HPE6-A79 HP Aruba Certified Mobility Expert Written Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your HP HPE6-A79 Aruba Certified Mobility Expert Written Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A network administrator has racked up a 7210 Mobility Controller (MC) that will be terminating 200+ Aps on a medium-size branch office. Next, the technician cabled the appliance with 4SPF+ Direct Attached Cables (DACs) distributed between two-member switching stack and powered it up.
What must the administrator do next in the MCs to assure maximum wired bandwidth utilization?
Refer to the exhibits.
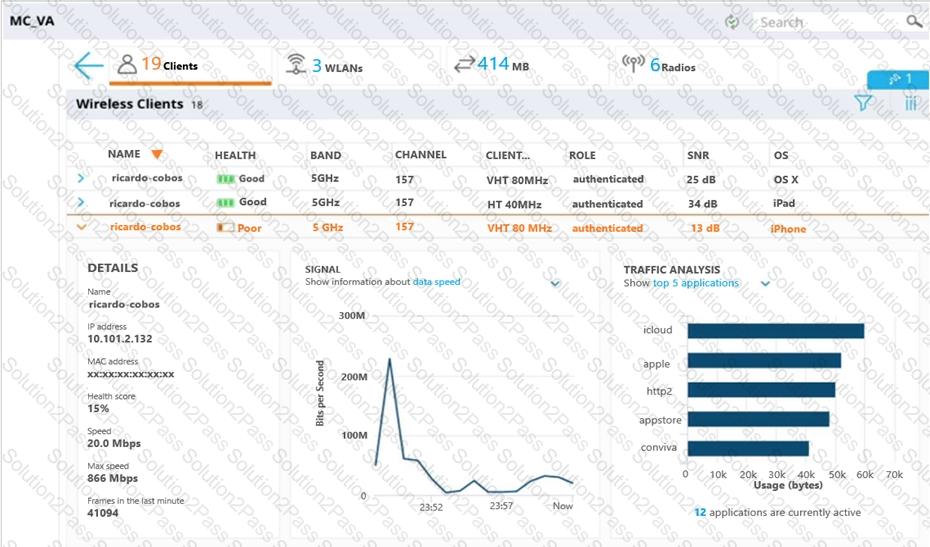
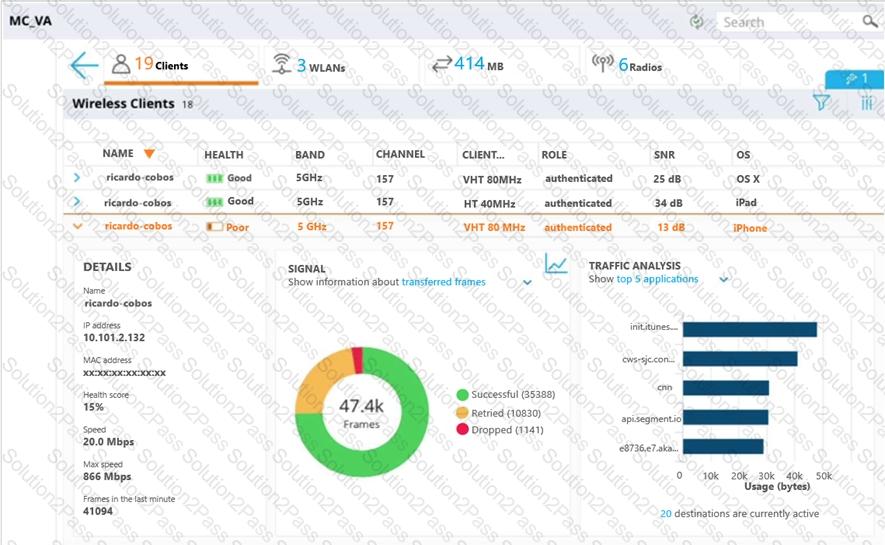
A user reports slow response time to a network administrator and suggests that there might be a problem with the WLAN. The user’s phone supports 802.11ac in the 5 GHz band. The network administrator finds the user in the Mobility Master (MM) and reviews the output shown in the exhibit.
What can the network administrator conclude after analyzing the data?
Refer to the exhibit.
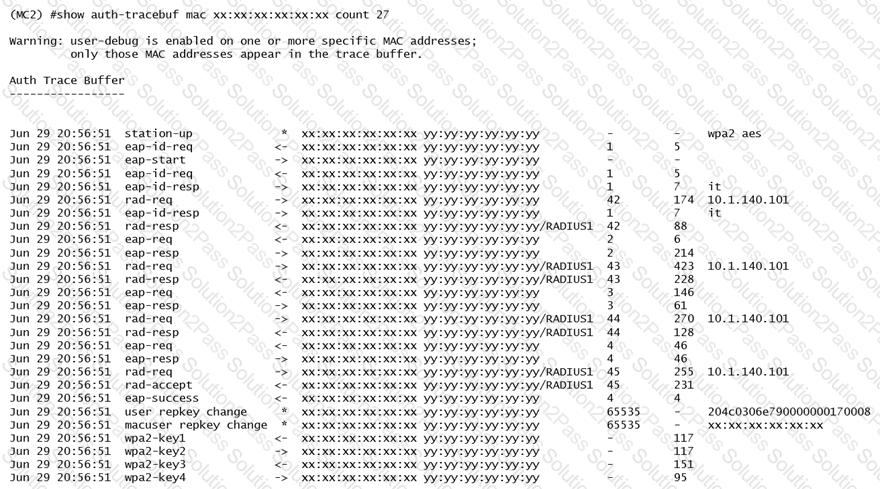
A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by a wireless station?
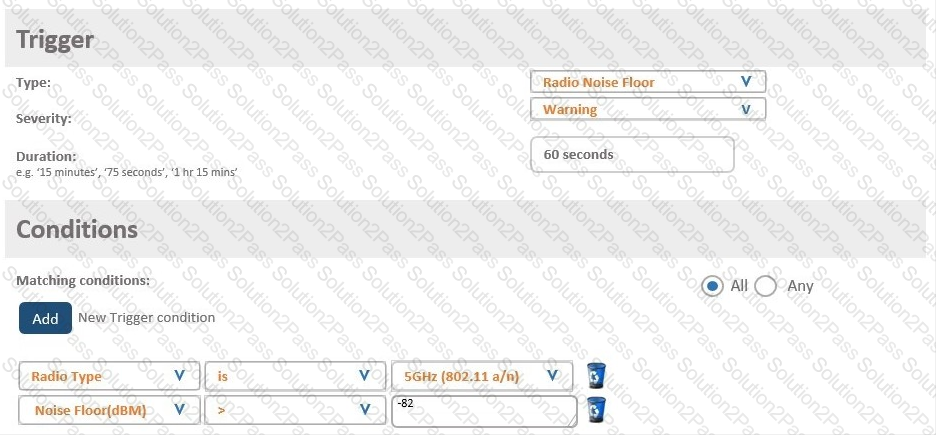
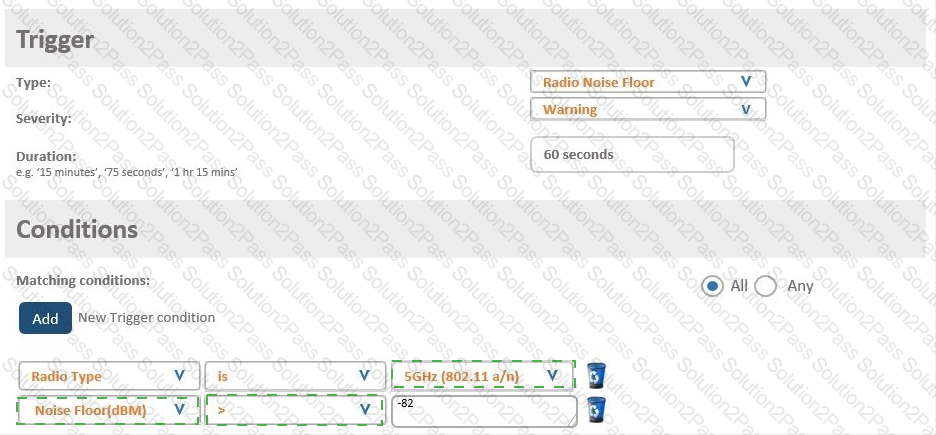
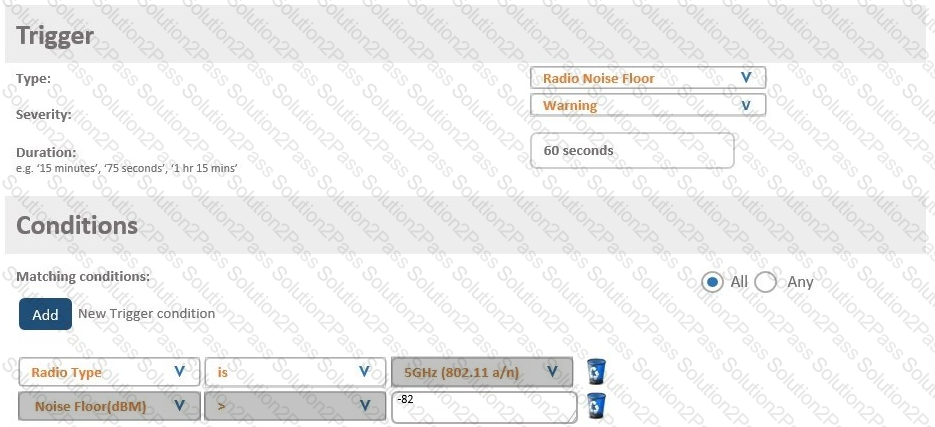
A network administrator wants to receive a warning level alarm every time the noise floor rises above -82 dBm on any of the AP radios.
Which alarm definition must the network administrator create to accomplish this?
An organization wants to deploy a WLAN infrastructure that provides connectivity to these client categories:
• Employees
• Contractors
• Guest users
• Corporate IoT legacy devices that support no authentication or encryption
Employees and contractors must authenticate with company credentials and get network access based on AD group membership. Guest users are required to authenticate with captive portal using predefined credentials. Only employees will run L2 encryption.
Which implementation plan fulfills the requirements while maximizing the channel usage?
Refer to the exhibit.
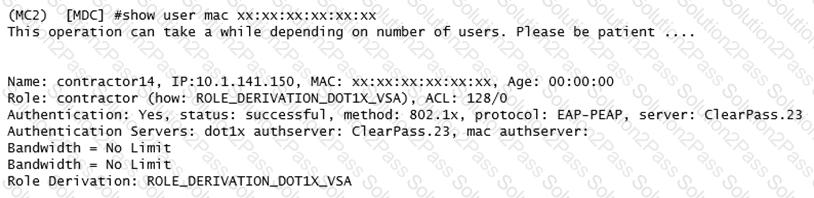
A network administrator is evaluating a deployment to validate that a user is assigned the proper role and reviews the output in the exhibit. How is the role assigned to user?
A network administrator is in charge of a Mobility Master (MM) – Mobility Controller (MC) based network security. Recently the Air Monitors detected a Rogue AP in the network and the administrator wants to enable “Tarpit” based wireless containment.
What profile must the administrator enable “tarpit” wireless containment on?
Refer to the exhibit.

The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?
A joint venture between two companies results in a fully functional WLAN Aruba solution. The network administrator uses the following script to integrate the WLAN solution with two radius servers, radius1 and radius2.
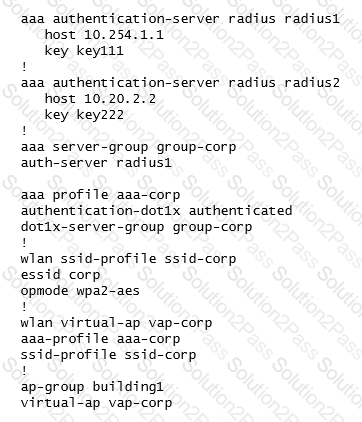
While all users authenticate with username@domainname.com type of credentials, radius1 has user accounts with the domain name portion.
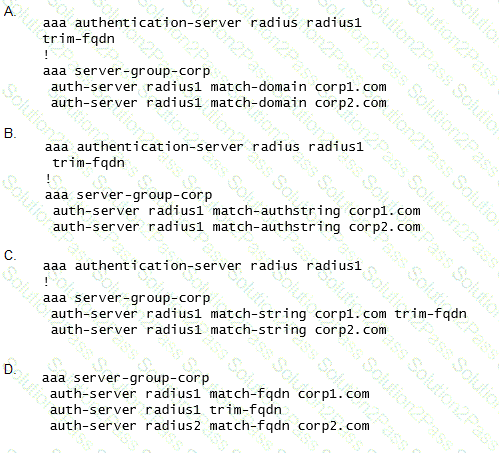
Which additional configuration is required to authenticate corp1.com users with radius1 and corp2 users with radius2?
Refer to the exhibit.
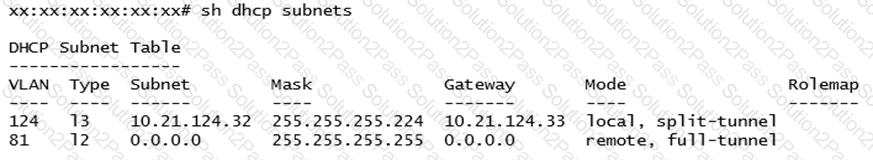
A network engineer deploys two different DHCP pools in an Instant AP (IAP) cluster for WLANs that will have connectivity to a remote site using Aruba IPSec.
Based on the output shown in the exhibit, which IAP-VPN DHCP modes are being used?
Refer to the exhibit.
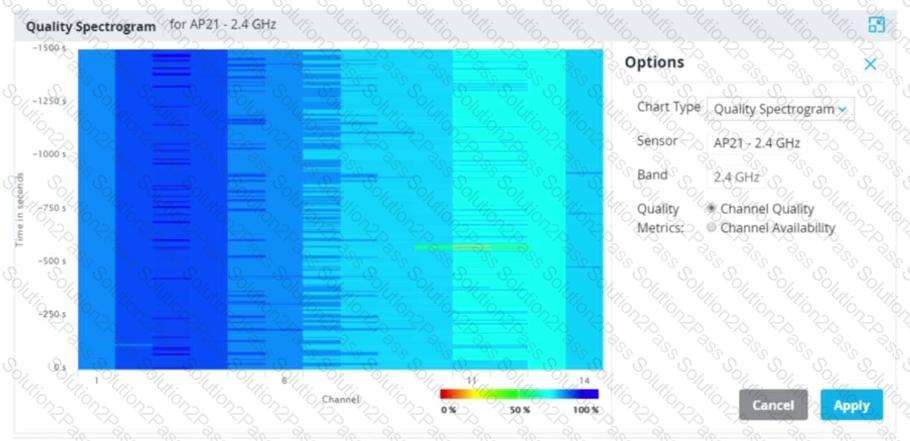
Based on the output shown in the exhibit, which channel offers the highest quality?
Refer to the exhibit.
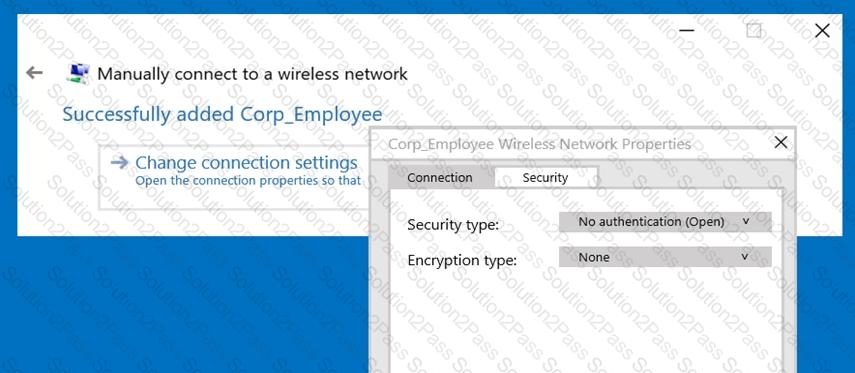
A network administrator wants to configure an 802.1x supplicant for a wireless network that includes the following:
• AES encryption
• EAP-MSCHAP v2-based user and machine authentication
• Validation of server certificate in Microsoft Windows 10
The network administrator creates a WLAN profile and selects the change connection settings option. Then the network administrator changes the security type to Microsoft: Protected EAP (PEAP), and enables user and machine authentication under Additional Settings.
What must the network administrator do next to accomplish the task?
Refer to the exhibit.
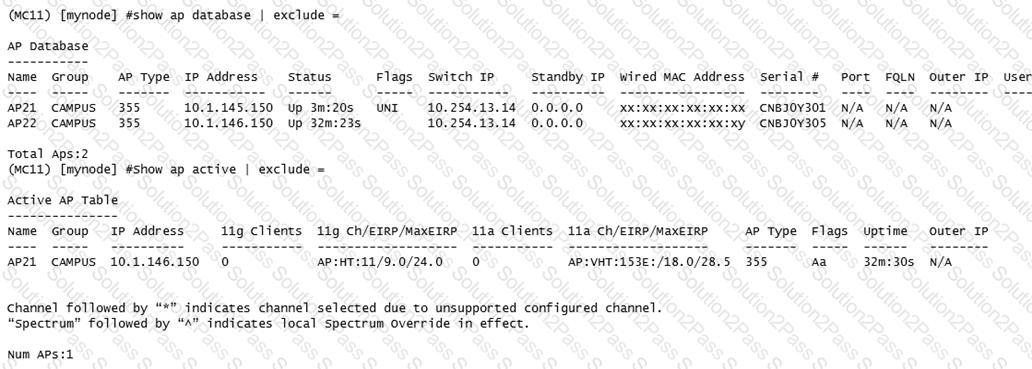
A network administrator deploys a new Mobility Master (MM) - Mobility Controller (MC) network. To test the solution, the network administrator accesses the console of a pair of APs and statically provisions them. However, one of the APs does not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit.
Which actions must the network administrator take to solve the problem?
Refer to the exhibit.
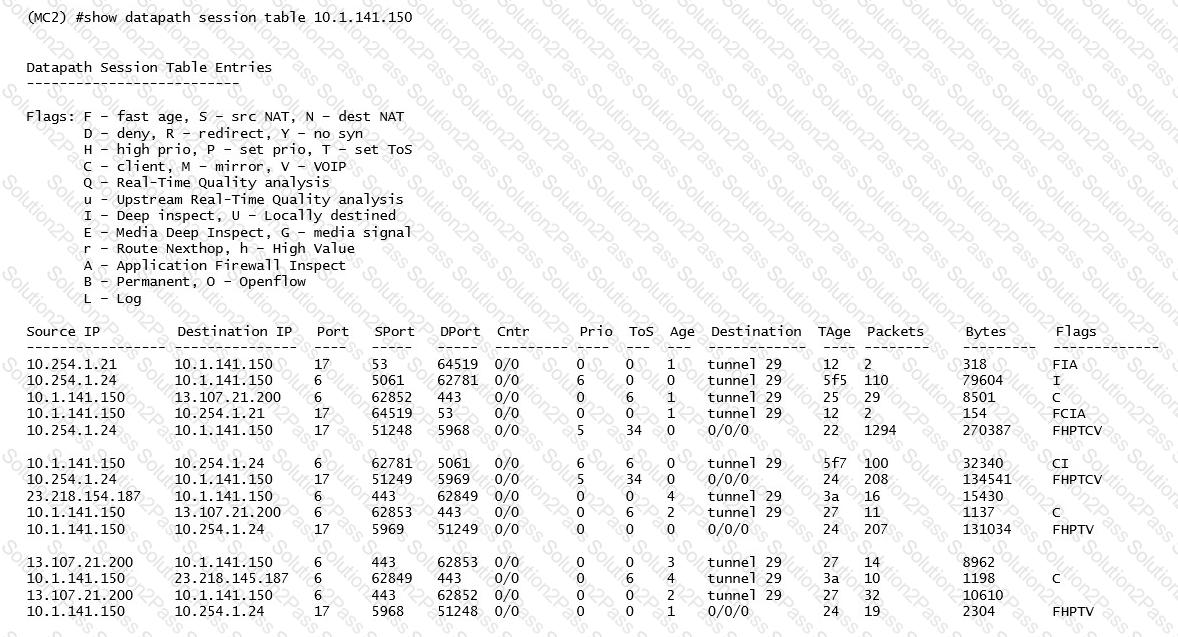
A network administrator deploys DSCP based prioritization in the entire wired network to improve voice quality for a SIP-based IP telephony system used by the company. However, users report that calls they make from WLAN have poor audio quality, while desktop phones do not experience the same problem. The network administrator makes a test call and looks in the datapath session table.
Based on the output shown in the exhibit, what is one area that the network administrator should focus on?
A company with 535 users deploys an Aruba solution with more than 1000 Aruba APs, two 7220 Mobility Controllers, and a single Mobility Master (MM) virtual appliance at the campus server farm. The MCs run a HA Fast failover group in dual mode and operate at 50% AP capacity.
If there is an MM or MC failure, the network administrator must ensure that the network is fully manageable and the MC load does not exceed 80%.
What can the network administrator do to meet these requirements?
Refer to the exhibit.
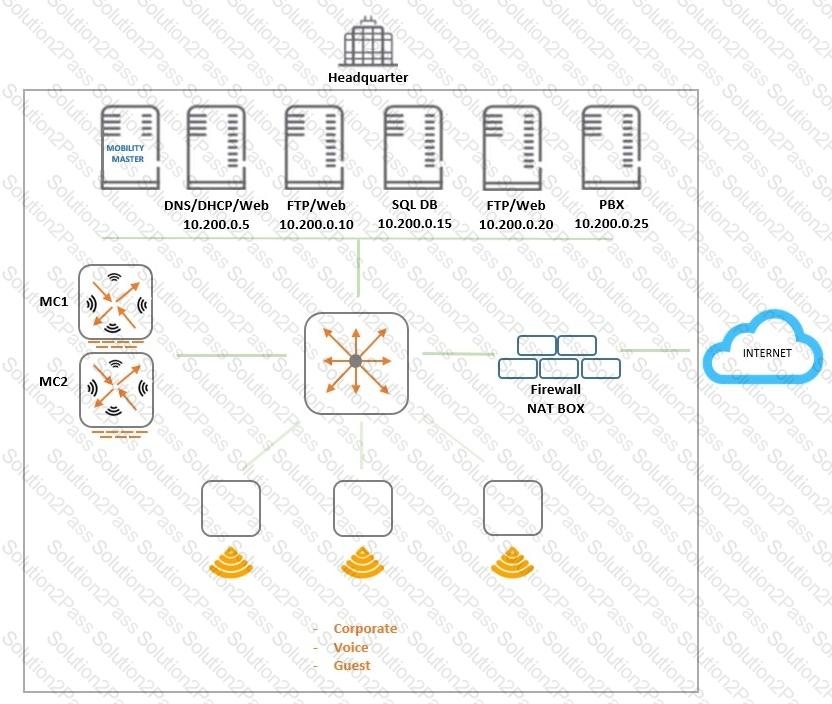
An organization provides WiFi access through a corporate SSID with an Aruba Mobility Master (MM) - Mobility Controller (MC) network that includes PEF functions. The organization wants to have a single firewall policy configured and applied to the employee role.
This policy must allow users to reach Web, FTP, and DNS services, as shown in the exhibit. Other services should be exclusive to other roles. The client NICs should receive IP settings dynamically.
Which policy design meets the organization’s requirements while minimizing the number of policy rules?
 Graphical user interface, application
Description automatically generated
Graphical user interface, application
Description automatically generated