H12-722 Huawei Certified ICT Professional - Constructing Service Security Network (HCIP-Security-CSSN V3.0) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Huawei H12-722 Huawei Certified ICT Professional - Constructing Service Security Network (HCIP-Security-CSSN V3.0) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
The user needs of a university are as follows:
1. The environment is large, and the total number of two-way traffic can reach 800M. Huawei USG6000 series firewall is deployed at its network node.
2. The intranet is divided into student area, server area, etc., users are most concerned about the security of the server area to avoid attacks from various threats.
3. At the same time, some pornographic websites in the student area are prohibited.
The external network has been configured as an untrust zone and the internal network has been configured as a trust zone on the firewall. How to configure the firewall to meet the above requirements?
155955cc-666171a2-20fac832-0c042c0415
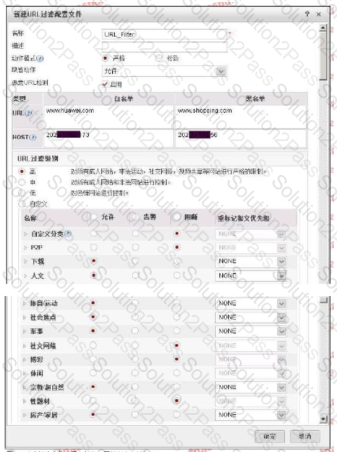
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
Huawei NIP6000 products have zero-setting network parameters and plug-and-play functions, because the interfaces and interface pairs only work on layer 2 without
Set the IP address.
A True
B. False
Which of the following options is not a defense against HTTP Flood attacks?
Which of the following behaviors is a false positive of the intrusion detection system?
Which of the following options belong to the network layer attack of the TCP/IP protocol stack? (multiple choice)
Regarding the description of keywords, which of the following is correct? (multiple choice)
The most common form of child-like attack is to send a large number of seemingly legitimate packets to the target host through Flood, which ultimately leads to network bandwidth.
Or the equipment resources are exhausted. Which of the following options is not included in traffic attack packets?
After the user deploys the firewall anti-virus strategy, there is no need to deploy anti-virus software
Which of the following options are correct for the configuration description of the management center ATIC? (multiple choice)
The administrator has made the following configuration:
1. The signature set Protect_ all includes the signature ID3000, and the overall action of the signature set is to block.
2. The action of overwriting signature ID3000 is an alarm.
For the URL is htpt://www.abcd. com:8080/news/education. aspx?name=tom &age=20, which option is path?
UDP is a connectionless protocol. UDP Flood attacks that change sources and ports will cause performance degradation of network devices that rely on session forwarding.
Even the session table is exhausted, causing the network to be paralyzed. Which of the following options is not a preventive measure for UDP Flood attacks?
Regarding the description of intrusion detection technology, which of the following statements is correct?
Misuse detection is through the detection of similar intrusions in user behavior, or those that use system flaws to indirectly violate system security rules
To detect intrusions in the system. Which of the following is not a feature of misuse detection 2
Which of the following technologies can achieve content security? (multiple choice)
In the Huawei USG6000 product, after creating or modifying the security configuration file, the configuration content will not take effect immediately: you need to click the "Prompt" in the upper right corner of the interface.
"Hand in" to activate.
Which of the following options is correct for the sequence of the flow-by-stream detection of AntiDDoS?
1. The Netflow analysis device samples the current network flow;
2. Send a drainage command to the cleaning center;
3. Discover the DDoS attack stream;
4.Netior: analysis equipment sends alarms to ATIC management center
5. The abnormal flow is diverted to the cleaning center for further inspection and cleaning;
6. The cleaning center sends the host route of the attacked target IF address server to the router to achieve drainage
7. The cleaning log is sent to the management center to generate a report;
8. The cleaned traffic is sent to the original destination server.
Regarding the processing process of file overwhelming, which of the following statements is correct?
Configure the following commands on the Huawei firewall:
[USG] interface G0/0/1
[USG] ip urpf loose allow-defult-route acl 3000
Which of the following options are correct? (multiple choice)
