Vault-Associate HashiCorp Certified: Vault Associate (002) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your HashiCorp Vault-Associate HashiCorp Certified: Vault Associate (002) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
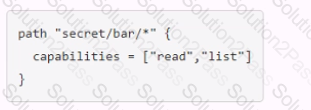
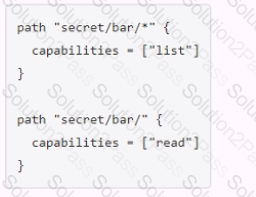
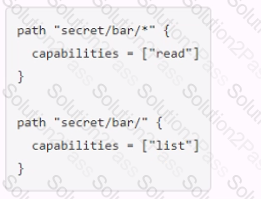
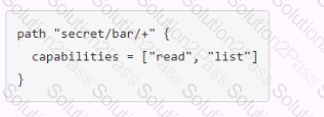
You have been tasked with writing a policy that will allow read permissions for all secrets at path secret/bar. The users that are assigned this policy should also be able to list the secrets. What should this policy look like?
What environment variable overrides the CLI's default Vault server address?
What are orphan tokens?
Your DevOps team would like to provision VMs in GCP via a CICD pipeline. They would like to integrate Vault to protect the credentials used by the tool. Which secrets engine would you recommend?
How many Shamir's key shares are required to unseal a Vault instance?
Examine the command below. Output has been trimmed.
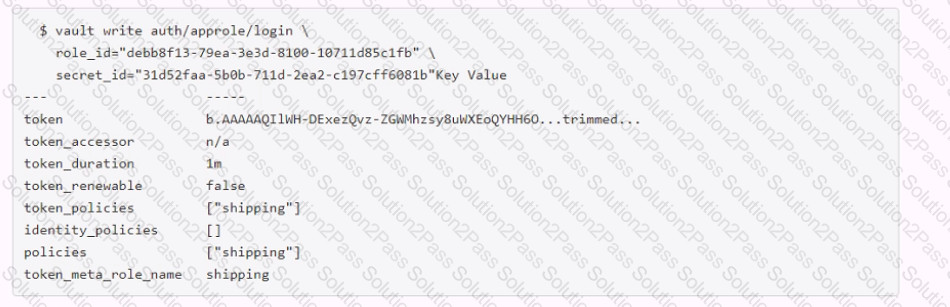
Which of the following statements describe the command and its output?
Which of the following statements describe the secrets engine in Vault? Choose three correct answers.
When an auth method is disabled all users authenticated via that method lose access.
Which of the following describes the Vault's auth method component?
Security requirements demand that no secrets appear in the shell history. Which command does not meet this requirement?
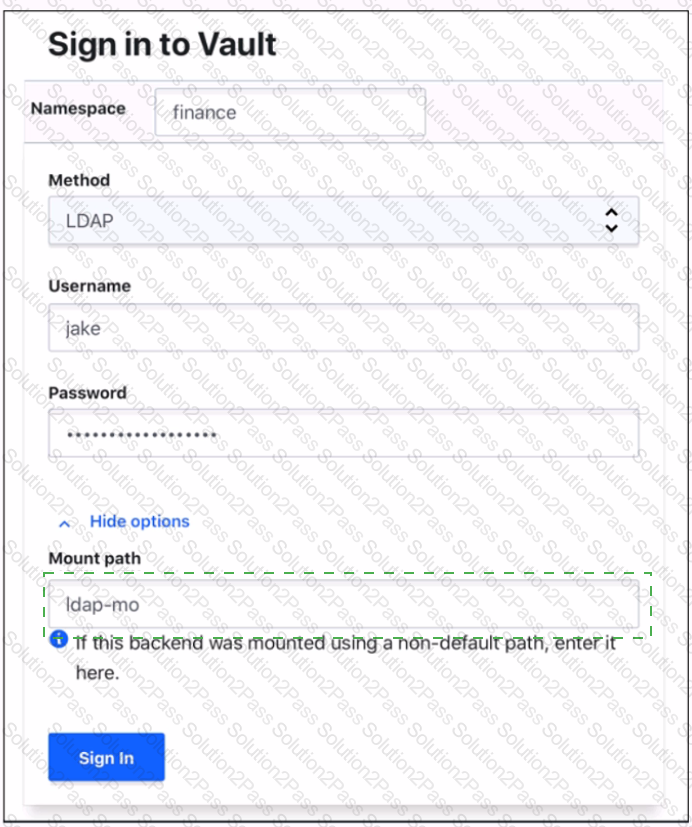
Where do you define the Namespace to log into using the Vault Ul?
To answer this question
Use your mouse to click on the screenshot in the location described above. An arrow indicator will mark where you have clicked. Click the "Answer" button once you have positioned the arrow to answer the question. You may need to scroll down to see the entire screenshot.
Where does the Vault Agent store its cache?
Which Vault secret engine may be used to build your own internal certificate authority?
You are performing a high number of authentications in a short amount of time. You're experiencing slow throughput for token generation. How would you solve this problem?
A web application uses Vault's transit secrets engine to encrypt data in-transit. If an attacker intercepts the data in transit which of the following statements are true? Choose two correct answers.
The Vault encryption key is stored in Vault's backend storage.
An authentication method should be selected for a use case based on: