JN0-214 Juniper Cloud Associate (JNCIA-Cloud) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Juniper JN0-214 Cloud Associate (JNCIA-Cloud) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the role of overlay tunnels in an overlay software-defined networking (SDN) solution?
Click to the Exhibit button.
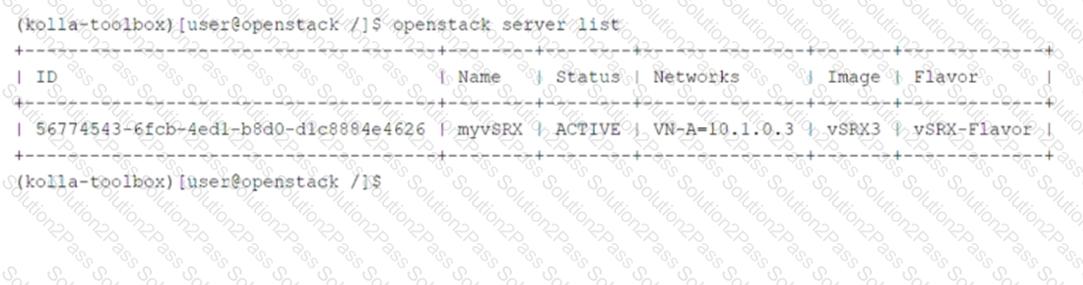
Referring to the exhibit, which two statements are correct? (Choose two.)
Which type of virtualization provides containerization and uses a microservices architecture?
Which two tools are used to deploy a Kubernetes environment for testing and development purposes? (Choose two.)
Which OpenStack node runs the network agents?
What are two Kubernetes worker node components? (Choose two.)
You are asked to deploy a cloud solution for a customer that requires strict control over their resources and data. The deployment must allow the customer to implement and manage precise security controls to protect their data.
Which cloud deployment model should be used in this situation?
Which technology is used to run VMs in an OpenShift cluster?
Which two statements about containers are true? (Choose two.)
Click to the Exhibit button.
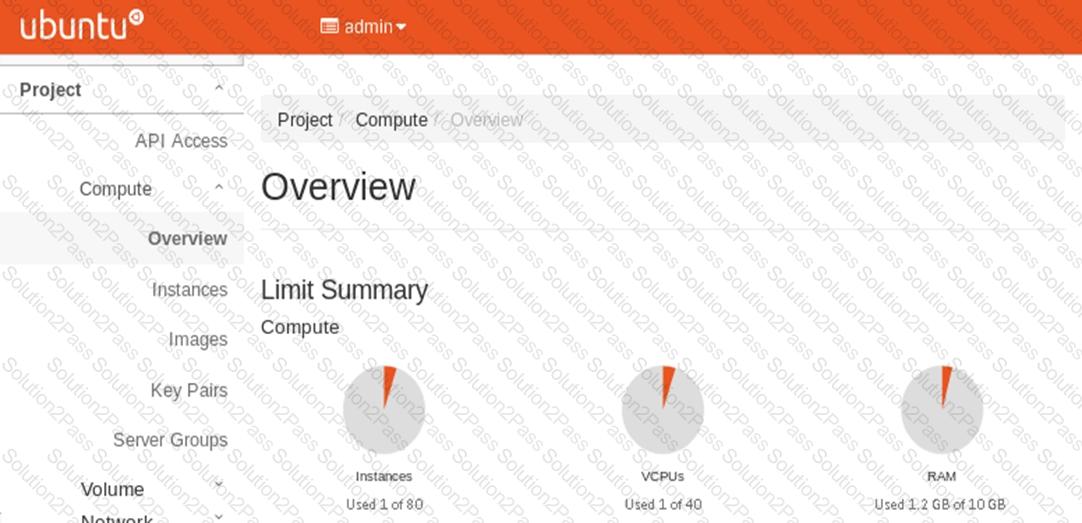
Referring to the exhibit, which OpenStack service provides the UI shown in the exhibit?
You are asked to deploy a Kubernetes application on your cluster. You want to ensure the application, and all of its required resources, can be deployed using a single package, with all install-related variables defined at start time.
Which tool should you use to accomplish this objective?
You must install a basic Kubernetes cluster.
Which tool would you use in this situation?
Click the Exhibit button.
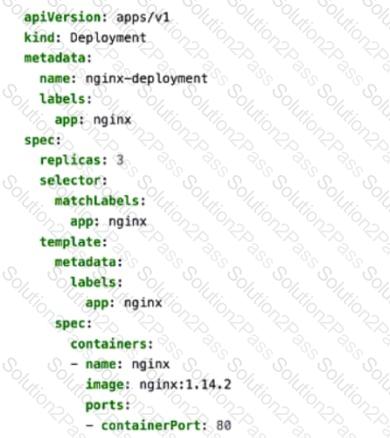
You apply the manifest file shown in the exhibit.
Which two statements are correct in this scenario? (Choose two.)
Which operating system must be used for control plane machines in Red Hat OpenShift?
Your organization manages all of its sales through the Salesforce CRM solution.
In this scenario, which cloud service model are they using?
Which encapsulation protocol uses tunneling to provide a Layer 2 overlay over an underlying Layer 3 network?
Which two statements are correct about the Kubernetes networking model? (Choose two.)
Which two statements are correct about Network Functions Virtualization (NFV)? (Choose two.)
Theopenstack user listcommand uses which OpenStack service?
