NSE6_FSR-7.3 Fortinet NSE 6 - FortiSOAR 7.3 Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE6_FSR-7.3 Fortinet NSE 6 - FortiSOAR 7.3 Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An administrator wants to collect and review all FortiSOAR log tiles to troubleshoot an issue. Which two methods can they use to accomplish this? (Choose two.)
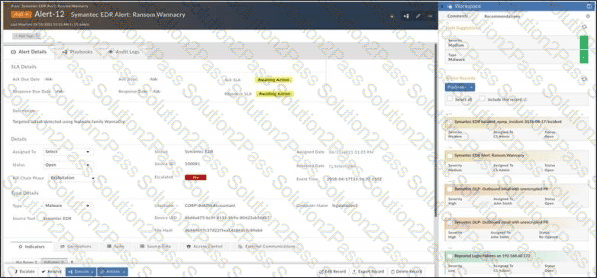
View the exhibit. The dataset on FortiSOAR has been trained to predict which record field?
What are two system-level logs that can be purged using application configuration? (Choose two.)
Select two statements that are true about FortiSOAR themes.
(Choose two.)
Refer to the exhibit.
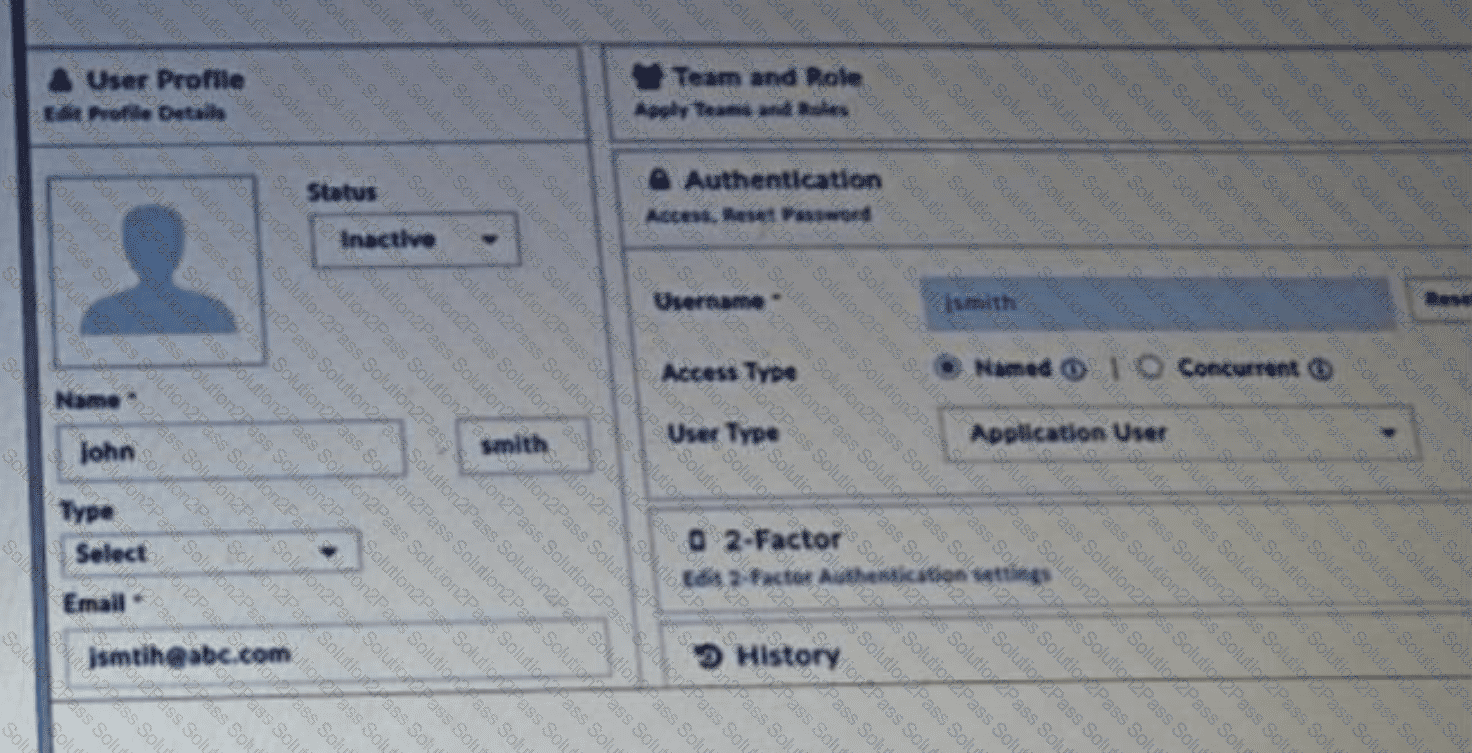
Why is this user's account inactive? (Choose one answer)
Which two relationship types are configurable on FortiSOAR?
(Choose two.)
What are two features of the FortiSOAR perpetual trial license? (Choose two.).
Which two statements about FortiSOAR virtual instance deployment requirements are true? (Choose two.)
Refer to the exhibit.
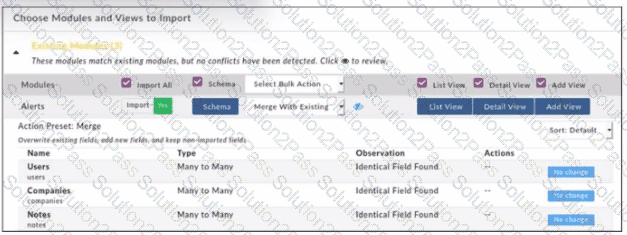
When importing modules to FortiSOAR using the configuration wizard, what actions are applied to fields it you select Merge with Existing as the Bulk action?
An administrator is issuing the following command on a node trying to join a FortiSOAR duster as a standby: csadm ha join-cluster --status active —role secondary --primary-node 10.0.1.160
The node fails to join the cluster. What is the issue?
A security analyst has reported unauthorized access to System Configuration. You must review the user's current level of access, and then restrict their access according to your organization's requirements. As part of your auditing process, which two actions should you perform? (Choose two.)
Refer to the exhibit.
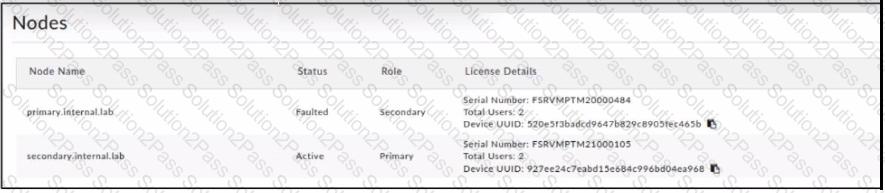
The former primary node was relegated to the secondary rote but is stuck in the Faulted state.
Which two steps must you take to restore operation in the high availability (HA) cluster? (Choose two.)
Which product is essential to level 3 of the SOC automation model?
