NSE6_FAC-6.4 Fortinet NSE 6 - FortiAuthenticator 6.4 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE6_FAC-6.4 Fortinet NSE 6 - FortiAuthenticator 6.4 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which FSSO discovery method transparently detects logged off users without having to rely on external features such as WMI polling?
Which EAP method is known as the outer authentication method?
You are an administrator for a large enterprise and you want to delegate the creation and management of guest users to a group of sponsors.
How would you associate the guest accounts with individual sponsors?
An administrator wants to keep local CA cryptographic keys stored in a central location.
Which FortiAuthenticator feature would provide this functionality?
When generating a TOTP for two-factor authentication, what two pieces of information are used by the algorithm to generate the TOTP?
Which two are supported captive or guest portal authentication methods? (Choose two)
Which statement about the assignment of permissions for sponsor and administrator accounts is true?
You are the administrator of a large network that includes a large local user datadabase on the current Fortiauthenticatior. You want to import all the local users into a new Fortiauthenticator device.
Which method should you use to migrate the local users?
Which two SAML roles can Fortiauthenticator be configured as? (Choose two)
You want to monitor FortiAuthenticator system information and receive FortiAuthenticator traps through SNMP.
Which two configurations must be performed after enabling SNMP access on the FortiAuthenticator interface? (Choose two)
Which of the following is an OATH-based standard to generate event-based, one-time password tokens?
A digital certificate, also known as an X.509 certificate, contains which two pieces of information? (Choose two.)
You have implemented two-factor authentication to enhance security to sensitive enterprise systems.
How could you bypass the need for two-factor authentication for users accessing form specific secured networks?
Examine the screenshot shown in the exhibit.
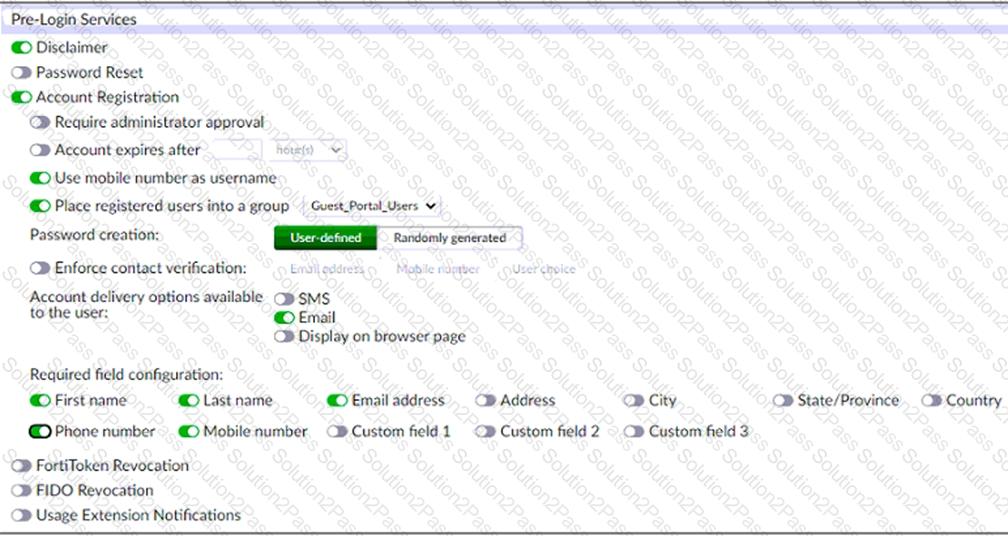
Which two statements regarding the configuration are true? (Choose two.)
