NSE7_LED-7.0 Fortinet NSE 7 - LAN Edge 7.0 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE7_LED-7.0 Fortinet NSE 7 - LAN Edge 7.0 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which CLI command should an administrator use to view the certificate verification process in real time?
Which two statements about the use of digital certificates are true? (Choose two.)
You are configuring a FortiGate wireless network to support automated wireless client quarantine using IOC Which two configurations must you put in place for a wireless client to be quarantined successfully? (Choose two)
Exhibit.
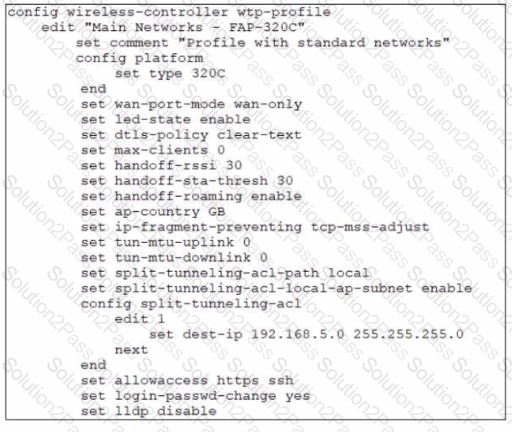
Exhibit.

Refer to the exhibits
In the wireless configuration shown in the exhibits, an AP is deployed in a remote site and has a wireless network (VAP) called Corporate deployed to it
The network is a tunneled network however clients connecting to a wireless network require access to a local printer Clients are trying to print to a printer on the remote site but are unable to do so
Which configuration change is required to allow clients connected to the Corporate SSID to print locally?
Which FortiSwitch VLANs are automatically created on FortGate when the first FortiSwitch device is discovered1?
Refer to the exhibit.
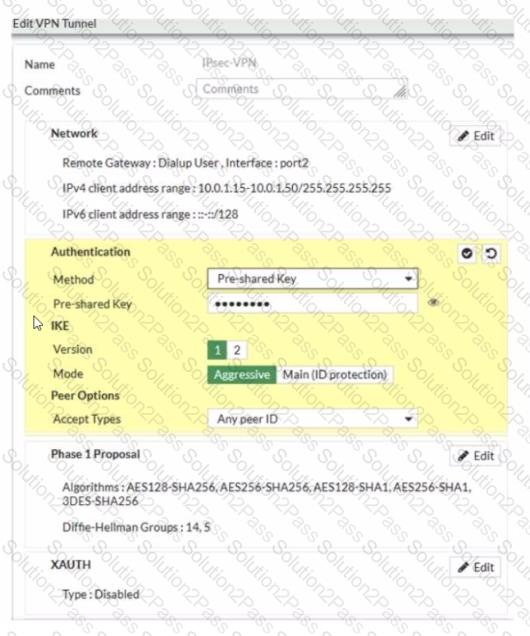
Examine the IPsec VPN phase 1 configuration shown in the exhibit
An administrator wants to use certificate-based authentication for an IPsec VPN user
Which three configuration changes must you make on FortiGate to perform certificate-based authentication for the IPsec VPN user? (Choose three)
Refer to the exhibit.
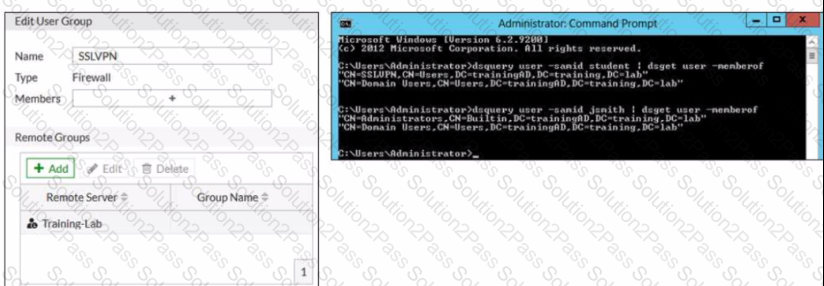
Examine the FortiGate user group configuration and the Windows AD LDAP group membership information shown in the exhibit
FortiGate is configured to authenticate SSL VPN users against Windows AD using LDAP The administrator configured the SSL VPN user group for SSL VPN users However the administrator noticed that both the student and j smith users can connect to SSL VPN
Which change can the administrator make on FortiGate to restrict the SSL VPN service to the student user only?
Refer to the exhibits.

Examine the LDAP server configuration and output shown in the exhibits.
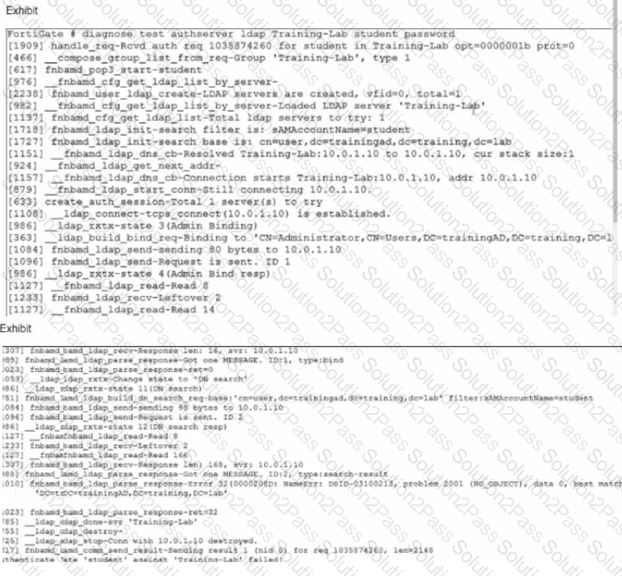
Note that the Distinguished Name and Username settings on the LDAP server configuration have been expanded to display their full contents.
An LDAP user named student cannot authenticate. While testing the student account, the administrator gets the CLI output shown in the exhibit.
According to the output, which FortiGate LDAP server settings must the administrator check?
Refer to the exhibits.
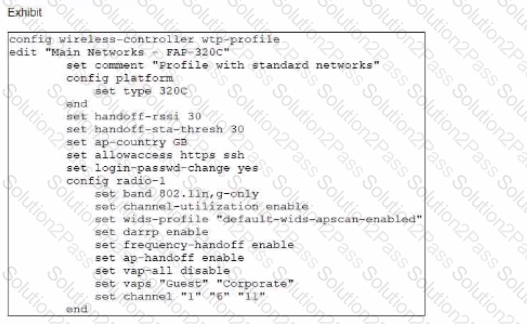
In the WTP profile configuration shown in the exhibit, the AP profile is assigned to two FAP-320 APs that are installed in an open plan office.
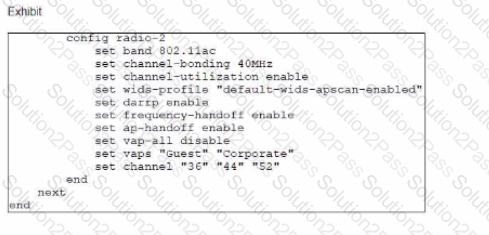
The first AP has 32 clients associated with the 5 GHz radios and 22 clients associated with the 2.4 GHz radio. The second AP has 12 clients associated with the 5 GHz radios and 20 clients associated with the 2.4 GHz radio.
A dual-band-capable client enters the office near the first AP and the first AP measures the new client at -33 dBm signal strength. The second AP measures the new client at 2 -43 dBm signal strength.
If the new client attempts to connect to the corporate wireless network, with which AP radio will the client be associated?
You are setting up an SSID (VAP) to perform RADlUS-authenticated dynamic VLAN allocation
Which three RADIUS attributes must be supplied by the RADIUS server to enable successful VLAN allocation'' (Choose three.)
Refer to the exhibit.
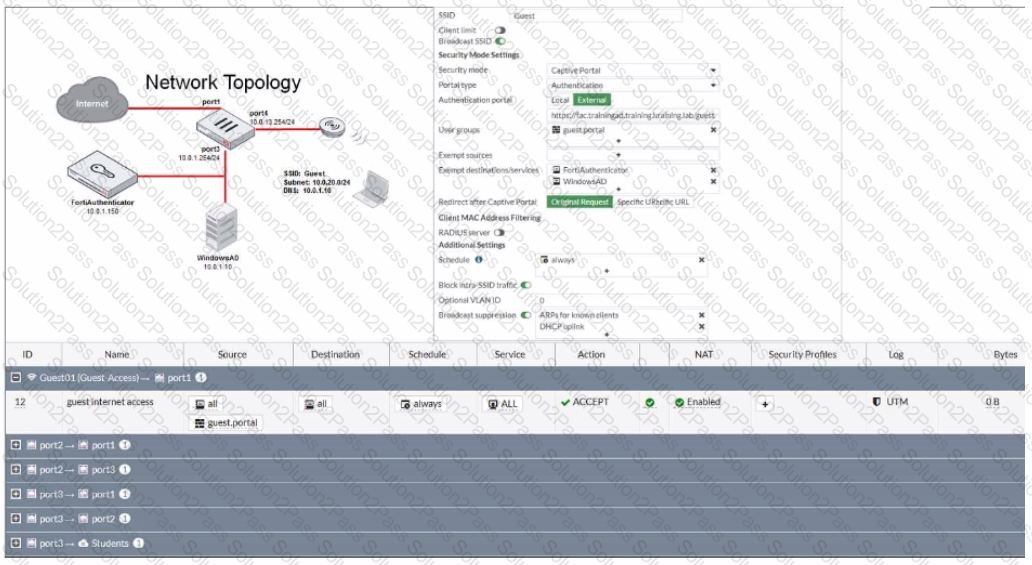
The exhibit shows a network topology and SSID settings. FortiGate is configured to use an external captive portal.
However, wireless users are not able to see the captive portal login page.
Which configuration change should the administrator make to fix the problem?
Which EAP method requires the use of a digital certificate on both the server end and the client end?
Which statement correctly describes the guest portal behavior on FortiAuthenticator?
To troubleshoot configuration push issues on a managed FortiSwitch, which FortiGate process should an administrator enable debug for?
Exhibit.
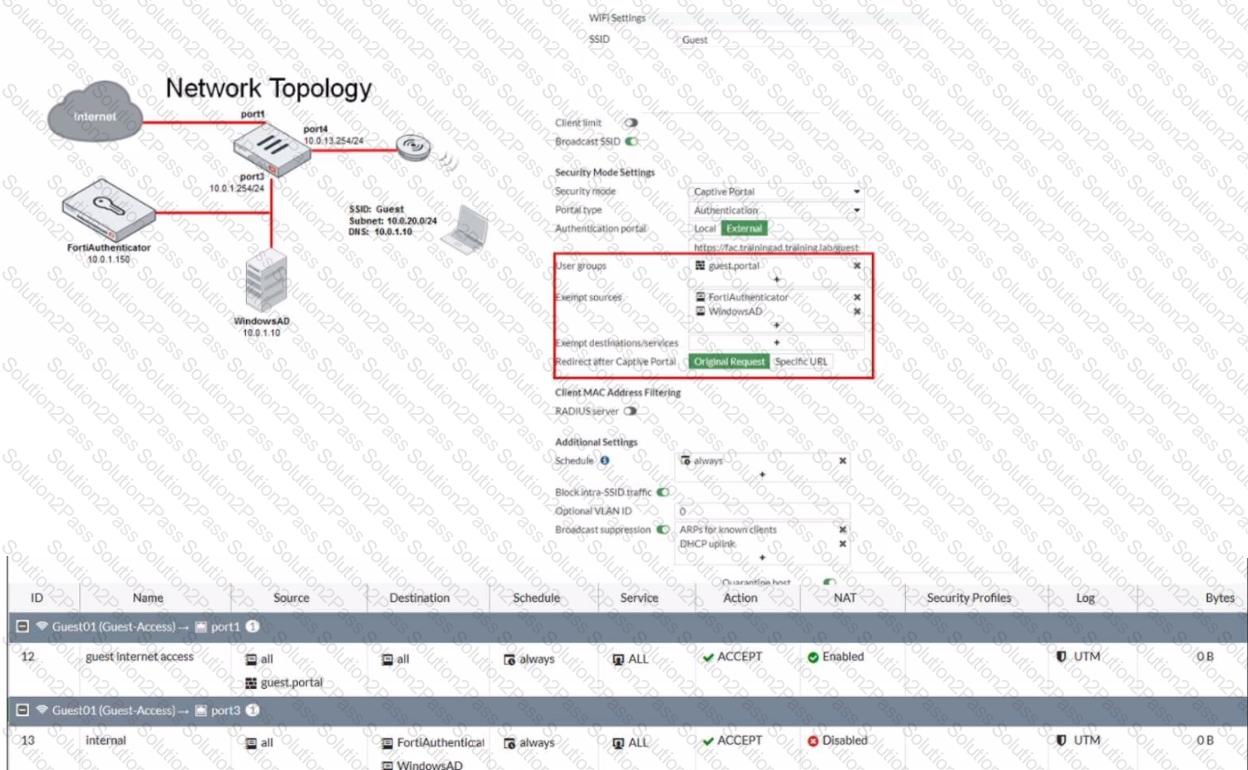
Refer to the exhibit showing a network topology and SSID settings.
FortiGate is configured to use an external captive portal However wireless users are not able to see the captive portal login page
Which configuration change should the administrator make to fix the problem?
Refer to the exhibit.
Examine the FortiGate RSSO configuration shown in the exhibit.
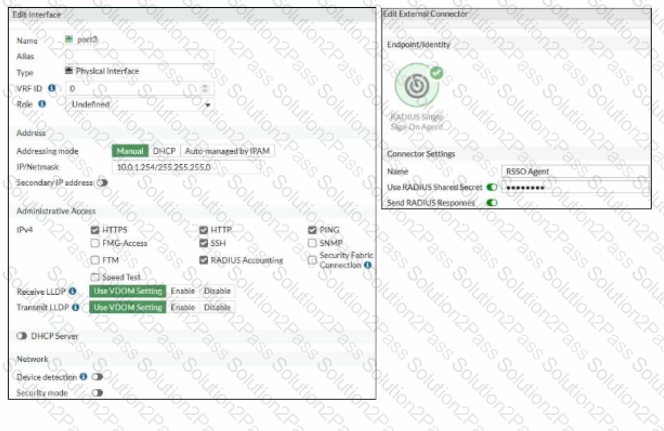
FortiGate is configured to receive RADIUS accounting messages on port3 to authenticate RSSO users. The incoming RADIUS accounting messages contain the username and group membership information in the User-Name and Class RADIUS attributes, respectively.
Which three settings must you configure onFortiGate to successfully authenticate RSSO users and matchthem to the existing RSSO user groups? (Choose three)
When you configure a FortiAP wireless interface for auto TX power control which statement describes how it configures its transmission power"?
Refer to the exhibit.
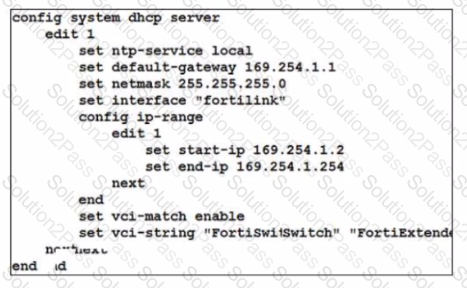
By default FortiOS creates the following DHCP server scope for the FortiLink interface as shown in the exhibit
What is the objective of the vci-string setting?
