NSE7_SOC_AR-7.6 Fortinet NSE 7 - Security Operations 7.6 Architect Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE7_SOC_AR-7.6 Fortinet NSE 7 - Security Operations 7.6 Architect certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables? (Choose two.)
Which role does a threat hunter play within a SOC?
Refer to Exhibit:
A SOC analyst is designing a playbook to filter for a high severity event and attach the event information to an incident.
Which local connector action must the analyst use in this scenario?
Refer to the exhibit.
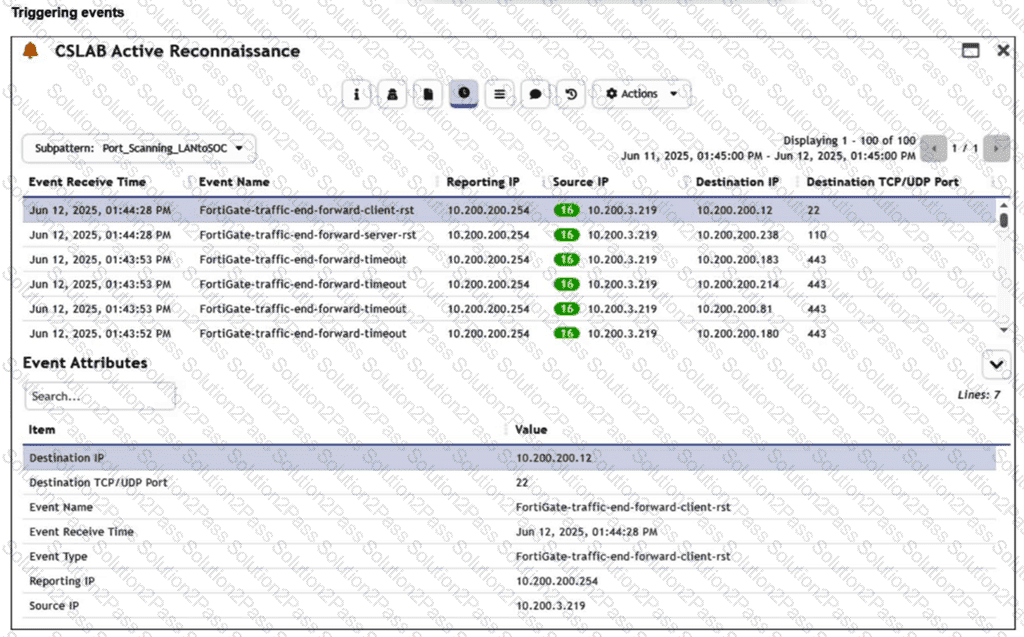
You are reviewing the Triggering Events page for a FortiSIEM incident. You want to remove the Reporting IP column because you have only one firewall in the topology. How do you accomplish this? (Choose one answer)
Which of the following are critical when analyzing and managing events and incidents in a SOC? (Choose two answers)
Which two best practices should be followed when exporting playbooks in FortiAnalyzer? (Choose two answers)
Which statement describes automation stitch integration between FortiGate and FortiAnalyzer?
Which two ways can you create an incident on FortiAnalyzer? (Choose two.)
Review the incident report:
Packet captures show a host maintaining periodic TLS sessions that imitate normal HTTPS traffic but run on TCP 8443 to a single external host. An analyst flags the traffic as potential command-and-control. During the same period, the host issues frequent DNS queries with oversized TXT payloads to an attacker-controlled domain, transferring staged files.
Which two MITRE ATT&CK techniques best describe this activity? (Choose two answers)
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three.)
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
Which two types of variables can you use in playbook tasks? (Choose two.)
Refer to Exhibit:
You are tasked with reviewing a new FortiAnalyzer deployment in a network with multiple registered logging devices. There is only one FortiAnalyzer in the topology.
Which potential problem do you observe?
Refer to the exhibit.
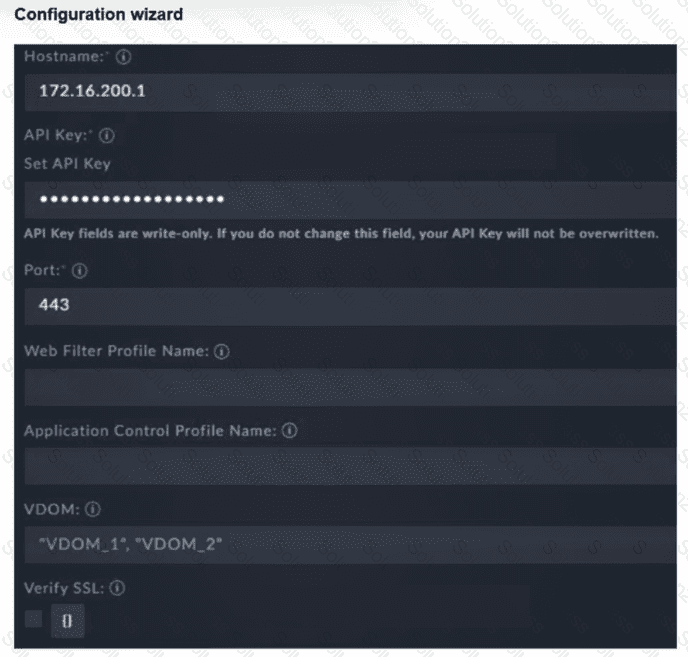
You must configure the FortiGate connector to allow FortiSOAR to perform actions on a firewall. However, the connection fails. Which two configurations are required? (Choose two answers)
Which statement best describes the MITRE ATT&CK framework?
Your company is doing a security audit To pass the audit, you must take an inventory of all software and applications running on all Windows devices
Which FortiAnalyzer connector must you use?
Refer to the exhibits.
You configured a custom event handler and an associated rule to generate events whenever FortiMail detects spam emails. However, you notice that the event handler is generating events for both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
