GCIA GIAC GCIA – GIAC Certified Intrusion Analyst Practice Test Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GCIA GCIA – GIAC Certified Intrusion Analyst Practice Test certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following log files are used to collect evidences before taking the bit-stream image of the BlackBerry?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 Active Directory-based single forest multiple domain IPv4 network. All the DNS servers on the network run Windows Server 2008. The users in the network use NetBIOS name to connect network application on the network. You have migrated the network to IPv6-enabled network. Now you want to enable DNS Server to perform lookups in GlobalNames Zone. Which of the following commands will you use to accomplish the task?
Which of the following statements are true about snort?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools is used to analyze the files produced by several popular packetcapture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
Which of the following techniques is used to identify attacks originating from a botnet?
Which of the following UDP ports are used by the Simple Network Management Protocol (SNMP)?
Each correct answer represents a complete solution. Choose two.
With reference to the given case study, one of the security goals requires to configure a secure connection between the Boston distribution center and the headquarters. You want to implement IP filter to fulfill the security requirements. How should you implement IP filters at the headquarters?
(Click the Exhibit button on the toolbar to see the case study.)
Which of the following terms is used to represent IPv6 addresses?
Which of the following tools is used to detect wireless LANs using the 802.11b, 802.11a, and 802.11g WLAN standards on the Windows platform?
Andrew, a bachelor student of Faulkner University, creates a gmail account. He uses 'Faulkner' as the password for the gmail account. After a few days, he starts receiving a lot of e-mails stating that his gmail account has been hacked. He also finds that some of his important mails have been deleted by someone. Which of the following methods has the attacker used to crack Andrew's password?
Each correct answer represents a complete solution. Choose all that apply.
John, a novice web user, makes a new E-mail account and keeps his password as "apple", his favorite fruit. John's password is vulnerable to which of the following password cracking attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following attacks involves multiple compromised systems to attack a single target?
Sasha wants to add an entry to your DNS database for your mail server. Which of the following types of resource records will she use to accomplish this?
Which of the following components are usually found in an Intrusion detection system (IDS)?
Each correct answer represents a complete solution. Choose two.
Which of the following is the default port for Simple Network Management Protocol (SNMP)?
Adam works as a Security administrator for Umbrella Inc. He runs the following traceroute and notice that hops 19 and 20 both show the same IP address.
1 172.16.1.254 (172.16.1.254) 0.724 ms 3.285 ms 0.613 ms 2 ip68-98-176-
1.nv.nv.cox.net (68.98.176.1) 12.169 ms 14.958 ms 13.416 ms 3 ip68-98-176-
1.nv.nv.cox.net (68.98.176.1) 13.948 ms ip68-100-0-1.nv.nv. cox.net (68.100.0.1)
16.743 ms 16.207 ms 4 ip68-100-0-137.nv.nv.cox.net (68.100.0.137) 17.324 ms 13.933
ms 20.938 ms 5 68.1.1.4 (68.1.1.4) 12.439 ms 220.166 ms 204.170 ms
6 so-6-0-0.gar2.wdc1.Level3.net (67.29.170.1) 16.177 ms 25.943 ms 14.104 ms 7
unknown.Level3.net (209.247.9.173) 14.227 ms 17.553 ms 15.415 ms "PassGuide" -
8 so-0-1-0.bbr1.NewYork1.level3.net (64.159.1.41) 17.063 ms 20.960 ms 19.512 ms 9
so-7-0-0.gar1. NewYork1.Level3.net (64.159.1.182) 20.334 ms 19.440 ms 17.938 ms
10 so-4-0-0.edge1.NewYork1.Level3.
net (209.244.17.74) 27.526 ms 18.317 ms 21.202 ms 11 uunet-level3-
oc48.NewYork1.Level3.net
(209.244.160.12) 21.411 ms 19.133 ms 18.830 ms 12 0.so-6-0-0.XL1.NYC4.ALTER.NET
(152.63.21.78)
21.203 ms 22.670 ms 20.111 ms 13 0.so-2-0-0.TL1.NYC8.ALTER.NET (152.63.0.153)
30.929 ms 24.858 ms
23.108 ms 14 0.so-4-1-0.TL1.ATL5.ALTER.NET (152.63.10.129) 37.894 ms 33.244 ms
33.910 ms 15 0.so-7-0-0.XL1.MIA4.ALTER.NET (152.63.86.189) 51.165 ms 49.935 ms
49.466 ms 16 0.so-3-0-0.XR1.MIA4.ALTER.
NET (152.63.101.41) 50.937 ms 49.005 ms 51.055 ms 17 117.ATM6-
0.GW5.MIA1.ALTER.NET (152.63.82.73) 51.897 ms 50.280 ms 53.647 ms 18 passguidegw1.
customer.alter.net (65.195.239.14) 51.921 ms 51.571 ms 56.855 ms 19
www.passguide.com (65.195.239.22) 52.191 ms 52.571 ms 56.855 ms 20
www.passguide.com (65.195.239.22) 53.561 ms 54.121 ms 58.333 ms
Which of the following is the most like cause of this issue?
You are concerned about outside attackers penetrating your network via your company Web server. You wish to place your Web server between two firewalls. One firewall between the Web server and the outside world. The other between the Web server and your network. What is this called?
Which of the following proxy servers is also referred to as transparent proxies or forced proxies?
Which of the following tools allows an attacker to intentionally craft the packets to gain unauthorized access?
Each correct answer represents a complete solution. Choose two.
Which of the following activities will you use to retrieve user names, and info on groups, shares, and services of networked computers?
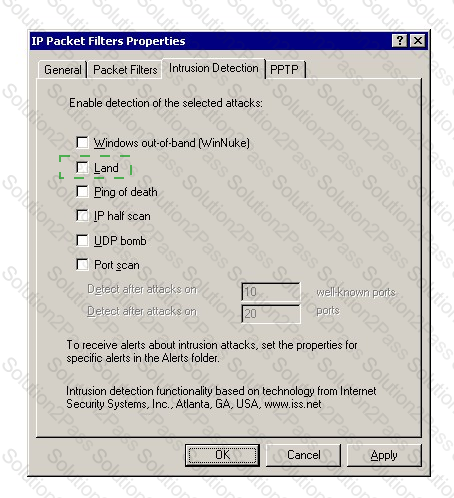
You work as a Network Administrator for McRobert Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) Server 2000. You are configuring intrusion detection on the server. You want to get notified when a TCP SYN packet is sent with a spoofed source IP address and port number that match the destination IP address and port number. Mark the alert that you will enable on the Intrusion Detection tab page of the IP Packet Filters Properties dialog box to accomplish the task.
Which of the following tools are used to determine the hop counts of an IP packet?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. According to the company's security policy, you apply Windows firewall setting to the computers on the network. Now, you are troubleshooting a connectivity problem that might be caused by Windows firewall. What will you do to identify connections that Windows firewall allows or blocks?
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
Which of the following are default ports for the FTP service?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. A firewall has been configured on the network. You configure a filter on the router. You verify that SMTP operations have stopped after the recent configuration. Which of the following ports will you have to open on the router to resolve the issue?
John works as a Professional Ethical Hacker for NetPerfect Inc. The company has a Linux-based network. All client computers are running on Red Hat 7.0 Linux. The Sales Manager of the company complains to John that his system contains an unknown package named as tar.gz and his documents are exploited. To resolve the problem, John uses a Port scanner to enquire about the open ports and finds out that the HTTP server service port on 27374 is open. He suspects that the other computers on the network are also facing the same problem. John discovers that a malicious application is using the synscan tool to randomly generate IP addresses. Which of the following worms has attacked the computer?
Which of the following work as traffic monitoring tools in the Linux operating system?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. Active Directory integrated zone has been configured on the network. You want to create a text file that lists the resource records of a specified zone for your record. Which of the following commands will you use to accomplish the task?
Adam works as a professional Computer Hacking Forensic Investigator. He wants to investigate a suspicious email that is sent using a Microsoft Exchange server. Which of the following files will he review to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.