NSE6_FNC-7.2 Fortinet NSE 6 - FortiNAC 7.2 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE6_FNC-7.2 Fortinet NSE 6 - FortiNAC 7.2 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which command line shell and scripting language does FortiNAC use for WinRM?
Refer to the exhibit, and then answer the question below.
Which host is rogue?
Which three capabilities does FortiNAC Control Manager provide? (Choose three.)
Where should you configure MAC notification traps on a supported switch?
Refer to the exhibit.
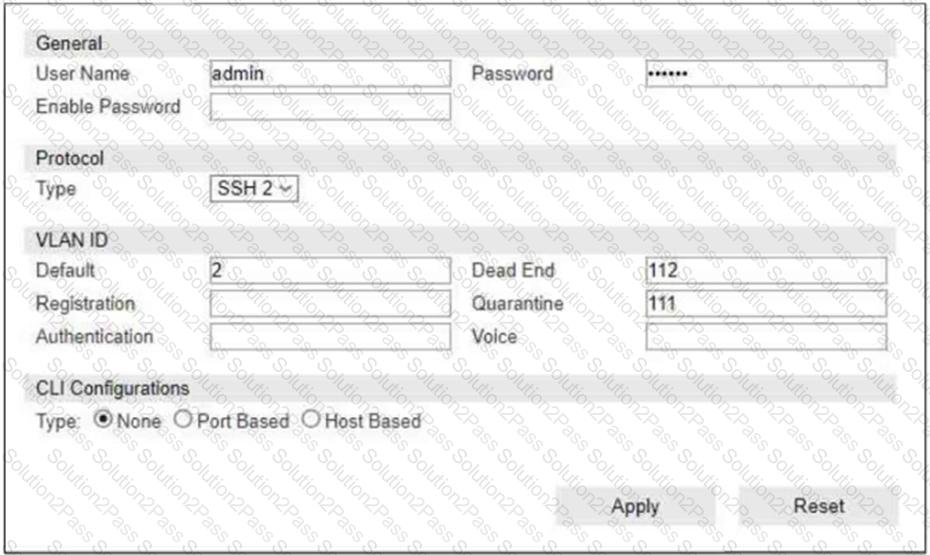
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
Which two things must be done to allow FortiNAC to process incoming syslog messages from an unknown vendor? (Choose two.)
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
When FortiNAC passes a firewall tag to FortiGate, what determines the value that is passed?
What agent is required in order to detect an added USB drive?
Refer to the exhibit.
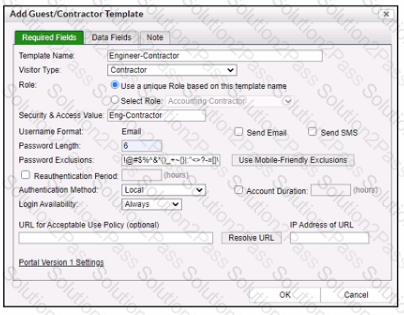
When a contractor account is created using this template, what value will be set in the accounts Rote field?
What capability do logical networks provide?
Which two device classification options can register a device automatically and transparently to the end user? (Choose two.)
Which three communication methods are used by FortiNAC to gather information from and control, infrastructure devices? (Choose three.)
Which three of the following are components of a security rule? (Choose three.)
In which view would you find who made modifications to a Group?
What method of communication does FortiNAC use to control VPN host access on FortiGate?
Which three are components of a security rule? (Choose three.)
