GCIH GIAC Certified Incident Handler Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GCIH GIAC Certified Incident Handler certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following attacks saturates network resources and disrupts services to a specific computer?
Which of the following refers to a condition in which a hacker sends a bunch of packets that leave TCP ports half open?
Which of the following types of skills are required in the members of an incident handling team?
Each correct answer represents a complete solution. Choose all that apply.
John works as a Network Security Professional. He is assigned a project to test the security of
www.we-are-secure.com. He establishes a connection to a target host running a Web service with netcat and sends a bad html request in order to retrieve information about the service on the host.
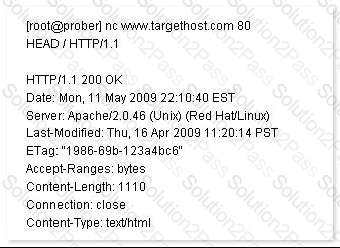
Which of the following attacks is John using?
Which of the following applications is NOT used for passive OS fingerprinting?
Which of the following statements about threats are true?
Each correct answer represents a complete solution. Choose all that apply.
Fill in the blank with the appropriate term.
______ is a technique used to make sure that incoming packets are actually from the networks that they claim to be from.
Which of the following statements are correct about spoofing and session hijacking?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following procedures is designed to enable security personnel to identify, mitigate, and recover from malicious computer incidents, such as unauthorized access to a system or data, denialof-service, or unauthorized changes to system hardware, software, or data?
Which of the following attacks capture the secret value like a hash and reuse it later to gain access to a system without ever decrypting or decoding the hash?
Which of the following is the method of hiding data within another media type such as graphic or document?
You want to connect to your friend's computer and run a Trojan on it. Which of the following tools will you use to accomplish the task?
Which of the following would allow you to automatically close connections or restart a server or service when a DoS attack is detected?
You work as a System Administrator in SunSoft Inc. You are running a virtual machine on Windows Server 2003. The virtual machine is protected by DPM. Now, you want to move the virtual machine to another host. Which of the following steps can you use to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following are open-source vulnerability scanners?
Which of the following reads and writes data across network connections by using the TCP/IP protocol?
Which of the following attacks can be overcome by applying cryptography?
Victor works as a professional Ethical Hacker for SecureEnet Inc. He has been assigned a job to test an image, in which some secret information is hidden, using Steganography. Victor performs the following techniques to accomplish the task:
1. Smoothening and decreasing contrast by averaging the pixels of the area where significant color transitions occurs.
2. Reducing noise by adjusting color and averaging pixel value.
3. Sharpening, Rotating, Resampling, and Softening the image.
Which of the following Steganography attacks is Victor using?
Which of the following statements about reconnaissance is true?
Your friend plans to install a Trojan on your computer. He knows that if he gives you a new version of chess.exe, you will definitely install the game on your computer. He picks up a Trojan and joins it with chess.exe. Which of the following tools are required in such a scenario?
Each correct answer represents a part of the solution. Choose three.
