H12-724 Huawei HCIP-Security (Fast track) V1.0 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Huawei H12-724 HCIP-Security (Fast track) V1.0 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
The use of the 802.1X authentication scheme generally requires the terminal to install specific client software. For large-scale deployment of client software, the methods that can be taken. What are the cases? (multiple choices)
Visitors refer to users who need temporary access to the network at a specific location.
According to the user’s access5W1H Conditions determine access rights andQoS Strategy for5W1Ho[Which of the following descriptions are correct? (Multiple choice)
Regarding the description of intrusion detection technology, which of the following statements is correct?
The administrator has configured file filtering to prohibit internal employees from uploading development files, but internal employees can still upload development files. Which of the following is not allowed Can the reason?
If you are deploying BYOD When the system is installed, use a stand-alone installation SM, Dual-machine installation SC, Stand-alone hardware deployment AE,Which of the following descriptions are correct? (Multiple choice)
Typical application scenarios of terminal security include: Desktop management, illegal outreach and computer peripheral management.
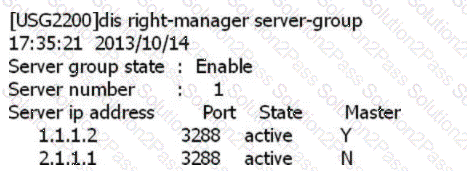
SACG query right-manager information as follows, which options are correct? (Select 2 answers)
Visitors can access the network through their registered account. Which of the following is not an account approval method?
SQI Server2005 may not be properly installed, which of the following may be the possible reasons?
In the park, users frequently enter and leave the wireless signal coverage area due to office needs. If you need to ensure the user's Internet experience, after the user passes an authentication, when he accesses the network again, no important authentication is required:Which of the following authentication methods is recommended?
Sort all services according to user group and account: By the end IP The address range is time-sharing, if it is a user group, a small terminal with an account IP Address range allocation for the same business(Chen Gongji outside business) I The business assigned to the one with the highest priority will take effect.
Which of the following is correct regarding the order of priority?
Using Agile Controller-Campus for visitor management, users can obtain the account they applied for in a variety of ways, but which of the following are not included A way?
According to different reliability requirements, centralized networking can provide different reliability networking solutions. Regarding these solutions, which of the following descriptions are correct? (Multiple choice)
Regarding the description of the security zone in the Agile Controller-Campus, which of the following options are correct? (multiple choice)
For special message attacks, which of the following option descriptions is correct?
A Special control packet attack is a potential attack and does not have direct destructive behavior
B. The attacker probes the network structure by sending special control messages to launch a real attack.
C. Special control message attacks do not have the ability to detect the network structure. Only scanning attacks can detect the network.
D. Special control message items can only use ICMP to construct attack messages.
The most common form of child-like attack is to send a large number of seemingly legitimate packets to the target host through Flood, which ultimately leads to network bandwidth.
Or the equipment resources are exhausted. Which of the following options is not included in traffic attack packets?
Which of the following options is Agile Controller-Campus middle SC The main function of the component?
An enterprise administrator configures a Web reputation website in the form of a domain name, and configures the domain name as www. abc; example. com. .
Which of the following is the entry that the firewall will match when looking up the website URL?
Regarding firewall and IDS, which of the following statements is correct?
