GCFW GIAC Certified Firewall Analyst Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GCFW GIAC Certified Firewall Analyst certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You are implementing passive OS fingerprinting in a network. Which of the following aspects are required to be configured there?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following terms is used to represent IPv6 addresses?
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008- based network. You have created a test domain for testing IPv6 addressing. Which of the following types of addresses are supported by IPv6?
Each correct answer represents a complete solution. Choose all that apply.
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote operating system (OS fingerprinting), or incorporated into a device fingerprint. Which of the following Nmap switches can be used to perform TCP/IP stack fingerprinting?
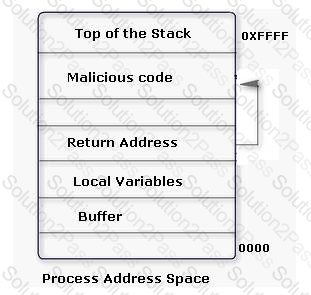
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
Which of the following tools can be used as a countermeasure to such an attack?
Which of the following ports cannot be used to access the router from a computer?
Which of the following wireless security features provides the best wireless security mechanism?
Which of the following well-known ports is used by BOOTP?
John, a malicious hacker, forces a router to stop forwarding packets by flooding it with many open connections simultaneously so that all hosts behind it are effectively disabled. Which of the following attacks is John performing?
Which of the following statements are true about an IDP rule base notification?
You work as a Network Administrator for BlueTech Inc. You want to configure Snort as an IDS for your company's wireless network, but you are concerned that Snort does not support all types of traffic. What traffic does Snort support?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to send malicious data packets in such a manner that one packet fragment overlaps data from a previous fragment so that he can perform IDS evasion on the We-are-secure server and execute malicious data. Which of the following tools can he use to accomplish the task?
Which of the following parts of IP header is used to specify the correct place of the fragment in the original un-fragmented datagram?
Which of the following firewalls operates at three layers- Layer3, Layer4, and Layer5?
Sam works as a Network Administrator for Gentech Inc. He has been assigned a project to develop the rules that define the IDP policy in the rulebase. Which of the following will he define as the components of the IDP policy rule?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements about the traceroute utility are true?
Each correct answer represents a complete solution. Choose all that apply.
You want to create a binary log file using tcpdump. Which of the following commands will you use?
You work as a Network Administrator for Tech Perfect Inc. The office network is configured as an IPv6 network. You have to configure a computer with the IPv6 address, which is equivalent to an IPv4 publicly routable address. Which of the following types of addresses will you choose?
Which of the following tools is used to analyze the files produced by several popular packetcapture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
Which of the following algorithms is used as a default algorithm for ESP extension header in IPv6?
