GSSP-.NET GIAC GIAC Secure Software Programmer - C#.NET Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSSP-.NET GIAC GIAC Secure Software Programmer - C#.NET certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following syntaxes is used for the EncryptionAlgorithm property of the Message class?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a class library using the .NET Framework. The library will be used to open the NSCs of computers. Later, you will set up the class library to the GAC and provide it Full Trust permission. You write down the following code segments for the socket connections:
SocketPermission permission = new SocketPermission(PermissionState.Unrestricted);
permission.Assert();
A number of the applications that use the class library may not have the necessary permissions to open the network socket connections. Therefore, you are required to withdraw the assertion. Which of the following code segments will you use to accomplish the task?
Patrick works as a Software Developer for GenTech Inc. He develops an application, named App1, using Visual C# .NET. He implements security using the security classes of the .NET Framework. He defines the following statements in the application:
PrincipalPermission Principal_Perm1 = new PrincipalPermission("Nick", "General
Manager");
PrincipalPermission Principal_Perm2 = new PrincipalPermission("Jack", "Accountant");
Patrick wants to check whether all demands that succeed for Principal_Perm1 also succeed for Principal_Perm2. Which of the following methods of the PrincipalPermission class will he use to accomplish this?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You are creating an application using the .NET Framework. You write the following code snippet to call a method from the Win32 API by using PInvoke:
int rst = MessageBox(hWd, Mytext, Mycaption, Mytype);
You are required define a method prototype. Which of the following code segments will you use to accomplish this task?
Which of the following is not a method of controlling traffic through a firewall?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating a Windows Forms application using .NET Framework 3.5. You need to develop a new control for the application. You must ensure that the control inherits the TreeView control by adding a custom node tag and a highlight color. What will you do?
Which of the following security methods is used when the code requires a specific set of permissions, which are not known until runtime?
Henry works as a Software Developer for SoftTech Inc. He creates a Windows form named
MyForm1. The form contains detailed information about a student. The form uses a ListBox control named ListBox1 that concatenates two strings displayed in two TextBox controls. Henry wants a method to return a value for the control. Which of the following options will he consider while creating a method for the control?
Which of the following modifiers in C# will you use if you do NOT want a custom-build component to be a base class?
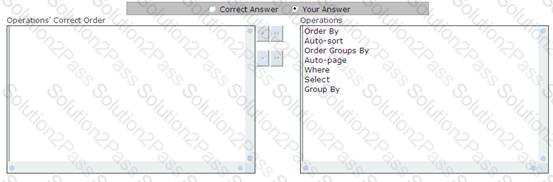
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. The application contains a data-bound control. You use the LinqDataSource control to use LINQ in the ASP.NET application by setting properties in markup text. The LinqDataSource control uses LINQ to SQL to automatically generate the data commands. You are required to perform data operations by using the LinqDataSource control. What is the correct order in which data operations are applied?
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its application development platform. He creates an application using .NET Framework. He wants to encrypt all his e-mails that he sends to anyone. Which of the following will he use to accomplish the task?
You work as a Software Developer for ManSoft Inc. You use Microsoft Visual Studio to create a Web service named MyWebService. You create a SOAP message that is not secure in the Web service. You want to use the SendSecurityFilter class in the Web service to handle the transmission and securing of SOAP messages. Which of the following code segments will you use to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
In which of the following objects are session variables stored?
Which of the following algorithms supports key lengths from 128 bits to 192 bits in increments of 64 bits?
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. Allen creates an application that will be used to handle security information related to the company. He wants to secure the application by using the most secure authentication method. The method should have a strong key for encryption and send the encrypted password across the network. Which of the following authentication methods will Allen use to accomplish the task?
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to attach the Visual Studio Debugger to Internet Explorer when the application is running. Which of the following steps will you take to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create a Web service using the .NET Framework 2.0. You call a method in the Web service. The following exception is thrown in the Web service: client.System.Web.Services.Protocols.SoapException: Server was unable to process request. System.NullReferenceException: Object reference not set to an instance of an object. You find out that it is the following line of code that throws the exception: if (Session ["StoredValue"] == null)
You must ensure that the method runs without throwing any exception. What will you do to accomplish this task?
You work as a Software Developer for Webtech Inc. You plan to migrate the existing Active Server Pages (ASP) pages to ASP.NET Web pages in order to implement rich functionalities of a Web browser in your Web pages. Therefore, you want to add controls to Web pages of your existing application named WebApp1. Which of the following controls will be most suitable to implement?
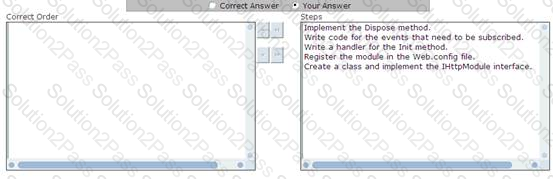
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. You want to use a HTTP module called on each and every request made by the application. It is called as part of the ASP.NET request pipeline. It has right to access life-cycle events throughout the request. You also want to ensure that the HTTP module allows a user to inspect incoming and outgoing requests and take appropriate action based on the request. What will be the correct order to create the HTTP module?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You have recently finished development of a Windows application using .NET Framework. Users report that the application is not running properly. When the users try to complete a particular action, the following error message comes out:
Unable to find assembly 'myservices, Version=1.0.0.0, Culture=neutral,
PublicKeyToken=29b5ad26c9de9b95'.
You notice that the error occurs as soon as the application tries to call functionality in a serviced component that was registered by using the following command:
regsvcs.exe myservices.dll
You must make sure that the application can call the functionality in the serviced component with no exceptions being thrown. What will you do to accomplish this task?
