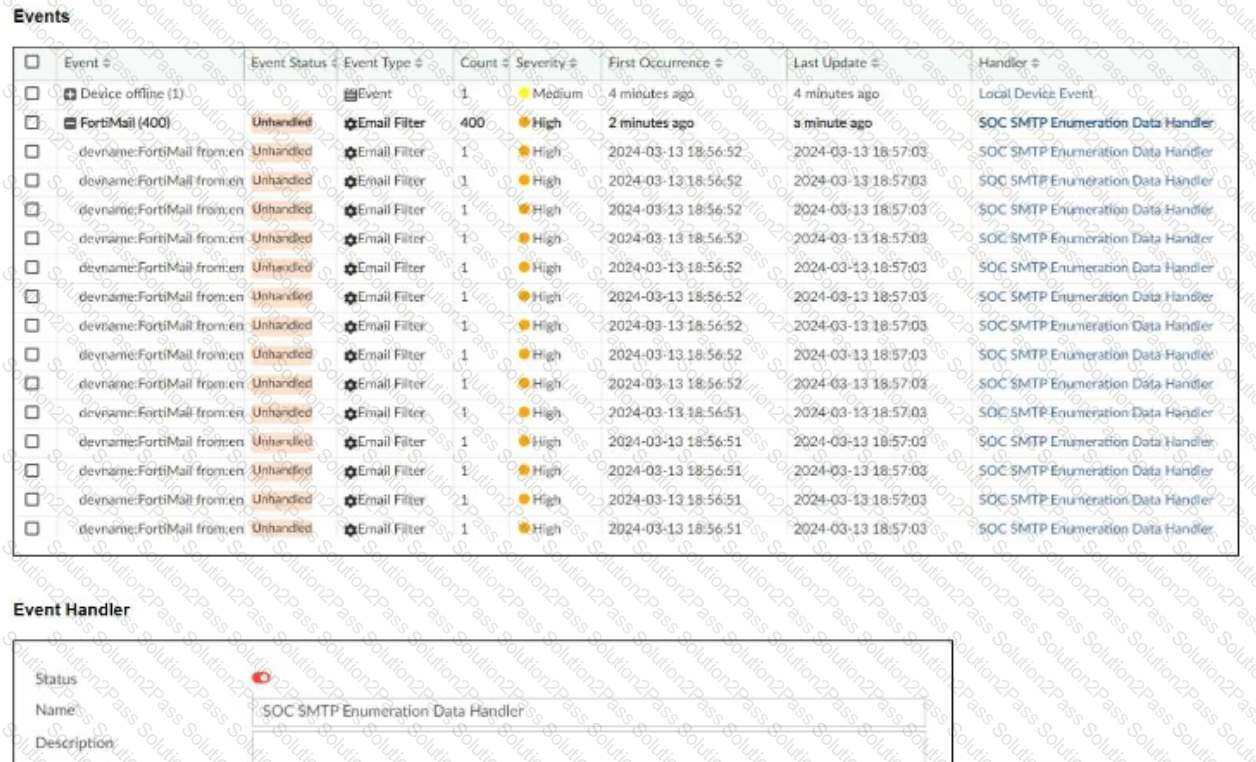
You notice that the custom event handler you configured to detect SMTP reconnaissance activities is creating a large number of events. This is overwhelming your notification system.
How can you fix this?
Which FortiAnalyzer connector can you use to run automation stitches9
Refer to Exhibit:
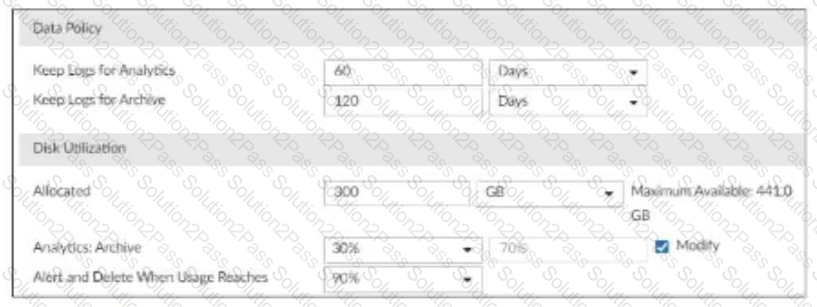
You are tasked with reviewing a new FortiAnalyzer deployment in a network with multiple registered logging devices. There is only one FortiAnalyzer in the topology.
Which potential problem do you observe?
