NSE6_FML-6.4 Fortinet NSE 6 - FortiMail 6.4 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE6_FML-6.4 Fortinet NSE 6 - FortiMail 6.4 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Examine the FortiMail recipient-based policy shown in the exhibit; then answer the question below.
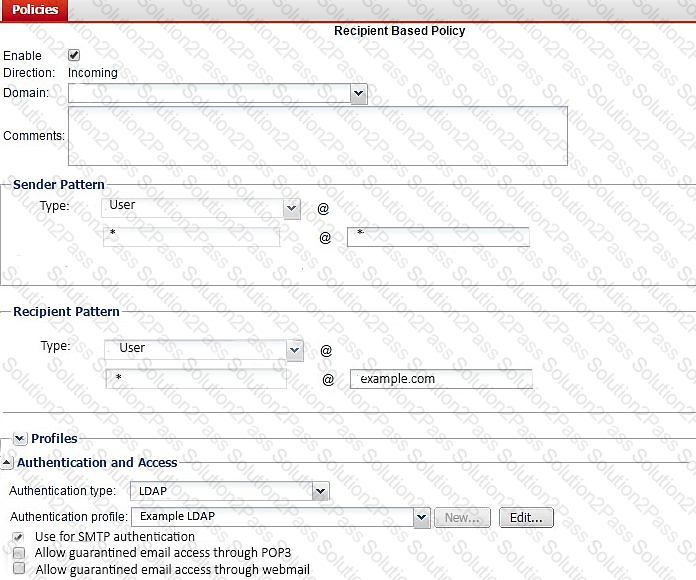
After creating the policy, an administrator discovered that clients are able to send unauthenticated email using SMTP. What must be done to ensure clients cannot send unauthenticated email?
What are the configuration steps to enable DKIM signing for outbound messages on FortiMail? (Choose three.)
Examine the FortiMail antivirus action profile shown in the exhibit; then answer the question below.
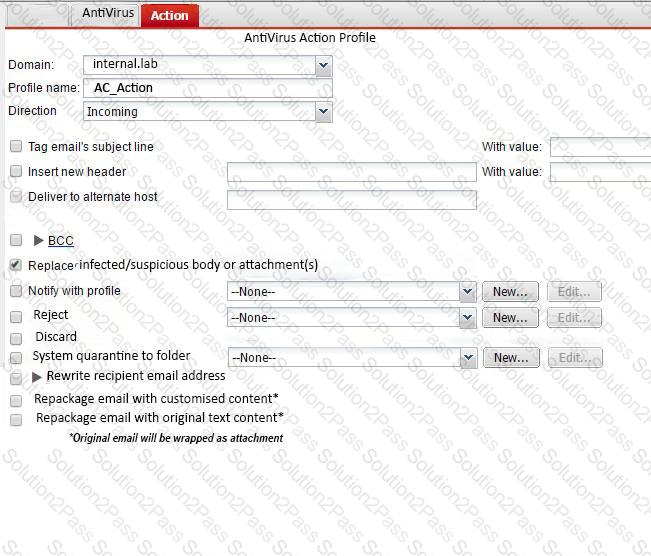
What is the expected outcome if FortiMail applies this action profile to an email? (Choose two.)
Examine the access receive rule shown in the exhibit; then answer the question below.
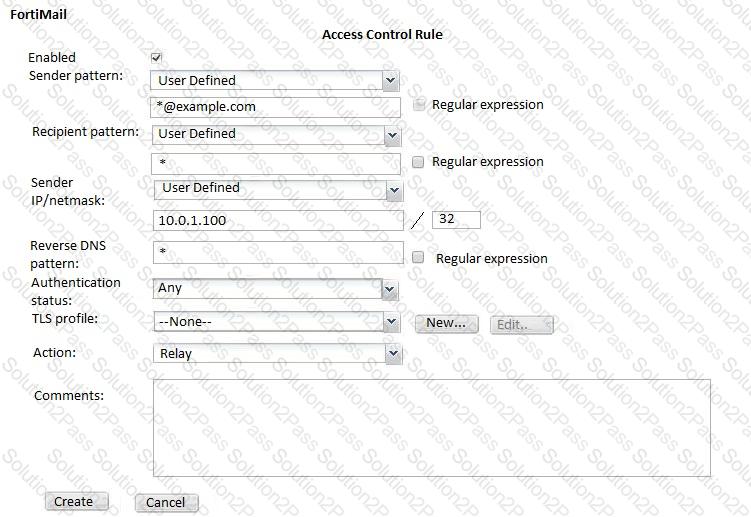
Which of the following statements are true? (Choose two.)
Examine the FortiMail archiving policies shown in the exhibit; then answer the question below.
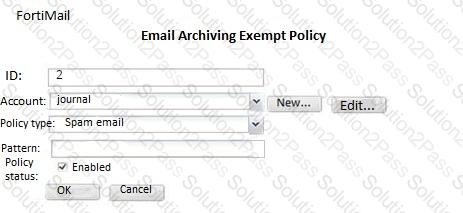
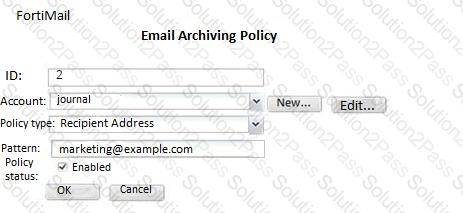
Which of the following statements is true regarding this configuration? (Choose two.)
Examine the FortMail mail server settings shown in the exhibit; then answer the question below.
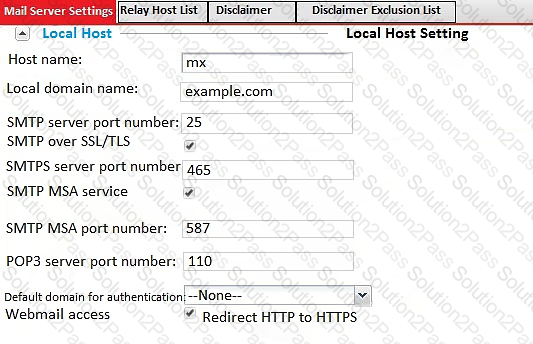
Which of the following statements are true? (Choose two.)
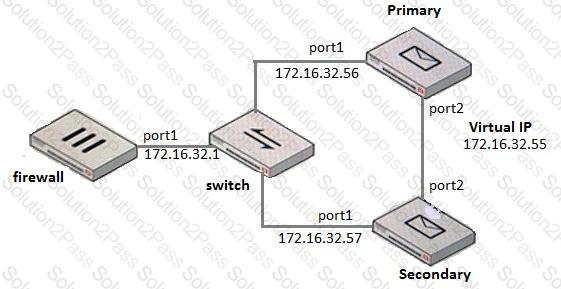
What IP address should the DNS MX record for this deployment resolve to?
Which of the following antispam techniques queries FortiGuard for rating information? (Choose two.)
Refer to the exhibit.
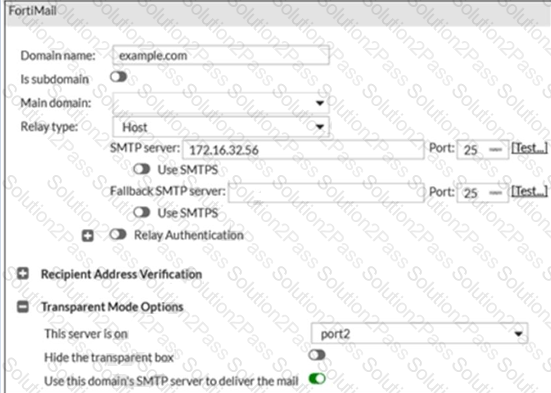
For the transparent mode FortiMail shown in the exhibit, which two sessions are considered incoming sessions? (Choose two.)
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9.
Which two scenarios will generate this policy ID? (Choose two.)
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks.
What option can the administrator configure to prevent these types of attacks?
What three configuration steps are required to enable DKIM signing for outbound messages on FortiMail? (Choose three.)
Refer to the exhibit.
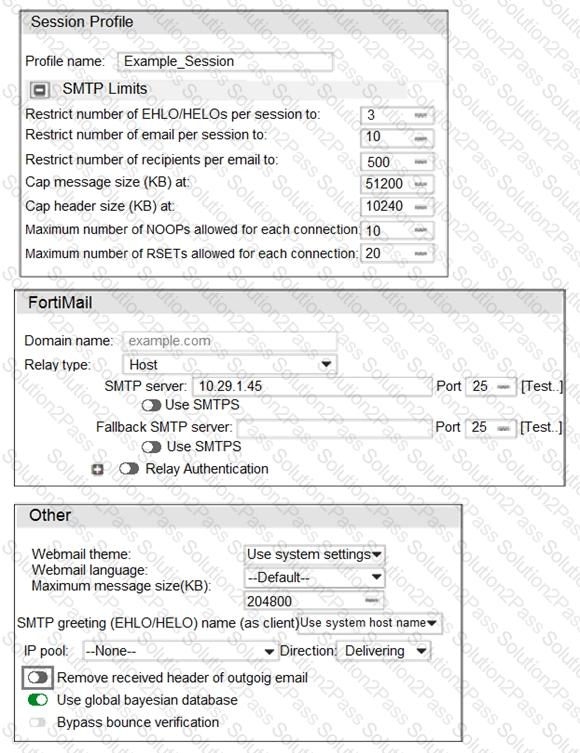
Which message size limit will FortiMail apply to the outbound email?
Refer to the exhibit.
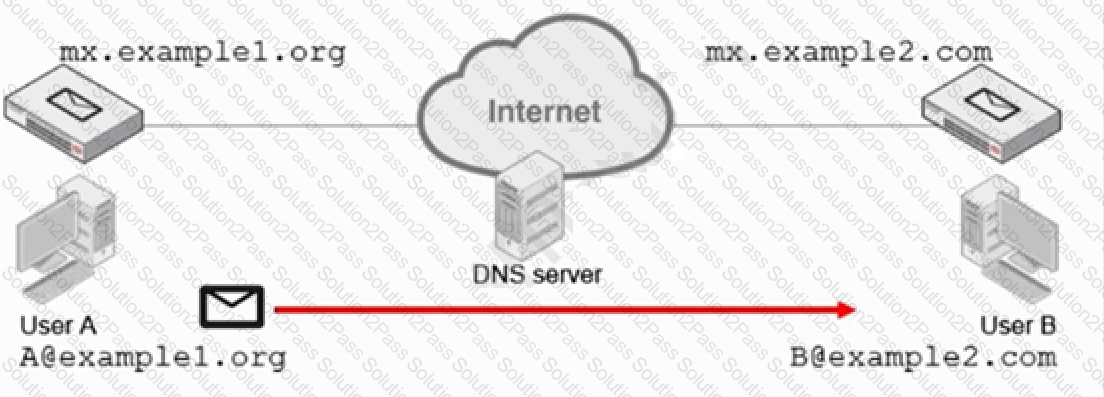
Which two statements about email messages sent from User A to User B are correct? (Choose two.)
Refer to the exhibit.
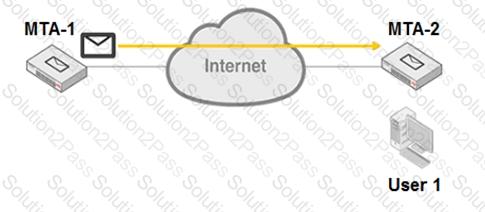
MTA-1 is delivering an email intended for User 1 to MTA-2.
Which two statements about protocol usage between the devices are true? (Choose two.)
Refer to the exhibit.
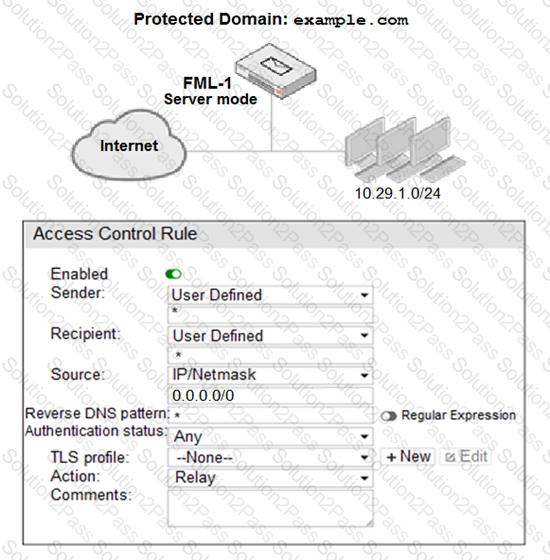
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain. Which two settings should be used to configure the access receive rule? (Choose two.)
