H12-725_V4.0 Huawei HCIP-Security V4.0 Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Huawei H12-725_V4.0 HCIP-Security V4.0 Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following statements is false about web rewriting in web proxy?
Huawei iMaster NCE-Campus is a web-based centralized management and control system in the CloudCampus Solution. It supports user access management and can function as multiple types of authentication servers. Which of the following servers can iMaster NCE-Campus not be used as?
Multiple links can be deployed at the egress of an enterprise network to improve network reliability.
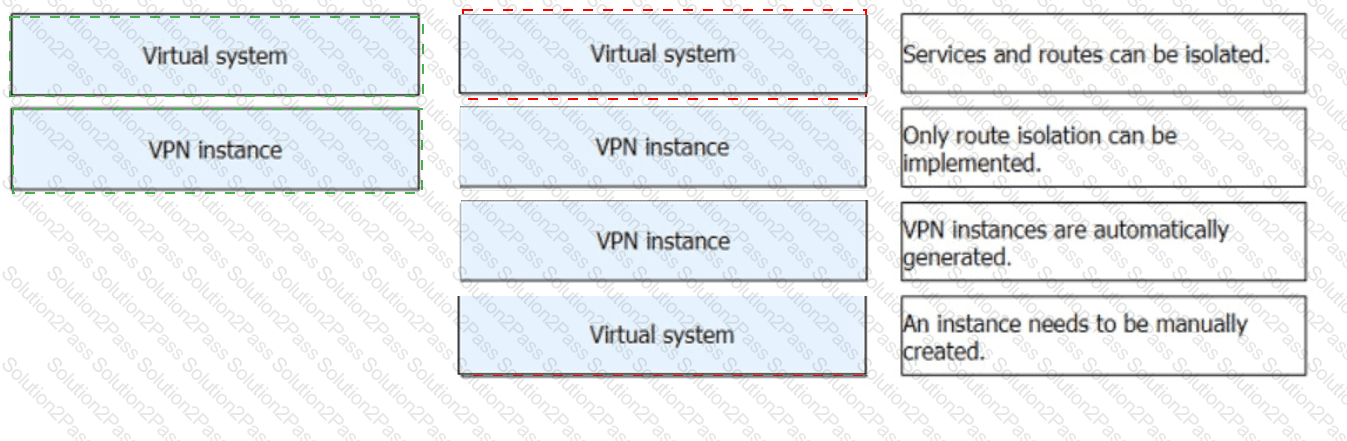
: 51 DRAG DROP
Match the description about virtual systems and VPN instances.

Which of the following statements is false about virtual system resource allocation?
Which of the following statements is true about the outgoing traffic in the firewall virtual system?
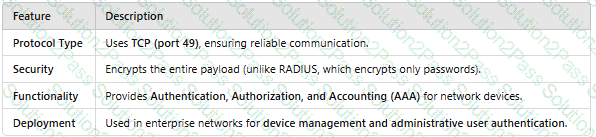
Which of the following statements is false about RADIUS and HWTACACS?
Which of the following methods are used by flood attacks to cause denial of services?(Select All that Apply)
If data filtering is configured on the firewall but is not correctly referenced in the security policy, the data that should be blocked can still be transmitted normally.
Which of the following conditions can be matched by PBR?(Select All that Apply)
Which of the following is the function of Message 1 and Message 2 during IKEv1 phase-1 negotiation in main mode?
The Common Vulnerability Scoring System (CVSS) is a widely used open standard for vulnerability scoring. It uses a modular scoring system. Which of the following is not included in the CVSS?
HWTACACS is a centralized information exchange protocol based on the client/server structure. It uses UDP for transmission and performs authentication, authorization, and accounting for users accessing the Internet through Point-to-Point Protocol (PPP) or Virtual Private Dial-up Network (VPDN) and administrative users logging in to devices.
Which of the following statements is false about hot standby networking?(Select All that Apply)
Which of the following statements is false about health check?
Network Access Control (NAC) is an end-to-end security control technology that works in combination with AAA to implement access authentication. Which of the following statements about NAC and AAA are true?(Select All that Apply)
When an IPsec VPN is established in aggressive mode, AH+ESP can be used to encapsulate packets in NAT traversal scenarios.
Which of the following actions can be performed when the firewall identifies file anomalies?(Select All that Apply)
 A screenshot of a computer
AI-generated content may be incorrect.
A screenshot of a computer
AI-generated content may be incorrect.